.jpg)
Chinese Phish All Identities of NSA, CIA, FBI and more...
For a day or so I was puzzled that the Anthem hack trail led to China. This would normally be a Russian operation. Then an insider told me that most of the three-letter U.S. Government agencies have their employees insured through Anthem's Blue Cross Blue Shield and then the whole thing fell into place.
The Chinese now own the identities of all the people fighting them, and can use this in a multitude of social engineering scenarios. No wonder that many people in the Government have steam coming out of their ears about the Anthem hack. Cyberwar has suddenly become -very- personal to them.
This may be why President Obama last Friday signed an executive order that will nudge private companies to share data about cybersecurity threats between each other and with the federal government.
Apart from the fact that the cost of the Anthem data breach are likely to smash $100 million barrier, it's surprising that Anthem did not encrypt SSN's which allowed wholesale identity theft of thousands of American cyberwarriors.
Wonder why hackers are going after healthcare records these days? They are much more valuable because they stay active for several months after a hack, as opposed the credit card numbers which quickly get nixed after a few days.
Since Anthem is a healthcare company, you would expect them to take HIPAA compliance to the max and even top the required controls with higher standards. As we all know, compliance does not equal security, but it establishes a basline at the very least.
Becoming HIPAA compliant and staying that way is a challenge to say the least. The KnowBe4 Compliance Manager can help you with that. Fill out the form to get a webdemo or a 30-day trial:
https://info.knowbe4.com/knowbe4-compliance-manager_lp_14-04-15
Scam Of The Week: Microsoft Volume Licensing
Watch it! The bad guys are going after YOU this time. There is a phishing scam doing the rounds which sends you malware "from Microsoft" about your Volume Licensing that evades sandboxes and contains a Word doc which has macros inside and leads to a possible malware infection.
Following the instructions in the phishing email results in Chanitor being downloaded, which is used to download other malware. Corporate users are phished from Microsoft Volume Licensing Service Center (VLSC), according to researchers with Cisco.
A screenshot of the phishing email – which asks recipients to click on a link to download VLSC registration details – was included in a Monday post by Martin Nystrom, senior manager for Cisco Managed Threat Defense. He wrote that the message is very similar to the real email sent by Microsoft.
The link in the email appears to be for a Microsoft website, but Nystrom points out that hovering over it with the mouse reveals the true URL. Clicking on it will result in the authentic VLSC login page opening, but will also trigger a ZIP file to download that recipients may not notice is being delivered from a different website.
The ZIP file contains a Windows executable with a SCR extension – a screensaver file – and opening it results in the system being infected with Chanitor, which is used to download other malware, Nystrom wrote. This is the link to the full post:
https://blogs.cisco.com/security/fake-volume-license-trojan-targets-corporate-users-and-evades-sandboxes
Warm Regards,
Stu Sjouwerman
Quotes of the Week:
"Find something you're passionate about and keep tremendously interested in it." - Julia Child
"Passion will move men beyond themselves, beyond their shortcomings, beyond their failures." - Joseph Campbell
New KnowBe4 Console V4.0 Released
We are excited to announce Version 4.0 of our console with some exciting new phishing features! Here are two highlights but there are many more. As you know we regularly survey our customers and #1 was the by far the most requested feature.
- Random phishing emails chosen from multiple campaigns, at random times over 24-120 hour period, where you can exclude weekends. We call this the "anti-prairie dog" feature because this prevents employees popping up from their cubicle from warning each other a test is going on.
- Targeted spear-phishing campaigns; the ability to replace certain fields within email templates similar to marketing emails that have [[first_name]] [[last_name]] fields that are populated dynamically for each recipient. We can do this now for our phishing emails based off of the information located in the Account profile and User profile. Available for both landing pages and email templates.
Check out these cool new features in your Management Console, and here is a full write up of the 10 new features of V4.0 at our blog:
https://blog.knowbe4.com/new-knowbe4-console-v4.0-released
What Are Our Customers Saying?
"Our bank has used your product for the last three years and I feel it is one of our BEST frontline security defenses. I have seen a dramatic increase in employee security awareness through the online training and phishing tests. I feel like a KnowBe4 evangelist when I am at any type of event." - L.S. AVP/Information Security Officer
"I think the random sending feature is great and I did not realize it went live yesterday! I logged in this morning to setup another campaign for the month of March and realized it was there, then received your email. Now I can setup one campaign for the entire firm and still prevent employees from asking each other. This will help them to think on their own." - B.D.
Anthem Hack Caused By A Phished System Admin?
The foreign hackers who stole up to 80 million records from Anthem social engineered their way into the company's network by obtaining the credentials of five tech workers. Thomas Miller, the Anthem's chief information officer said the first sign of the attack came when a systems administrator noticed that a database query was being run using his identifier code although he hadn’t initiated it.
Forensics Team Says "Phishing"
The Mandiant forensics team that was called in to investigate the hack now believe the criminals got in through by phishing which tricked the five tech workers into unknowingly revealing a password or downloading a Trojan with a keylogger software.
At this point it is thought that the system administrator who was social engineered took over a month to notice that his own credentials were being used. This shows a significant lack of security awareness, as well as a lack of good audit practices. An insider told me it's especially painful for the U.S. Government as all their 3-letter agencies are insured via Anthem. Imagine the Chinese having all the CIA health records.
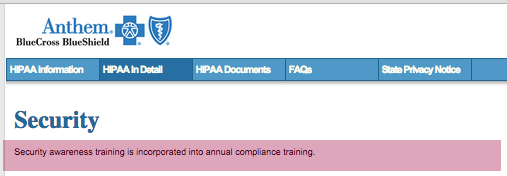
To quote Anthem's website, "Security awareness training is incorporated into annual compliance training," which means that there is no continual security awareness training, and that's not cutting it as we continually see (Home Depot, Target). This picture is a screen shot from the Anthem website:
If you want to spend less time putting out fires, get more time to be proactive, and get the things done you know need to be done, step employees through effective security awareness training. It will help you prevent this kind of disaster or at least make it very hard for the bad guys to social engineer employees. Find out how affordable this is for your organization. Get a quote now:
https://info.knowbe4.com/kmsat_get_a_quote_now
Antivirus Products Are Slow at Making Malware Signatures
The traditional malicious software detection approach is far from being sufficient, especially in corporate environments. More and more it's found that antivirus products can take months before adding the algorithms to recognize the more complex threats.
A recent study from Damballa, a security company offering solutions against advanced cyber threats, revealed that malware could spend as much as six months on a system before it is identified using signature-based detection.
Damballa's CTO Brian Foster said: "For years now the industry has discussed the declining effectiveness of preventative controls like antivirus, firewalls and IPS. These technologies simply do not work against polymorphic malware, which is used by nearly all of today’s advanced attacks. And yet RSA estimates that most organizations still spend about 80% of their security budgets on prevention technologies.
Damballa wanted to demonstrate the limitations of a prevention-centered approach to malicious software. They analyzed a sample set of tens-of-thousands of files sent to them by their customers. The files detected as malicious by their own Failsafe system were also scanned by the four most commonly deployed antivirus products. Here’s what they found:
- Within the first hour, the antivirus products missed nearly 70% of the malware
- After 24 hours, still only 66% of the files were identified as malicious
- At the seven-day mark, the accumulated total was 72%
- After one month, 93% of the files were identified as malicious
- More than six months passed before 100% of the malicious files were identified malware-alerts-per-week Courtesy Ponemon
A 2015 Ponemon Institute report shows that the average enterprise gets 17,000 malware alerts weekly, or 2,430 daily, from IT security products. Based on the Damballa study you can do the easy math; antivirus products miss 796 malicious files on Day One.
And now combine the data from Damballa, RSA and Ponemon. You come to the shocking discovery that 80% of the security budget is spent on controls that are missing 796 malicious files a day.
Many of these infections are caused by end-users who click on a malicious ad, click a bad link or open an infected attachment.
We all have limited budget and manpower. Nobody can afford to dedicate the majority their budget to failing controls. You need to defend your networks in depth, and get proactive instead of continuing to run around putting out fires. The Ponemon graph shows the lost time caused by infected devices.
The very first step in getting proactive is deploying effective security awareness training combined with simulated phishing attacks. Prevention that really works is more important than ever, and end-user education gives you the best bang for your budget buck, but you also need to put greater emphasis on deeper defense-in-depth levels with detection and response. If you can reduce the time between the initial infection and its discovery and remediation, you reduce your risk of damage.
The first thing though would be to step your users through security awareness training combined with simulated phishing attacks to keep them on their toes with security top of mind. It's a must these days.
Cyberheist 'FAVE' LINKS:
This Week's Links We Like. Tips, Hints And Fun Stuff.
Boston dynamics has a smaller version of the quadruped Big Dog, nimbler and pretty impressive. They can run in packs and run off a battery so they are much more quiet. This is getting very interesting!
https://youtu.be/M8YjvHYbZ9w
Infographic from 1931 depicting 4000 years of world history. It's obviously behind, but fascinating nonetheless:
http://tinyurl.com/megu958