The Russian 800-pound gorilla Dridex Banking Trojan gang who are also behind the Cerber ransomware have just upped their game. Cerber is part of the small set of professional ransomware families that gets updated at a furious pace in an attempt to gain (criminal) market share. Cerber now comes with new capabilities that allows the Dridex gang to steal data from three Bitcoin wallet apps — the Bitcoin Core wallet, the Electrum wallet app and the Multibit wallet app.
This new Cerber flavor is also able to steal saved passwords from popular web browsers, including Internet Explorer, Google Chrome, and Mozilla Firefox.
Trend Micro security researchers said that while stolen browser passwords may help the cyber criminals hijack victims' accounts, the stolen data from Bitcoin wallets is only the first step: "Theft of these files does not assure that the stored Bitcoins can be stolen. The thief would still need to get the password that protects the wallet in question," Trend Micro researchers said in a blog.
Cerber's criminal coders have been working hard to avoid detection. Last year, just a day after a Cerber decryption tool was issued out by Check Point security experts, they updated Cerber which made the decryptor useless.
Trend Micro also said that just in May this year, Cerber underwent six different upgrades. "Cerber ransomware has acquired the reputation of being one of the most rapidly evolving ransomware families to date. This new feature shows that attackers are trying out new ways to monetize ransomware," .
Some details of Cerber haven’t changed, though. It still arrives via phishing emails with an attached file:
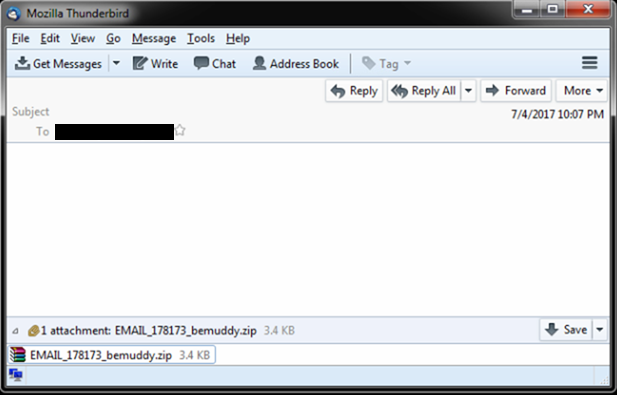
Solutions and Best Practices
Trend Micro noted: "Cerber’s entry vector onto systems didn’t change, so known best practices against it would still work. Educating users against opening attachments in emails from external or unverified sources would lower the risks; system administrators should also consider email policies that strip out such attachments."
We could not agree more.
KnowBe4's integrated training and phishing platform allows you to send emails with Office attachments and see who opens them up, and even if they click on the "Enable Editing" button which could activate malicious macros and infect the network with ransomware.
 Here's how it works:
Here's how it works:




