CyberheistNews Vol 9 #30
KnowBe4 Achieves Highest and Furthest Overall Position for Its Ability to Execute and Completeness of Vision in the 2019 Gartner Magic Quadrant for Security Awareness CBT 
We are excited to announce that KnowBe4 has achieved the highest and furthest overall position as a Leader for its ability to execute and completeness of vision in the 2019 Magic Quadrant for Security Awareness Computer-Based Training. This was the third consecutive year that we were recognized as a Leader in this Report.
We are very proud of this accomplishment.
We believe, as the world's largest security awareness training platform and a newly minted Unicorn due to our $1 billion valuation, this placement in the Leaders’ Quadrant validates our mission to enable employees to make smarter security decisions within client organizations has been successful using world-class training and simulated phishing to improve their security posture and mitigate risk.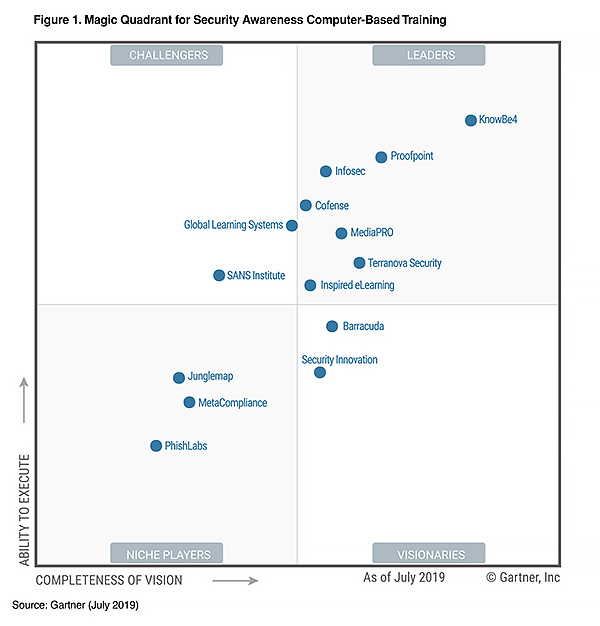
We attribute our position to the massive success we’ve had in developing new-school security awareness training and simulated phishing that shows real results in lowering an organization’s Phish-prone™ percentage.
Perry Carpenter, KnowBe4’s Chief Evangelist & Strategy Officer stated, “At KnowBe4, we consistently innovate our platform to bring our customers the absolute best-in-class content that they can utilize in their efforts to raise the level of security awareness in their organizations. We believe what sets KnowBe4 apart is our dedication to providing the highest level of customer service throughout the entire sales, onboarding and customer support processes."
A few things that always surprise people about the KnowBe4 platform is its ease-of-use regardless of an organization’s size, the shockingly affordable pricing, and the extremely-wide library of world-class content.
Read the Security Awareness CBT report to find out what we believe sets KnowBe4 apart.
Download Your Complimentary Copy of the Report Now!
https://info.knowbe4.com/gartner-magic-quadrant-security-awareness-cbt-chn
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose. This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from KnowBe4. Gartner Magic Quadrant for Security Awareness Computer-Based Training, Joanna G. Huisman, 18 July 2019

We are excited to announce that KnowBe4 has achieved the highest and furthest overall position as a Leader for its ability to execute and completeness of vision in the 2019 Magic Quadrant for Security Awareness Computer-Based Training. This was the third consecutive year that we were recognized as a Leader in this Report.
We are very proud of this accomplishment.
We believe, as the world's largest security awareness training platform and a newly minted Unicorn due to our $1 billion valuation, this placement in the Leaders’ Quadrant validates our mission to enable employees to make smarter security decisions within client organizations has been successful using world-class training and simulated phishing to improve their security posture and mitigate risk.

We attribute our position to the massive success we’ve had in developing new-school security awareness training and simulated phishing that shows real results in lowering an organization’s Phish-prone™ percentage.
Perry Carpenter, KnowBe4’s Chief Evangelist & Strategy Officer stated, “At KnowBe4, we consistently innovate our platform to bring our customers the absolute best-in-class content that they can utilize in their efforts to raise the level of security awareness in their organizations. We believe what sets KnowBe4 apart is our dedication to providing the highest level of customer service throughout the entire sales, onboarding and customer support processes."
A few things that always surprise people about the KnowBe4 platform is its ease-of-use regardless of an organization’s size, the shockingly affordable pricing, and the extremely-wide library of world-class content.
Read the Security Awareness CBT report to find out what we believe sets KnowBe4 apart.
Download Your Complimentary Copy of the Report Now!
https://info.knowbe4.com/gartner-magic-quadrant-security-awareness-cbt-chn
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose. This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from KnowBe4. Gartner Magic Quadrant for Security Awareness Computer-Based Training, Joanna G. Huisman, 18 July 2019
[FIRST EVER] Now *SEE* Why Everyone is Raving About Our Platform
IT pros know that you need a strong human firewall as your last line of defense. You can see right now why your peers are choosing KnowBe4’s world-class awareness training and simulated phishing platform to create that human firewall.
For the first time in KnowBe4's history, for a limited time, we are making available an on-demand 30-minute product demo of our award-winning security awareness training. You can immediately see how easy it is to train and phish your users:
Train Your Users:
The world's largest library with 900+ pieces of security awareness training content.
Phish Your Users:
Best-in-class, fully automated simulated phishing attacks, with thousands of templates.
Phishing By Industry Benchmarking:
See how you stack up against your peers with the new phishing Industry Benchmarks!
See The Results:
Advanced Reporting on 60+ key awareness training indicators ready for management. Show the great ROI!
See for yourself why over 26,000 organizations worldwide use KnowBe4 to train and phish their users.
Watch This Limited Time 30-minute Demo Now:
https://info.knowbe4.com/kmsat-od-product-demonstration
IT pros know that you need a strong human firewall as your last line of defense. You can see right now why your peers are choosing KnowBe4’s world-class awareness training and simulated phishing platform to create that human firewall.
For the first time in KnowBe4's history, for a limited time, we are making available an on-demand 30-minute product demo of our award-winning security awareness training. You can immediately see how easy it is to train and phish your users:
Train Your Users:
The world's largest library with 900+ pieces of security awareness training content.
Phish Your Users:
Best-in-class, fully automated simulated phishing attacks, with thousands of templates.
Phishing By Industry Benchmarking:
See how you stack up against your peers with the new phishing Industry Benchmarks!
See The Results:
Advanced Reporting on 60+ key awareness training indicators ready for management. Show the great ROI!
See for yourself why over 26,000 organizations worldwide use KnowBe4 to train and phish their users.
Watch This Limited Time 30-minute Demo Now:
https://info.knowbe4.com/kmsat-od-product-demonstration
Microsoft Discovers New Excel-Based Attack to Deliver the FlawedArmmyRAT Malware
A new set of tweets from Microsoft Security Intelligence walks through an attack that uses a number of built-in Windows toolsets to infect machines with the notorious malware.
Many attackers attempt to “live off the land”, leveraging executables, tools, and scripting languages that are built into the Windows operating system as a way to avoid detection. This latest attack documented by Microsoft does exactly that with the intent of installing a remote access trojan (RAT) that gives an attacker complete control over the infected endpoint.
Here’s how it works:
This detailed set of steps is necessary for attackers to avoid detection. However, keep in mind that all the user experiences is the opening of the email and the clicking of the attachment – nothing more. THIS is why phishing is so successful: attackers automate all the malicious parts of the attack, only needing the unwitting user to simply start off the process.
Users that have gone through Security Awareness Training can easily spot the red flags in this type of attack. But you *have* to train them. Post with links:
https://blog.knowbe4.com/microsoft-discovers-new-excel-based-attack-to-deliver-the-flawedarmmyrat-malware
A new set of tweets from Microsoft Security Intelligence walks through an attack that uses a number of built-in Windows toolsets to infect machines with the notorious malware.
Many attackers attempt to “live off the land”, leveraging executables, tools, and scripting languages that are built into the Windows operating system as a way to avoid detection. This latest attack documented by Microsoft does exactly that with the intent of installing a remote access trojan (RAT) that gives an attacker complete control over the infected endpoint.
Here’s how it works:
- The potential victim receives an email containing an Excel spreadsheet as an attachment.
- When opened, the Excel file runs a macro that calls MSIexec (dot) com
- MSIexec downloads a Microsoft Installer (MSI) file to be installed
- The MSI file contains a digitally signed executable (so it must be safe, right?) that decrypts and loads a second executable directly into memory
- The second executable downloads another digitally signed file, wsus (dot) exe
- This file runs and loads the final payload – the FlawedArmmy RAT – into memory
This detailed set of steps is necessary for attackers to avoid detection. However, keep in mind that all the user experiences is the opening of the email and the clicking of the attachment – nothing more. THIS is why phishing is so successful: attackers automate all the malicious parts of the attack, only needing the unwitting user to simply start off the process.
Users that have gone through Security Awareness Training can easily spot the red flags in this type of attack. But you *have* to train them. Post with links:
https://blog.knowbe4.com/microsoft-discovers-new-excel-based-attack-to-deliver-the-flawedarmmyrat-malware
[Live Demo TOMORROW] Identify and Respond to Email Threats Faster With PhishER
Your users are likely already reporting potentially dangerous emails in some fashion within your organization. The increase of this email traffic... can present a new problem!
With only approximately 1 in 10 user-reported emails being verified as actually malicious, how do you handle the real phishing attacks and email threats —and just as importantly— effectively manage the other 90% of user-reported messages accurately and efficiently?
Now you can with PhishER, a product which allows your Incident Response team to quickly identify and respond to email threats faster. This will save them so much time!
See how you can best manage your user-reported messages.
Join us TOMORROW, July 24 @ 2:00 pm (ET), for a live 30-minute demonstration of the new PhishER platform. With PhishER you can:
Date/Time: Tomorrow, Wednesday, July 24 @ 2:00 pm (ET)
Save My Spot!
https://event.on24.com/wcc/r/2018396/91E93646DDA057B561EB41A24725B538?partnerref=CHN2
Your users are likely already reporting potentially dangerous emails in some fashion within your organization. The increase of this email traffic... can present a new problem!
With only approximately 1 in 10 user-reported emails being verified as actually malicious, how do you handle the real phishing attacks and email threats —and just as importantly— effectively manage the other 90% of user-reported messages accurately and efficiently?
Now you can with PhishER, a product which allows your Incident Response team to quickly identify and respond to email threats faster. This will save them so much time!
See how you can best manage your user-reported messages.
Join us TOMORROW, July 24 @ 2:00 pm (ET), for a live 30-minute demonstration of the new PhishER platform. With PhishER you can:
- Cut through your Incident Response inbox noise and respond to the most dangerous threats more quickly
- Automate message prioritization by rules you set into one of three categories: Clean, Spam or Threat
- See clusters of messages to identify a potential phishing attack against your organization
- Meet critical SLAs within your organization to process and prioritize threats and legitimate emails
- Easy integration with KnowBe4’s email add-in button, Phish Alert, or forwarding to a mailbox works too!
Date/Time: Tomorrow, Wednesday, July 24 @ 2:00 pm (ET)
Save My Spot!
https://event.on24.com/wcc/r/2018396/91E93646DDA057B561EB41A24725B538?partnerref=CHN2
[Scam of the Week] New 'US State Police' Phishing Extortion Scam Includes Contact Numbers
Our friend Larry Abrams at Bleeping computer warned: "A new extortion scam is underway that pretends to be from a US State Police detective who is willing to delete child pornography evidence if you send them $2,000 in Bitcoins. Pretending to be from a state police detective is a new twist, but what really stands out is that they also include a contact phone number that can be used to call the scammer.
We all know, or should know, about the sextortion emails people are receiving where the sender states they have hacked the recipient's computer and taped them doing things while on adult sites. Since then, we have seen further extortion scams that pretend to be the CIA, bomb threats, threats to ruin a website's reputation, and even from hitmen asking you to pay them to call off a hit.
In this new campaign, extortionists are pretending to be state police detectives for different states in the U.S.A. where they claim that the email recipient has been involved in this criminal behavior. As they retiring, they are offering to delete the evidence if the recipient sends them $2,000 in bitcoin."
Users have reported receiving these phishing emails from "states" such as California, Georgia, Florida, Minnesota, New York, and Tennessee. Full post with copy/paste ready-to-send email for your users and links to templates to inoculate all employees:
https://blog.knowbe4.com/scam-of-the-week-new-us-state-police-phishing-extortion-scam-includes-contact-numbers
Let's stay safe out there.
Our friend Larry Abrams at Bleeping computer warned: "A new extortion scam is underway that pretends to be from a US State Police detective who is willing to delete child pornography evidence if you send them $2,000 in Bitcoins. Pretending to be from a state police detective is a new twist, but what really stands out is that they also include a contact phone number that can be used to call the scammer.
We all know, or should know, about the sextortion emails people are receiving where the sender states they have hacked the recipient's computer and taped them doing things while on adult sites. Since then, we have seen further extortion scams that pretend to be the CIA, bomb threats, threats to ruin a website's reputation, and even from hitmen asking you to pay them to call off a hit.
In this new campaign, extortionists are pretending to be state police detectives for different states in the U.S.A. where they claim that the email recipient has been involved in this criminal behavior. As they retiring, they are offering to delete the evidence if the recipient sends them $2,000 in bitcoin."
Users have reported receiving these phishing emails from "states" such as California, Georgia, Florida, Minnesota, New York, and Tennessee. Full post with copy/paste ready-to-send email for your users and links to templates to inoculate all employees:
https://blog.knowbe4.com/scam-of-the-week-new-us-state-police-phishing-extortion-scam-includes-contact-numbers
Let's stay safe out there.
Warm Regards,
Stu Sjouwerman
Founder and CEO
KnowBe4, Inc
Quotes of the Week
"Quality is not an act, it is a habit."
- Aristotle, Greek Philosopher (384 BC - 322 BC)
"I'm a man of simple tastes. I'm always satisfied with the best."
- Oscar Wilde, Writer (1854 - 1900)
Thanks for reading CyberheistNews
- Aristotle, Greek Philosopher (384 BC - 322 BC)
"I'm a man of simple tastes. I'm always satisfied with the best."
- Oscar Wilde, Writer (1854 - 1900)
Thanks for reading CyberheistNews
Security News
Mimecast Identifies Brand New Phishing Tactic Called "SHTML"
In early April, the Mimecast Threat Center team discovered a rare type of server-parsed HTML (SHTML) based phishing attack emerging from the UK.
When users opened attachments in these phishing campaign emails, they were immediately redirected to a malicious site requesting sensitive information. The image above shows an example of the targeted attack email that organizations received.
Their Threat Center utilized this critical threat intelligence to create an advanced custom rule that directly identifies the SHTML construction, and in a two-month period since deployment, Mimecast detected more than 100,000 individual users being attacked with this new type of phishing.
Email Is Still the Number One Attack Vector. Here Is the Mimecast Takeaway:
"Phishing is an increasingly common and widespread problem that isn’t going away anytime soon. Remain vigilant by avoiding links and attachments – like the malicious SHTML document employed in the above phishing attack – in email messages unless you’re certain they’re legitimate. If in doubt, follow the most basic and effective solutions at your disposal – ignore, delete and report."
KnowBe4 strongly recommends the free Phish Alert Button to do that reporting to your Incident Response Team. Blog post with links:
https://blog.knowbe4.com/mimecast-identifies-brand-new-phishing-tactic-called-shtml
In early April, the Mimecast Threat Center team discovered a rare type of server-parsed HTML (SHTML) based phishing attack emerging from the UK.
When users opened attachments in these phishing campaign emails, they were immediately redirected to a malicious site requesting sensitive information. The image above shows an example of the targeted attack email that organizations received.
Their Threat Center utilized this critical threat intelligence to create an advanced custom rule that directly identifies the SHTML construction, and in a two-month period since deployment, Mimecast detected more than 100,000 individual users being attacked with this new type of phishing.
Email Is Still the Number One Attack Vector. Here Is the Mimecast Takeaway:
"Phishing is an increasingly common and widespread problem that isn’t going away anytime soon. Remain vigilant by avoiding links and attachments – like the malicious SHTML document employed in the above phishing attack – in email messages unless you’re certain they’re legitimate. If in doubt, follow the most basic and effective solutions at your disposal – ignore, delete and report."
KnowBe4 strongly recommends the free Phish Alert Button to do that reporting to your Incident Response Team. Blog post with links:
https://blog.knowbe4.com/mimecast-identifies-brand-new-phishing-tactic-called-shtml
Lateral Phishing Used to Attack Organizations on a Global Scale
Warwick Ashford at ComputerWeekly reported: "Lateral phishing is a growing type of account takeover that has enabled attackers to target more than 100,000 people by hijacking just 154 email accounts.
Lateral phishing represents a sophisticated evolution in email-based attacks, with 1 in 7 organisations targeted in this way in the past seven months, according to researchers at Barracuda Networks and the University of California, Berkeley.
Account takeover continues to be one of the fastest-growing email security threats, but attackers are starting to adapt, introducing new ways to exploit compromised accounts, such as lateral phishing, which uses hijacked accounts to send phishing emails to an array of recipients in the account’s contact list, ranging from close contacts in the company to partners at other organisations.
Out of the organisations targeted by lateral phishing, more than 60% had multiple compromised accounts.
Some had dozens of compromised accounts that sent lateral phishing attacks to additional employee accounts and users at other organisations.
A recent benchmarking report by security awareness training firm KnowBe4 shows that the average phish-prone percentage across all industries and sizes of organisations at 29.6% – up 2.6% since 2018.
Large organisations in the hospitality industry have the highest phish-prone percentage (PPP) of 48%, and are therefore most likely to fall victim to a phishing attack, while the transportation industry is at the lowest risk, with large organisations in the sector scoring a PPP of just 16%.
Because lateral phishing exploits the implicit trust in the legitimate accounts compromised, these attacks ultimately lead to increasingly large reputational harm for the initial victim organisation, the researchers said.
To defend against lateral phishing attacks, the researchers said there are three critical precautions organisations can take:
https://blog.knowbe4.com/lateral-phishing-used-to-attack-organizations-on-global-scale
Warwick Ashford at ComputerWeekly reported: "Lateral phishing is a growing type of account takeover that has enabled attackers to target more than 100,000 people by hijacking just 154 email accounts.
Lateral phishing represents a sophisticated evolution in email-based attacks, with 1 in 7 organisations targeted in this way in the past seven months, according to researchers at Barracuda Networks and the University of California, Berkeley.
Account takeover continues to be one of the fastest-growing email security threats, but attackers are starting to adapt, introducing new ways to exploit compromised accounts, such as lateral phishing, which uses hijacked accounts to send phishing emails to an array of recipients in the account’s contact list, ranging from close contacts in the company to partners at other organisations.
Out of the organisations targeted by lateral phishing, more than 60% had multiple compromised accounts.
Some had dozens of compromised accounts that sent lateral phishing attacks to additional employee accounts and users at other organisations.
A recent benchmarking report by security awareness training firm KnowBe4 shows that the average phish-prone percentage across all industries and sizes of organisations at 29.6% – up 2.6% since 2018.
Large organisations in the hospitality industry have the highest phish-prone percentage (PPP) of 48%, and are therefore most likely to fall victim to a phishing attack, while the transportation industry is at the lowest risk, with large organisations in the sector scoring a PPP of just 16%.
Because lateral phishing exploits the implicit trust in the legitimate accounts compromised, these attacks ultimately lead to increasingly large reputational harm for the initial victim organisation, the researchers said.
To defend against lateral phishing attacks, the researchers said there are three critical precautions organisations can take:
- Security awareness training
- Advanced detection techniques
- Two-factor authentication
https://blog.knowbe4.com/lateral-phishing-used-to-attack-organizations-on-global-scale
Attackers Are Shifting Their Focus to Easy Targets
One reason organizations are struggling to defend themselves against cyberattacks is because many sophisticated attackers are specifically targeting small and mid-sized organizations that don’t have large budgets, according to Michael Madon from Mimecast.
Madon joined the CyberWire’s Hacking Humans podcast to discuss how companies can better understand the cybersecurity skills gap. He explained that one of the factors driving the demand for skills is a wide array of new threats facing unprepared companies.
“There are three reasons why the cybersecurity enterprise is complex, I think,” Madon said. “One of them is the types and quantity of attacks are constantly changing and iterating, right? The enemy is super smart, and they're criminals, too, right? So you have state actors, and you have, really, either state-sponsored criminals or just really sophisticated criminals who wear suits to work every day…. Many times, these criminal networks are a concerted effort.”
In response to these increasingly advanced criminal operations, Madon said that larger companies with deeper pockets have gotten better about deploying advanced cyber defenses. As a result, many skilled hackers are finding it more efficient to go after softer targets.
“And so they're going downstream, and that's why you see an increase in the number of attacks in sort of the middle market,” Madon explains. “And so, these companies that typically would have had sort of mediocre hackers and mediocre criminals are now having really sophisticated hackers and criminals that are now attacking them, because those hackers and criminals are going to where it's easiest to attack.”
Cyberattacks aren’t necessarily a high-risk, high-reward effort
Cyberattacks aren’t necessarily a high-risk, high-reward effort for attackers. An attack against a smaller company can yield a decent payoff at a fraction of the effort it would take to hack a major corporation. On the other hand, while larger companies often have more defenses in place, it usually only takes a single mistake by an employee to let an attacker in. Organizations of all sizes can benefit from new-school security awareness training to prevent these attacks from succeeding. The CyberWire has the story:
https://thecyberwire.com/podcasts/cw-podcasts-hh-2019-07-18.html
One reason organizations are struggling to defend themselves against cyberattacks is because many sophisticated attackers are specifically targeting small and mid-sized organizations that don’t have large budgets, according to Michael Madon from Mimecast.
Madon joined the CyberWire’s Hacking Humans podcast to discuss how companies can better understand the cybersecurity skills gap. He explained that one of the factors driving the demand for skills is a wide array of new threats facing unprepared companies.
“There are three reasons why the cybersecurity enterprise is complex, I think,” Madon said. “One of them is the types and quantity of attacks are constantly changing and iterating, right? The enemy is super smart, and they're criminals, too, right? So you have state actors, and you have, really, either state-sponsored criminals or just really sophisticated criminals who wear suits to work every day…. Many times, these criminal networks are a concerted effort.”
In response to these increasingly advanced criminal operations, Madon said that larger companies with deeper pockets have gotten better about deploying advanced cyber defenses. As a result, many skilled hackers are finding it more efficient to go after softer targets.
“And so they're going downstream, and that's why you see an increase in the number of attacks in sort of the middle market,” Madon explains. “And so, these companies that typically would have had sort of mediocre hackers and mediocre criminals are now having really sophisticated hackers and criminals that are now attacking them, because those hackers and criminals are going to where it's easiest to attack.”
Cyberattacks aren’t necessarily a high-risk, high-reward effort
Cyberattacks aren’t necessarily a high-risk, high-reward effort for attackers. An attack against a smaller company can yield a decent payoff at a fraction of the effort it would take to hack a major corporation. On the other hand, while larger companies often have more defenses in place, it usually only takes a single mistake by an employee to let an attacker in. Organizations of all sizes can benefit from new-school security awareness training to prevent these attacks from succeeding. The CyberWire has the story:
https://thecyberwire.com/podcasts/cw-podcasts-hh-2019-07-18.html
What KnowBe4 Customers Say
"Stu, I am definitely very happy with the service and everyone I have dealt with at your organization. I cannot think of another organization that has been so helpful and eager to assist. Thanks!"
- C.C., Director Information Security
"You guys certainly are providing me with a fantastic level of support, guidance, and a great platform to delight our customers and continue growing both of our businesses.
Jon has been very supportive and sharp, Katie has been doing a great job of helping provide feedback and guidance on our client configurations, the content and material provided by the evangelists and made available as webinars and whitepapers have been fantastic, and KB4-Con was amazing.
I greatly enjoyed meeting yourself, Jon, and the rest of the KnowBe4 team that was in attendance in May; and the sheer level of passion, enthusiasm, and caring exhibited by all of your staff is overwhelmingly positive and reassuring to see in a partner of ours.
I’ll be rolling out a bundled security product in Q4 at with KnowBe4’s KMSAT as one of the key backbone components, so hopefully we’ll see even more growth as that gains traction and gets some sales in 2020. I’m greatly looking forward to growing both of our businesses further as our security offerings become more robust and as the KMSAT platform keeps growing!"
- K.J., Cybersecurity Manager at a KnowBe4 Channel partner
KnowBe4 Adds Language Localization to Learner's Experience for All Customers We are excited to announce the availability of KnowBe4’s new localized training interface option for your users! Currently available in 15 local languages, your users now can choose the language they're most comfortable with for their entire training interface, helping deliver a more immersive training experience. More:
https://blog.knowbe4.com/knowbe4-adds-language-localization-to-learners-experience-for-all-customers
KnowBe4 Quarterly Product Update Video Q2. All the new cool features in just 15 minutes!:
https://blog.knowbe4.com/video-knowbe4-quarterly-product-update-0
"Stu, I am definitely very happy with the service and everyone I have dealt with at your organization. I cannot think of another organization that has been so helpful and eager to assist. Thanks!"
- C.C., Director Information Security
"You guys certainly are providing me with a fantastic level of support, guidance, and a great platform to delight our customers and continue growing both of our businesses.
Jon has been very supportive and sharp, Katie has been doing a great job of helping provide feedback and guidance on our client configurations, the content and material provided by the evangelists and made available as webinars and whitepapers have been fantastic, and KB4-Con was amazing.
I greatly enjoyed meeting yourself, Jon, and the rest of the KnowBe4 team that was in attendance in May; and the sheer level of passion, enthusiasm, and caring exhibited by all of your staff is overwhelmingly positive and reassuring to see in a partner of ours.
I’ll be rolling out a bundled security product in Q4 at with KnowBe4’s KMSAT as one of the key backbone components, so hopefully we’ll see even more growth as that gains traction and gets some sales in 2020. I’m greatly looking forward to growing both of our businesses further as our security offerings become more robust and as the KMSAT platform keeps growing!"
- K.J., Cybersecurity Manager at a KnowBe4 Channel partner
KnowBe4 Adds Language Localization to Learner's Experience for All Customers We are excited to announce the availability of KnowBe4’s new localized training interface option for your users! Currently available in 15 local languages, your users now can choose the language they're most comfortable with for their entire training interface, helping deliver a more immersive training experience. More:
https://blog.knowbe4.com/knowbe4-adds-language-localization-to-learners-experience-for-all-customers
KnowBe4 Quarterly Product Update Video Q2. All the new cool features in just 15 minutes!:
https://blog.knowbe4.com/video-knowbe4-quarterly-product-update-0
The 10 Interesting News Items This Week
- Send This One to Your C-suite: "Equifax to Pay Around $700 Million to Resolve Data-Breach Probes":
https://www.wsj.com/articles/equifax-to-pay-around-700-million-to-resolve-data-breach-probes-11563577702? - Deep Fakes are getting better every day with AI/machine learning and start to pose a major threat to your org. Discuss this problem at the HackBusters forum here:
https://discuss.hackbusters.com/t/deep-fakes-getting-better-every-day-with-ai-machine-learning/4439 - The Single Biggest Computer Defense Decision You Must Get Right:
https://cybersecurityventures.com/the-single-biggest-computer-defense-decision-you-must-get-right/ - A Whopping 93% of Orgs Worry About Cloud Security:
https://www.infosecurity-magazine.com/news/93-of-orgs-worry-about-cloud/ - The Top 25 Women in Cybersecurity - Winners:
http://cyberdefenseawards.com/top-25-women-in-cybersecurity/ - Threatlist: 68% of Overwhelmed IT Managers Can’t Keep up with Cyberattacks:
https://threatpost.com/overwhelmed-it-managers-cyberattacks/146450/ - Ransomware Attacks Grow Rampant, Paying Still Not a Good Option:
https://www.bleepingcomputer.com/news/security/ransomware-attacks-grow-rampant-paying-still-not-a-good-option/ - Why 72% of people still recycle passwords:
https://www.techrepublic.com/article/why-72-of-people-still-recycle-passwords/ - Funny article stating that most Cybersec budget should go to awareness. Wildly exaggerated but he's trying to make a point:
https://www.itworldcanada.com/article/bulk-of-cyber-budget-should-go-to-awareness-training-not-technology-says-expert/420064 - “Information Terrorism: Can You Trust Your Toaster?” paper that won the Sun Tzu award from National Defense University:
https://www.devost.net/papers/suntzu.pdf - BONUS: New SANS Security Awareness Report Highlights the Rising Era of Awareness Training:
https://blog.knowbe4.com/sans-security-awareness-report-highlights-the-rising-era-of-awareness-training
Cyberheist 'Fave' Links
This Week's Links We Like, Tips, Hints and Fun Stuff
- The First Trailer For Top Gun 2 Has Finally Touched Down! Summer 2020:
https://www.thedrive.com/the-war-zone/29061/the-first-trailer-for-top-gun-2-has-finally-touched-down
- Buster Keaton's Most Amazing Stunts, he is one of the greatest and most influential comedians and stunt performers of all time:
https://www.flixxy.com/buster-keatons-most-amazing-stunts.htm?utm_source=4
- The Amazing 1202 Alarm: Apollo 11 Had a Hidden Hero -- Software:
https://www.youtube.com/watch?v=z4cn93H6sM0
- Watch "Mr. Robot: The Final Season Preview: How Many People Have You Hurt?":
https://www.youtube.com/watch?v=sbc97xo7N9A&feature=youtu.be
- Penn & Teller FOOL US - Axel Hecklau vanishes Tellers driving license:
https://www.flixxy.com/magician-axel-hecklau-vanishes-tellers-driving-license.htm?utm_source=4
- The World's Most Popular Algorithm: SHA 256 and Bitcoin. Love how he explains!
https://www.youtube.com/watch?v=8COArd_EREw&feature=youtu.be
- The “Unpickable” Europa Disc Padlock Picked FAST:
https://www.youtube.com/watch?v=F_38TFES88I&feature=youtu.be
- The IRS fights against ID Theft and asks Tax Pros to join the fray. Check No. 3:
https://www.youtube.com/watch?v=mCOJbsQ0b88
- SpaceX Crew Dragon Parachute Tests. Nicely done photography of the chute deploy and landing!:
https://www.youtube.com/watch?v=B9eYCGOlr5Y
- Scientist Explains How She Captured Rare Footage of The Elusive Giant Squid:
https://video.wired.com/watch/scientist-explains-how-she-captured-footage-of-a-giant-squid
- The first trailer for the movie 'Cats' has arrived- featuring Jennifer Hudson, Taylor Swift, James Corden and Judi Dench:
https://www.flixxy.com/cats-movie-trailer.htm?utm_source=4 - For the Kids - Here’s a first look at Apple’s Peanuts show featuring astronaut Snoopy:
https://www.youtube.com/watch?v=n4hgH6IX2lU&feature=youtu.be





