When we talk with folks outside the security industry about what we see from the bad guys on a daily basis, we often get the response, "Wow! That's really sneaky." And it's true. The bad guys are nothing if not sneaky. Spoofed domains. Fake Paypal notices. Word documents loaded with macro-based malware tripwires. Malicious actors impersonating corporate CEOs. It's all very sneaky.
This morning, however, we encountered a credentials phish (forwarded to us by an alert customer through the Phish Alert Button) that brought a very different word to mind. That word is brazen.
Let's take a look.
When No One is Looking
The phish in question is a fairly straightforward credentials phish. It starts with this email:
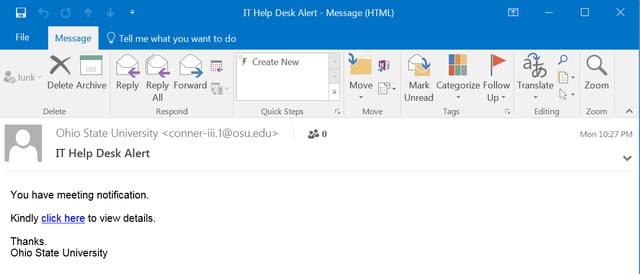
Anyone half-awake should be asking questions based on just a cursory glance at this email.
- It purports to originate from an "IT Help Desk Alert" account, yet the listed email address appears to be a personal email address (and, from the headers we inspected, likely associated with a compromised account).
- The message in the email body is not only strangely terse but awkwardly lacking an indefinite article (should read: "You have a meeting notification.").
- The message is signed simply "Ohio State University," with no other identifying information about the scheduling system that presumably generated this notification.
There are plenty of users, however, who won't notice these red flags and will go right ahead and click the supplied link to "view details." With that click their browsers will open this pixel-perfect lift of the actual email login page for faculty/staff at Ohio State University.
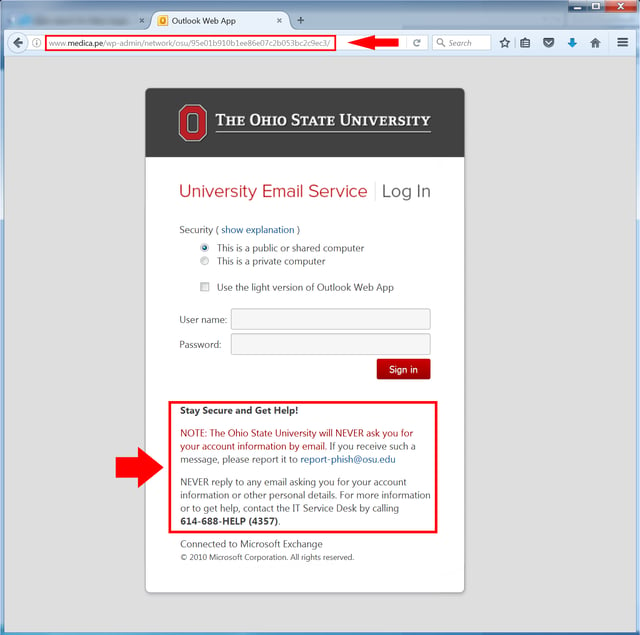
We've highlighted the key elements. First, the URL tells us very clearly that we are not at osu.edu (a domain anyone working there should recognize and be looking for).
Second, the bad guys didn't even bother to remove or edit the security notice warning users against phishing attacks. The provided email address/link to report phishing attacks is real and working. The listed phone number for the OSU IT Service Desk is real. And it's all there on a malicious web page being used to phish users.
That's the very definition of brazen.
The bad guys simply had no qualms about including all that information in this phishing page. Why? Because they can be fairly confident that no one is paying any attention.
And that's why simple phishes like this one continue to work day in and day out.
Stop. Look. Think.
Most phishes we see are surprisingly simple to recognize and defeat. All it takes is a user who is paying attention -- a user who takes a second or two to stop, look, and think before taking any action in response to a social engineering hook.
Habit dulls the senses and allows alarming attacks on the security of your organization to hide amidst the jungle of familiar-looking details that are daily office life. Your users need to be shaken out of the lazy habits that let them click past obvious red flags and right into sneaky traps set by the bad guys.
New school security awareness training is all about teaching your users new and better habits and motivating them to open their eyes and pay attention when malicious emails like this one land in their inboxes.
Since phishing has risen to the #1 malware infection vector, and attacks are getting through your filters too often, getting your users effective security awareness training which includes frequent simulated phishing attacks is a must.
KnowBe4's integrated training and phishing platform allows you to send attachments with Word Docs with macros in them, so you can see which users open the attachments and then enable macros!
See it for yourself and get a live, one-on-one demo.
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





