 New analysis shows sources of cryptocurrency being placed into mining pools with huge deposits that make it easier for cybercriminals to make their ransom funds untraceable.
New analysis shows sources of cryptocurrency being placed into mining pools with huge deposits that make it easier for cybercriminals to make their ransom funds untraceable.
One of the core concepts of a blockchain is that every transaction is documented within the blockchain itself. So, it makes sense that we’d all think that even if ransomware threat actors receive their ransom in some form of cryptocurrency, the funds would be traceable, and potentially law enforcement officials would be able to tie the crypto addresses to someone in the real world.
But new data from blockchain analysis firm Chainalysis shows that over the past 5 years, the amount of crypto from known ransomware addresses sent to crypto mining pools has skyrocketed. Anytime crypto is sent to a service, it’s mixed in with all other submitted funds, making it impossible to track where funds leaving the pool originally came from.
In essence, crypto services like mining pools are laundering ransomware gangs’ money.
According to the data, the amount of money in crypto placed into these mining pools was as little as $10,000 back in Q1 of 2018 and has grown to over $10 million in Q1 of this year (the yellow line in the graph below). That’s literally 1,000 times larger, or 100,000% growth over 5 years!
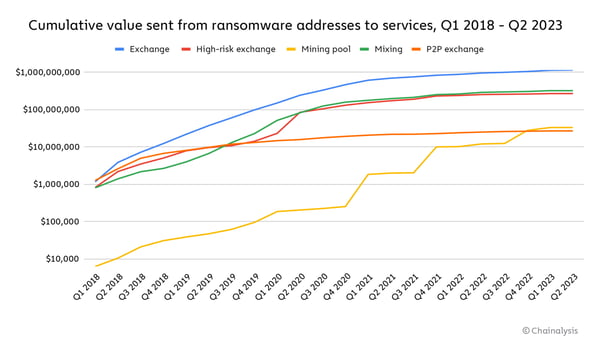
Source: Chainalysis
What this means for the average organization is that ransomware gangs have found a sufficient means to “clean” their funds and avoid being traced when they take their funds out.
In short, ransomware is still profitable.
With phishing still topping the list of initial attack vectors for ransomware, it’s critical that your security controls around email (which should include Security Awareness Training for your employees) is robust and effective in stopping malware-based, malwareless, and social engineering attacks coming in via email.
 Here's how it works:
Here's how it works:




