CyberheistNews Vol 7 #35
These 4 Maps Will Make You Understand Russia's Aggressive Cyber Attacks 
There are many kinds of maps, they can show roads or general geography, but sometimes they shed light on other dimensions like economic, political and/or military perspectives.
First of all, you need to realize that planet Earth is an "anarchy of nations". There is no planetary overlord—which we probably should be glad about—and the United Nations are corrupt and ineffective. Countries are locked in a constant struggle for power.
These maps explain why Russia is so incredibly aggressive on the internet, and essentially is using the net as an integral part of their asymmetric cold warfare.
Strategically speaking, Russia is in a difficult spot since the 1991 collapse of the communist Soviet Union. Putin has repeatedly said this is his biggest regret, and he wants to resurrect the old Soviet power (where his job was stealing Western intellectual property for the KGB).
Here is a map that shows the furthest reach of the old Soviet regime during the cold war:
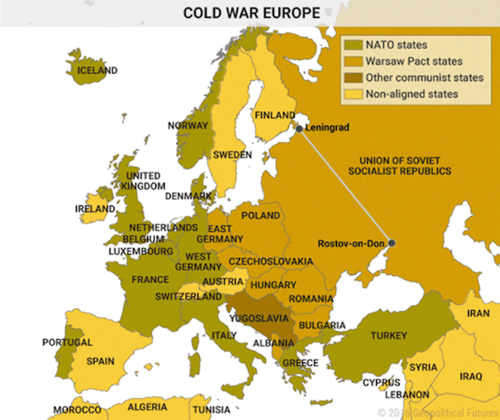
Have a look at the straight line drawn from Leningrad to Rostov-on-Don, and keep that line in mind. (Note that Leningrad became St. Petersburg in 1991 after the collapse).
No Natural Barriers
Now, there are no natural barriers that stop invaders from Western Europe to roll straight into Russia, like the Germans did in the Second World War. Here is a map that illustrates this:
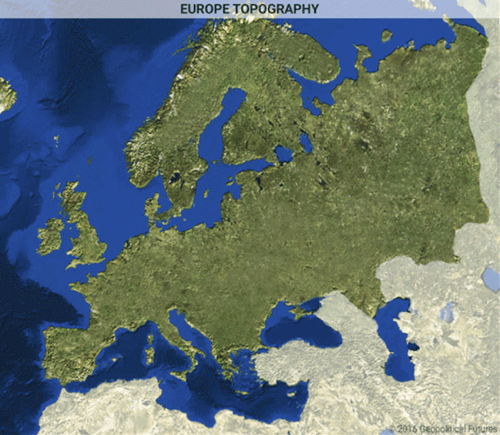
Since the 1991 collapse, Russia has no buffers in place to protect against an invasion, and NATO has made significant inroads in Eastern Europe. The other problem is that Russia is almost landlocked and has no easy access to the sea.
Landlocked
Basically Europe controls Russia's access to the sea, and during the Cold War, air bases in Norway, Scotland, and Iceland, coupled with carrier battle groups, worked to deny Russia access to the sea. This demonstrates the vulnerability Russia faces due to its lack of access to oceans and waterways.
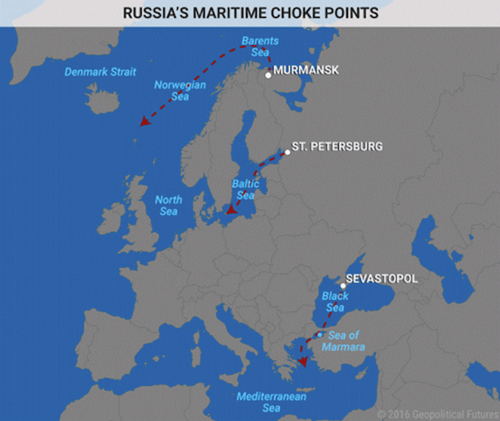
Cannot Project Significant Force
Russia cannot project significant force because its naval force is bottled up and because you cannot support major forces from the air alone. Russia's primary issue is the western frontier and Ukraine. Putin thinks that the Euro-American interest in creating a pro-Western regime there has a purpose beyond Ukraine. Putin's Ukraine viewpoint is that they lost a critical buffer zone, and guess what, from his perspective he is right.
Russian Economy in Serious Trouble
Russia's economy is very much like an intersection in the boondocks with a gas station, a gun shop, and a flag on top. Their economy is in serious trouble given the plummeting price of oil in the past years and no expectation of getting better. Their weapons exports only partially compensate for this.
The Upshot
Russia occupies the weaker strategic position, having lost their western buffers against an invader, an economy in trouble, and are struggling to maintain the physical integrity of their "Mother Russia".
Here is the picture of how things look now, and compare the straight line from St. Petersburg to Rostov-on-Don again with the first map:
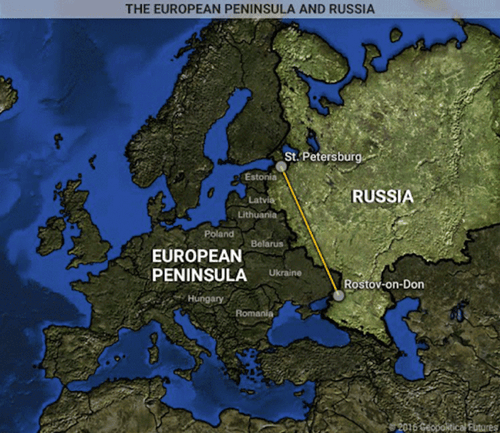
It is not hard to see why they are grabbing hold of any strategic advantage they can get their hands on, and the internet allows them to overcome traditional military limitations. Russian cyber attacks by the FSB, GRU and organized cyber crime (protected by the Kremlin) are not going away any time soon.
The Gerasimov Doctrine
The WSJ observed: "Russia’s military laid out what is now seen as a blueprint for cyberwarfare with a 2013 article in a professional journal by Gen. Valery Gerasimov, the chief of Russia’s General Staff. Cyberspace, wrote Gen. Gerasimov, 'opens wide asymmetrical possibilities for reducing the fighting potential of the enemy.'"
In his 2013 article, Gerasimov talked about the Russian military’s desire to hone its hacking skills as an extension of conventional warfare and political conflict. In reality, they were already deeply engaged in this and expanding their reach. In Washington’s defense and national security circles, Russia’s attacks in cyberspace have become known as the “Gerasimov doctrine”.
In addition to the above, Russian President Vladimir Putin said a few days ago: "The leader in Artificial Intelligence will rule the world." He predicted that future wars will be fought by drones, and "when one party's drones are destroyed by drones of another, it will have no other choice but to surrender." Terminator, here we come.
Note, the vast majority of Russia's cyber attacks start with social engineering and spear phishing.

There are many kinds of maps, they can show roads or general geography, but sometimes they shed light on other dimensions like economic, political and/or military perspectives.
First of all, you need to realize that planet Earth is an "anarchy of nations". There is no planetary overlord—which we probably should be glad about—and the United Nations are corrupt and ineffective. Countries are locked in a constant struggle for power.
These maps explain why Russia is so incredibly aggressive on the internet, and essentially is using the net as an integral part of their asymmetric cold warfare.
Strategically speaking, Russia is in a difficult spot since the 1991 collapse of the communist Soviet Union. Putin has repeatedly said this is his biggest regret, and he wants to resurrect the old Soviet power (where his job was stealing Western intellectual property for the KGB).
Here is a map that shows the furthest reach of the old Soviet regime during the cold war:

Have a look at the straight line drawn from Leningrad to Rostov-on-Don, and keep that line in mind. (Note that Leningrad became St. Petersburg in 1991 after the collapse).
No Natural Barriers
Now, there are no natural barriers that stop invaders from Western Europe to roll straight into Russia, like the Germans did in the Second World War. Here is a map that illustrates this:

Since the 1991 collapse, Russia has no buffers in place to protect against an invasion, and NATO has made significant inroads in Eastern Europe. The other problem is that Russia is almost landlocked and has no easy access to the sea.
Landlocked
Basically Europe controls Russia's access to the sea, and during the Cold War, air bases in Norway, Scotland, and Iceland, coupled with carrier battle groups, worked to deny Russia access to the sea. This demonstrates the vulnerability Russia faces due to its lack of access to oceans and waterways.

Cannot Project Significant Force
Russia cannot project significant force because its naval force is bottled up and because you cannot support major forces from the air alone. Russia's primary issue is the western frontier and Ukraine. Putin thinks that the Euro-American interest in creating a pro-Western regime there has a purpose beyond Ukraine. Putin's Ukraine viewpoint is that they lost a critical buffer zone, and guess what, from his perspective he is right.
Russian Economy in Serious Trouble
Russia's economy is very much like an intersection in the boondocks with a gas station, a gun shop, and a flag on top. Their economy is in serious trouble given the plummeting price of oil in the past years and no expectation of getting better. Their weapons exports only partially compensate for this.
The Upshot
Russia occupies the weaker strategic position, having lost their western buffers against an invader, an economy in trouble, and are struggling to maintain the physical integrity of their "Mother Russia".
Here is the picture of how things look now, and compare the straight line from St. Petersburg to Rostov-on-Don again with the first map:

It is not hard to see why they are grabbing hold of any strategic advantage they can get their hands on, and the internet allows them to overcome traditional military limitations. Russian cyber attacks by the FSB, GRU and organized cyber crime (protected by the Kremlin) are not going away any time soon.
The Gerasimov Doctrine
The WSJ observed: "Russia’s military laid out what is now seen as a blueprint for cyberwarfare with a 2013 article in a professional journal by Gen. Valery Gerasimov, the chief of Russia’s General Staff. Cyberspace, wrote Gen. Gerasimov, 'opens wide asymmetrical possibilities for reducing the fighting potential of the enemy.'"
In his 2013 article, Gerasimov talked about the Russian military’s desire to hone its hacking skills as an extension of conventional warfare and political conflict. In reality, they were already deeply engaged in this and expanding their reach. In Washington’s defense and national security circles, Russia’s attacks in cyberspace have become known as the “Gerasimov doctrine”.
In addition to the above, Russian President Vladimir Putin said a few days ago: "The leader in Artificial Intelligence will rule the world." He predicted that future wars will be fought by drones, and "when one party's drones are destroyed by drones of another, it will have no other choice but to surrender." Terminator, here we come.
Note, the vast majority of Russia's cyber attacks start with social engineering and spear phishing.
NEW: Have Your Users Made You an Easy Target for Spear Phishing?
Many of the emails addresses and identities of your organization are exposed on the Internet and easy to find for cybercriminals. With that email attack surface, they can launch social engineering, spear phishing and ransomware attacks on your organization.
Our NEW Email Exposure Check Pro goes even further to identify the at-risk users in your organization by crawling business social media information and scouring hundreds of breach databases. This is done in two stages:
First Stage: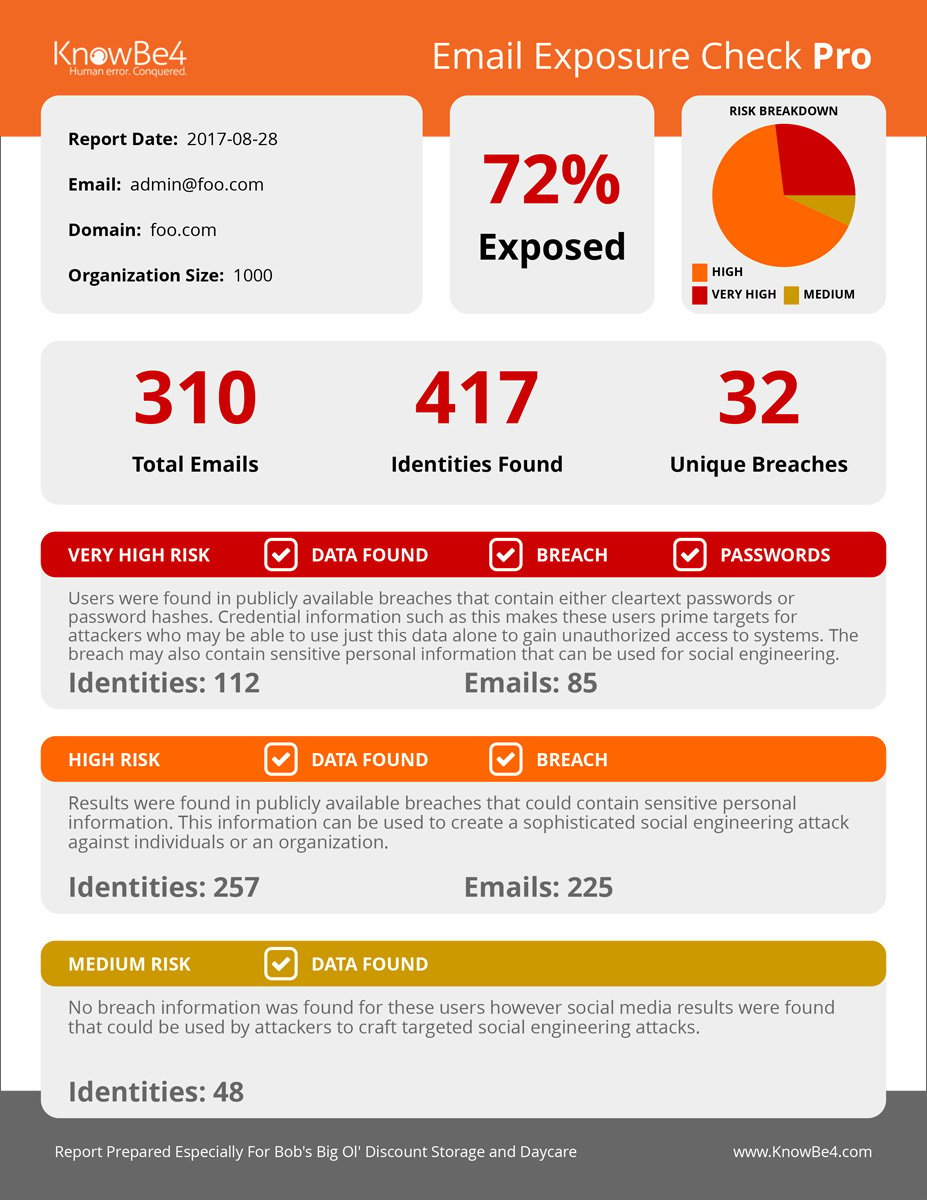
Does deep web searches to find any publicly available organizational data. This will show you what your organizational structure looks like to an attacker, which they can use to craft targeted spear phishing attacks.
Second Stage: Finds any users that have had their account information exposed in any of several hundred breaches. These users are particularly at-risk because an attacker knows more about that user, up to and including their actual passwords!
Your EEC Pro Reports: We will email you back a summary report PDF of the number of exposed emails, identities and risk levels found. You will also get a link to the full detailed report of actual users found, including breach name and if a password was exposed.
This is so important that even if you already ran your one-time no-charge legacy EEC, you are eligible to try the new Pro version. Request your complimentary one-time Email Exposure Check Pro here:
https://info.knowbe4.com/email-exposure-check-pro-chn
Many of the emails addresses and identities of your organization are exposed on the Internet and easy to find for cybercriminals. With that email attack surface, they can launch social engineering, spear phishing and ransomware attacks on your organization.
Our NEW Email Exposure Check Pro goes even further to identify the at-risk users in your organization by crawling business social media information and scouring hundreds of breach databases. This is done in two stages:
First Stage:

Does deep web searches to find any publicly available organizational data. This will show you what your organizational structure looks like to an attacker, which they can use to craft targeted spear phishing attacks.
Second Stage: Finds any users that have had their account information exposed in any of several hundred breaches. These users are particularly at-risk because an attacker knows more about that user, up to and including their actual passwords!
Your EEC Pro Reports: We will email you back a summary report PDF of the number of exposed emails, identities and risk levels found. You will also get a link to the full detailed report of actual users found, including breach name and if a password was exposed.
This is so important that even if you already ran your one-time no-charge legacy EEC, you are eligible to try the new Pro version. Request your complimentary one-time Email Exposure Check Pro here:
https://info.knowbe4.com/email-exposure-check-pro-chn
The 5 Cyber Attacks You're Most Likely to Face
IT Security Guru Roger Grimes did it again. He boiled things down to something easy to understand and execute. He started out with: "Don't be distracted by the exploit of the week. Invest your time and money defending against the threats you're apt to confront".
"As a consultant, one of the security biggest problems I see is perception: The threats companies think they face are often vastly different than the threats that pose the greatest risk. For example, they hire me to deploy state-of-the-art public key infrastructure (PKI) or an enterprise-wide intrusion detection system when really what they need is better patching.
"The fact is most companies face the same threats -- and should be doing their utmost to counteract those risks. Here are the five most common successful cyber attacks." I am just listing the 5 threats here, you should read the whole article with the explanation and countermeasures of each threat:
Cyber attack No. 1: Socially engineered malware
Cyber attack No. 2: Password phishing attacks
Cyber attack No. 3: Unpatched software
Cyber attack No. 4: Social media threats
Cyber attack No. 5: Advanced persistent threats
Note that in Attack 5 (APT) Grimes mentions phishing, and recommends strong end-user education in 3 of the other 4. Here is the article, take 5 minutes to read it, this is time very well spent and excellent ammo to get IT Security budget:
http://www.csoonline.com/article/2616316/data-protection/security-the-5-cyber-attacks-you-re-most-likely-to-face.html
IT Security Guru Roger Grimes did it again. He boiled things down to something easy to understand and execute. He started out with: "Don't be distracted by the exploit of the week. Invest your time and money defending against the threats you're apt to confront".
"As a consultant, one of the security biggest problems I see is perception: The threats companies think they face are often vastly different than the threats that pose the greatest risk. For example, they hire me to deploy state-of-the-art public key infrastructure (PKI) or an enterprise-wide intrusion detection system when really what they need is better patching.
"The fact is most companies face the same threats -- and should be doing their utmost to counteract those risks. Here are the five most common successful cyber attacks." I am just listing the 5 threats here, you should read the whole article with the explanation and countermeasures of each threat:
Cyber attack No. 1: Socially engineered malware
Cyber attack No. 2: Password phishing attacks
Cyber attack No. 3: Unpatched software
Cyber attack No. 4: Social media threats
Cyber attack No. 5: Advanced persistent threats
Note that in Attack 5 (APT) Grimes mentions phishing, and recommends strong end-user education in 3 of the other 4. Here is the article, take 5 minutes to read it, this is time very well spent and excellent ammo to get IT Security budget:
http://www.csoonline.com/article/2616316/data-protection/security-the-5-cyber-attacks-you-re-most-likely-to-face.html
Phishing Attack With PowerPoint Attachment Bypasses User Access Control
Fortinet researchers discovered a malicious PowerPoint file which currently is used to attack diplomats, United Nations and government organizations worldwide. This will soon filter down to mass phishing attacks.
The attack uses an existing Microsoft Office vulnerability in combination with a technique to bypass User Account Control (UAC) to infect systems. CVE-2017-0199 was patched in April this year and is a favorite cybercrime target, because despite the availability of the patch, many organizations have not patched Office for a variety of reasons.
The CVE-2017-0199 vulnerability in Office is something you want to patch NOW.
Fortinet researchers discovered a malicious PowerPoint file which currently is used to attack diplomats, United Nations and government organizations worldwide. This will soon filter down to mass phishing attacks.
The attack uses an existing Microsoft Office vulnerability in combination with a technique to bypass User Account Control (UAC) to infect systems. CVE-2017-0199 was patched in April this year and is a favorite cybercrime target, because despite the availability of the patch, many organizations have not patched Office for a variety of reasons.
The CVE-2017-0199 vulnerability in Office is something you want to patch NOW.
Warm Regards,
Stu Sjouwerman
Quotes of the Week
"Your time is limited, so don’t waste it living someone else’s life." - Steve Jobs
"Do not dwell in the past, do not dream of the future, concentrate the mind on the
present moment." - Buddha
Thanks for reading CyberheistNews
"Do not dwell in the past, do not dream of the future, concentrate the mind on the
present moment." - Buddha
Thanks for reading CyberheistNews
Security News
MacEwan University Victim of 11.8 Million Dollar CEO Fraud
CBC News reported that an Edmonton, Canada university was the victim of a US 11.8 million dollars CEO fraud attack after staff failed to call one of its vendors to verify whether emails requesting a change in banking information were legitimate.
"MacEwan University discovered the fraud on Aug. 23 after the legitimate vendor, a construction company, called to ask why it hadn't been paid. Three payments were made to the fraudulent account: one on Aug. 10 for 1.9 million; another on Aug. 17 for 22,000 and a third on Aug. 19 for 9.9 million dollars. More on how this happened at the KnowBe4 blog:
https://blog.knowbe4.com/macewan-university-victim-of-11.8m-ceo-fraud
CBC News reported that an Edmonton, Canada university was the victim of a US 11.8 million dollars CEO fraud attack after staff failed to call one of its vendors to verify whether emails requesting a change in banking information were legitimate.
"MacEwan University discovered the fraud on Aug. 23 after the legitimate vendor, a construction company, called to ask why it hadn't been paid. Three payments were made to the fraudulent account: one on Aug. 10 for 1.9 million; another on Aug. 17 for 22,000 and a third on Aug. 19 for 9.9 million dollars. More on how this happened at the KnowBe4 blog:
https://blog.knowbe4.com/macewan-university-victim-of-11.8m-ceo-fraud
Ransomware Is Going More Corporate, Less Consumer
Cybercriminals on average charge 544 dollars for ransom per device, signaling a new sweet spot for payouts.
DarkReading wrote about Symantec's Internet Security Threat Report released last week, where they had up-to-date numbers on ransomware. It is is on track to surpass last year's wave of attacks, and businesses are getting hit with ransomware nearly as much as consumers.
Based on the 319,000 Symantec-blocked ransomware incidents that occurred during the first half of this year, the security giant is anticipating 2017 to easily surpass last year's 470,000 incidents, says Kevin Haley, director of Symantec's Security Response team.
"You have to give a lot of credit to WannaCry and Petya, but even without those two the numbers are increasing," Haley says. "WannaCry and Petya provide guideposts to other malware authors who see worms as an effective way for propagation."
Ransomware Worms Its Way Onto Corporate Networks
Ransomware deployed as worms tends to hit companies far harder than consumers, given that malicious malware can shoot through corporate networks with great speed. Consumers, on the other hand, are usually not connected to a network. More at DarkReading:
https://www.darkreading.com/endpoint/ransomware-is-going-more-corporate-less-consumer/d/d-id/1329774?
Cybercriminals on average charge 544 dollars for ransom per device, signaling a new sweet spot for payouts.
DarkReading wrote about Symantec's Internet Security Threat Report released last week, where they had up-to-date numbers on ransomware. It is is on track to surpass last year's wave of attacks, and businesses are getting hit with ransomware nearly as much as consumers.
Based on the 319,000 Symantec-blocked ransomware incidents that occurred during the first half of this year, the security giant is anticipating 2017 to easily surpass last year's 470,000 incidents, says Kevin Haley, director of Symantec's Security Response team.
"You have to give a lot of credit to WannaCry and Petya, but even without those two the numbers are increasing," Haley says. "WannaCry and Petya provide guideposts to other malware authors who see worms as an effective way for propagation."
Ransomware Worms Its Way Onto Corporate Networks
Ransomware deployed as worms tends to hit companies far harder than consumers, given that malicious malware can shoot through corporate networks with great speed. Consumers, on the other hand, are usually not connected to a network. More at DarkReading:
https://www.darkreading.com/endpoint/ransomware-is-going-more-corporate-less-consumer/d/d-id/1329774?
A Phishing Attack in the Clouds May Rain on Your Parade
According to MeriTalk, an editorial and events organization that focuses on Federal IT and government computing technologies, governments are moving some, or all of their IT to the cloud, because of its attractive pricing models in addition to other value added services.
MeriTalk noted that “both Federal and state governments use Office 365 for reasons such as cost savings, security, privacy, and accessibility. The State of New York saved 3 million dollars a year when it adopted Office 365 and the city of Chicago experienced an 80 percent decrease in cost per employee.
Microsoft also restricts content so it’s only shared with intended users, and contains tools to make its technology accessible to people who are visually impaired, deaf, or hard of hearing. These added enhancements and accessibility features are costly for organizations to build and maintain internally.
The Office 365 Account Compromise
But according to a new Barracuda blog post, on August 30, Office 365 is becoming a popular place to get phished. “Cybercriminals have a long history of designing attacks to reach the largest number of eyeballs possible. From the early days of traditional spam, to search or trending topics on social platforms, criminals follow the users—and Office 365 has become a breeding ground for highly personalized, compelling attacks.”
The new threat is called the Office 365 Account Compromise. The social engineering red flag is an email purportedly coming from Microsoft notifying you that your account has been suspended and imploring you to take action by clicking on the link in the graphic. Microsoft does not typically send such suspension notices.
The attack methodology is the typical “credential grab”
Click on the graphic link. Provide the crooks with your login credentials and bam. Your account is compromised. Your contacts are compromised. Your organization is now susceptible to lateral penetration from trusted emails.
The bad guys are no longer sending amateur emails with the usual big red flags like poor spelling, sloppy graphics, and grammatical errors. The current crop of phishers uses carefully constructed, next generation, socially engineered templates which are often hard to recognize without special security training.
Microsoft is trying to build phishing detection into Office 365 but it only offers Advanced Threat Protection as a part of its Office 365 Enterprise E5 plan which is much more costly and uses a method called URL detonation and Dynamic delivery.
At the end of the day, machine-based detection while good but expensive is likely not yet a replacement for individual security awareness training against the potential for human error.
Commonly used phishing methods are to get you to open a PDF, ZIP file, or even a graphic which has an embedded stealth executable that executes scripts that present you with a phony but carefully designed simulated login page all designed to steal your credentials.
According to a recent Barracuda survey:
According to MeriTalk, an editorial and events organization that focuses on Federal IT and government computing technologies, governments are moving some, or all of their IT to the cloud, because of its attractive pricing models in addition to other value added services.
MeriTalk noted that “both Federal and state governments use Office 365 for reasons such as cost savings, security, privacy, and accessibility. The State of New York saved 3 million dollars a year when it adopted Office 365 and the city of Chicago experienced an 80 percent decrease in cost per employee.
Microsoft also restricts content so it’s only shared with intended users, and contains tools to make its technology accessible to people who are visually impaired, deaf, or hard of hearing. These added enhancements and accessibility features are costly for organizations to build and maintain internally.
The Office 365 Account Compromise
But according to a new Barracuda blog post, on August 30, Office 365 is becoming a popular place to get phished. “Cybercriminals have a long history of designing attacks to reach the largest number of eyeballs possible. From the early days of traditional spam, to search or trending topics on social platforms, criminals follow the users—and Office 365 has become a breeding ground for highly personalized, compelling attacks.”
The new threat is called the Office 365 Account Compromise. The social engineering red flag is an email purportedly coming from Microsoft notifying you that your account has been suspended and imploring you to take action by clicking on the link in the graphic. Microsoft does not typically send such suspension notices.
The attack methodology is the typical “credential grab”
Click on the graphic link. Provide the crooks with your login credentials and bam. Your account is compromised. Your contacts are compromised. Your organization is now susceptible to lateral penetration from trusted emails.
The bad guys are no longer sending amateur emails with the usual big red flags like poor spelling, sloppy graphics, and grammatical errors. The current crop of phishers uses carefully constructed, next generation, socially engineered templates which are often hard to recognize without special security training.
Microsoft is trying to build phishing detection into Office 365 but it only offers Advanced Threat Protection as a part of its Office 365 Enterprise E5 plan which is much more costly and uses a method called URL detonation and Dynamic delivery.
At the end of the day, machine-based detection while good but expensive is likely not yet a replacement for individual security awareness training against the potential for human error.
Commonly used phishing methods are to get you to open a PDF, ZIP file, or even a graphic which has an embedded stealth executable that executes scripts that present you with a phony but carefully designed simulated login page all designed to steal your credentials.
According to a recent Barracuda survey:
- Of respondents using the cloud today, 40 percent of their infrastructure is already in the public cloud, and they expect to increase this to almost 70 percent within five years.
- 99 percent said that their organizations have seen benefits as a result of moving to the public cloud.
- 91 percent reported they had concerns over their use of public cloud, with 54 percent stating that cyber attacks are their chief concern.
- 71 percent felt the cloud provider was responsible for customer data in the public cloud, and 66 percent felt the cloud provider was responsible for their applications in the public cloud.
- Nine out of 10 (91% ) of organizations reported they had concerns over their use of public cloud, with cyber attacks being the chief concern at 54%. Over half (56%) had experienced at least one cyber attack, and 30% expect this to continue in the future.
Artificial Intelligence Cyber Attacks Are Coming – But What Does That Mean?
A good article at TheConversation started with: "The next major cyberattack could involve artificial intelligence systems. It could even happen soon: At a recent cybersecurity conference, 62 industry professionals, out of the 100 questioned, said they thought the first AI-enhanced cyberattack could come in the next 12 months. "This doesn’t mean robots will be marching down Main Street. Rather, artificial intelligence will make existing cyberattack efforts – things like identity theft, denial-of-service attacks and password cracking – more powerful and more efficient. [...]
"As a scholar who has studied AI decision-making, I can tell you that interpreting human actions is still difficult for AI’s and that humans don’t really trust AI systems to make major decisions. So, unlike in the movies, the capabilities AI could bring to cyberattacks – and cyberdefense – are not likely to immediately involve computers choosing targets and attacking them on their own.
"People will still have to create attack AI systems, and launch them at particular targets. But nevertheless, adding AI to today’s cybercrime and cybersecurity world will escalate what is already a rapidly changing arms race between attackers and defenders."" Full article:
https://theconversation.com/artificial-intelligence-cyber-attacks-are-coming-but-what-does-that-mean-82035
A good article at TheConversation started with: "The next major cyberattack could involve artificial intelligence systems. It could even happen soon: At a recent cybersecurity conference, 62 industry professionals, out of the 100 questioned, said they thought the first AI-enhanced cyberattack could come in the next 12 months. "This doesn’t mean robots will be marching down Main Street. Rather, artificial intelligence will make existing cyberattack efforts – things like identity theft, denial-of-service attacks and password cracking – more powerful and more efficient. [...]
"As a scholar who has studied AI decision-making, I can tell you that interpreting human actions is still difficult for AI’s and that humans don’t really trust AI systems to make major decisions. So, unlike in the movies, the capabilities AI could bring to cyberattacks – and cyberdefense – are not likely to immediately involve computers choosing targets and attacking them on their own.
"People will still have to create attack AI systems, and launch them at particular targets. But nevertheless, adding AI to today’s cybercrime and cybersecurity world will escalate what is already a rapidly changing arms race between attackers and defenders."" Full article:
https://theconversation.com/artificial-intelligence-cyber-attacks-are-coming-but-what-does-that-mean-82035
Vote for KnowBe4 at the 2017 Computing Security Awards!
KnowBe4 made it as Finalist in the 2017 Computing Security Awards, and we'd be eternally grateful if you could vote for us in the category "Education and Training Provider of the Year".
They invited everyone to cast their votes and said: "An acknowledgement will be sent to the email address you provide. Please take care when entering this email address. Votes will not be counted if the acknowledgement email is undelivered. Voting closes 5th October 2017.
There are 25 drop-downs with finalists, and these are always interesting to check out if you need a shortlist for the leaders in a particular space.
It would be awesome if you could vote for us! This is the link:
http://computingsecurityawards.co.uk/?page=csa2017vote
KnowBe4 made it as Finalist in the 2017 Computing Security Awards, and we'd be eternally grateful if you could vote for us in the category "Education and Training Provider of the Year".
They invited everyone to cast their votes and said: "An acknowledgement will be sent to the email address you provide. Please take care when entering this email address. Votes will not be counted if the acknowledgement email is undelivered. Voting closes 5th October 2017.
There are 25 drop-downs with finalists, and these are always interesting to check out if you need a shortlist for the leaders in a particular space.
It would be awesome if you could vote for us! This is the link:
http://computingsecurityawards.co.uk/?page=csa2017vote
Interesting News Items This Week
Insider Threats Account for Nearly 75 Percent of Security Breach Incidents:
https://securityintelligence.com/news/insider-threats-account-for-nearly-75-percent-of-security-breach-incidents/
‘Onliner’ bot can bypass spam filters:
https://www.theverge.com/2017/8/31/16232144/onliner-largest-malware-spambot
Mystery surrounds malware attack that forced German state parliament offline:
https://www.tripwire.com/state-of-security/featured/german-parliament-malware-mystery/
This giant ransomware campaign just sent millions of malware-spreading emails:
http://www.zdnet.com/article/this-giant-ransomware-campaign-just-sent-millions-of-malware-spreading-emails/
Comparitech Discovers Phishing Scam Targeting Bitcoin Users:
http://www.itsecurityguru.org/2017/08/31/comparitech-discovers-phishing-scam-targeting-bitcoin-users/
US government site was hosting ransomware:
https://threatpost.com/us-government-site-removes-link-to-cerber-ransomware-downloader/127767/
An Instagram hack hit millions of accounts, and victims’ phone numbers are now for sale:
https://www.theverge.com/2017/9/1/16244304/instagram-hack-api-bug-doxagram-selena-gomez
Insider Threats Account for Nearly 75 Percent of Security Breach Incidents:
https://securityintelligence.com/news/insider-threats-account-for-nearly-75-percent-of-security-breach-incidents/
‘Onliner’ bot can bypass spam filters:
https://www.theverge.com/2017/8/31/16232144/onliner-largest-malware-spambot
Mystery surrounds malware attack that forced German state parliament offline:
https://www.tripwire.com/state-of-security/featured/german-parliament-malware-mystery/
This giant ransomware campaign just sent millions of malware-spreading emails:
http://www.zdnet.com/article/this-giant-ransomware-campaign-just-sent-millions-of-malware-spreading-emails/
Comparitech Discovers Phishing Scam Targeting Bitcoin Users:
http://www.itsecurityguru.org/2017/08/31/comparitech-discovers-phishing-scam-targeting-bitcoin-users/
US government site was hosting ransomware:
https://threatpost.com/us-government-site-removes-link-to-cerber-ransomware-downloader/127767/
An Instagram hack hit millions of accounts, and victims’ phone numbers are now for sale:
https://www.theverge.com/2017/9/1/16244304/instagram-hack-api-bug-doxagram-selena-gomez
Cyberheist 'Fave' Links
This Week's Links We Like, Tips, Hints and Fun Stuff
- Nicole Smith has the 'most incredible jump of her life' when she gets the opportunity to launch out of a Fox Acrobatic Glider in Dubai:
http://www.flixxy.com/skydiver-ejects-from-glider.htm?utm_source=4
- And while we are up there, an eagle carrying a camera gives us a stunning bird's eye view of the Nebelhorn mountain in the Allgäu Alps in Germany:
http://www.flixxy.com/flying-eagle-point-of-view-of-the-german-alps.htm?utm_source=4
- More birds: Starlings Perform Awesome Aerial Acrobatics to Escape a Falcon:
http://www.flixxy.com/starlings-peform-awesome-aerial-acrobatics-to-escape-a-falcon.htm?utm_source=4
- An amazing Rube Goldberg machine made in Japan with many complex features, including a rotating whiteboard. The Japanese commentary is a riot:
http://www.flixxy.com/amazing-japanese-rube-goldberg-machine.htm?utm_source=4
- OK, Who -Is- This Stu Guy Anyway? [VIDEO] I had a freelance video PR crew follow me one day at Black Hat, to give you an idea of who the heck I am:
https://blog.knowbe4.com/ok-who-is-this-stu-sjouwerman-guy-anyway-video
- "I wore a Mars space suit and it was exhausting."
https://youtu.be/R3O9TgZwMuE
- Elon Musk Just Shared Footage of a Hyperloop Accelerating to 200 Mph and Holy Crap:
http://www.sciencealert.com/elon-musk-just-shared-footage-of-a-hyperloop-accelerating-to-200mph-and-holy-crap - Magician Mat Franco pours six different drinks - coffee, lemonade, orange juice, beer, wine and water - from one milk carton:
http://www.flixxy.com/mat-franco-returns-to-americas-got-talent-with-milk-carton-magic.htm?utm_source=4





