 Ransomware authors are realizing the benefit of either stealing data or just implying they have and threatening to publish the data publicly in order to increase their chances of being paid.
Ransomware authors are realizing the benefit of either stealing data or just implying they have and threatening to publish the data publicly in order to increase their chances of being paid.
It’s a brilliant and simple twist in the ransomware evolution story; since you already have access to most of a network’s data to encrypt it, why not steal some of the data as well to up the payment ante? It started with Maze ransomware late last year. Then other ransomware gangs, like DoppelPaymer, joined in. Soon, it became so desirable, Maze formed a cartel of sorts where as many as 10 ransomware variants now use this tactic and even share a common publishing platform hosted by Maze.
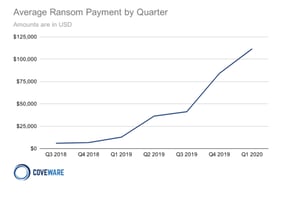
Quickly becoming the new norm, new data from Coveware’s Q2 2020 Ransomware Marketplace Report sheds some light on just how bad it’s getting. According to the report in Q2 of this year:
- 30% of ransomware attacks involved a threat to release data (with no confirmation that data was actually stolen)
- 22% of attacks actually involved confirmed exfiltrated data – this is up from 8.7% in Q1, a rise of 152%
- Both Maze and DoppelPaymer variants had multiple months in both Q1 and Q2 of this year where 100% of their attacks involved data exfiltration
- Payment “defaults” (where data cannot be decrypted) remains low, at 2%
With downtime post-attack already at 16 days (according to Coveware), the added threat of an organization’s data being published or sold on the dark web makes the remediation of this attack particularly complex and costly.
It’s time to realize a few things:
- Ransomware is now the attack to worry about.
- Security solutions aren’t currently stopping all attacks and there’s no sign they will in the near future.
- Email phishing is the #1 attack vector in attacks against organizations 100 employees or greater (according to the report).
- Your users need to play a role in your organizational security by putting lessons learned via Security Awareness Training into practice, being mindful when interacting with email and the web, and not engaging with suspicious content that may have malicious intent.
This new data should be enough to scare you into believing when you become a victim of a ransomware attack, cleaning up the mess isn’t going to be pretty and you’re likely going to be forced to pay the ransom, whether you can remediate the encrypted data or not.
 Here's how it works:
Here's how it works:




