
Top 5 System Admin Hate Votes
May 22, the question was asked on Spiceworks: "What is your IT-related Arch Nemesis?", more than 200 random replies came in. I thought it would be interesting to know what the top ones were. I tabulated (and somewhat normalized) the main things that generate support tickets and most of the system admins came back and voted on which things they HATED the MOST!
The Top 5 most mentioned things they HATE are in sequence of percentage:
1) No Documentation: 29.7%
2) Users: 27.4%
3) Printers and Apple products tie with 25.5% each
4) Fake Antivirus: 24.5%
Some other observations: You seem not to mind Microsoft Exchange very much, (kudos for Microsoft) and driver problems seem to have subsided over time. Java is still causing a lot of headaches with 21.2% as the most hated item. Here is the graph: 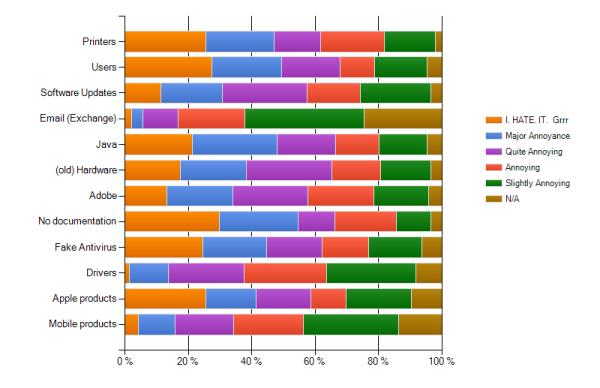
Windows XP End Of Life Security Issue
As we all know, XP will no longer be supported April next year. There will be no new security updates, non-security hotfixes, free or paid assisted support options or online technical content updates. But many of us are forced to keep XP machines running after the deadline. I have a possible solution I'd like your feedback on. Please take 3 minutes and fill out this survey? I will report back the results in a coming issue.
Thanks in advance!!
https://www.surveymonkey.com/s/XPEOL-APPCTRL
Facebook Scams Of The Week
Since you are in IT, you or your webmaster may have been tasked to manage your organization's Facebook Page. This phishing scam specifically targets -you- with an email from 'Facebook Security.'
The scammers try to trick Page owners into starting a 'Fan Page Verification Program.' You are asked to share your Facebook Page’s URL, login creds and create a 10-digit number as a 'Transferring Code.' Once you have done this, they can now post links for your followers which trust you as a source.
Oh, while we are talking Facebook, cybercriminals are now using the following trick. They clone a whole profile, befriend the victim's friends and use their trust to defraud them.
Cloned accounts can be used to send spam messages, initiate scams, and steal personal information that could be used for more serious identity theft. In the recent cases, there are reports that once the cloned account's repeated and fraudulent friend request has been accepted, the scammer starts soliciting money from 'friends'. Warn your users to use Real Life verification before they agree to any transaction over Facebook.
Quotes of the Week
"I need new haters. The old ones started to like me" - T-shirt in Tampa
"Expect while reaching for the stars, people to whirl by with their dark clouds and storm upon you." - Anthony Liccione
|

NEW: 'Attack' Your Own Users
 Since the survey shows that users indeed are a pain in your neck, here is something you can do that is both useful and a bit of fun. Over here at KnowBe4, we call it the one-two punch. Since the survey shows that users indeed are a pain in your neck, here is something you can do that is both useful and a bit of fun. Over here at KnowBe4, we call it the one-two punch.
ONE: We run the (free) Email Exposure Check for you. That gives you all the email addresses out there available on the Internet from your own domain. It's often surprising how many addresses can be found and whose.
TWO: You create (again free) an account on our website, upload the addresses found in step ONE, and 5 minutes later they receive a simulated phishing attack! You will immediately know your phishing attack surface and the Phish-prone percentage of the highest risk employees. Fabulous ammo to get more security budget and fun to do!
Sign Up For Your Free Email Exposure Check Now:
https://info.knowbe4.com/email-exposure-check

Seven Deadly Social Engineering Vices REDUX
We made it on the Spiceworks front page with that article which has gone viral. Thousands of system admins said that they were going to send that blog post to their execs and users. I recommend you do the same. There are two options:
- Give them the link to the KnowBe4 Blog (which has a fun image)
- Repurpose the copy and send it as your own, which you are welcome to if at the end you mention the source.
Keep those users on their toes with security top of mind!
https://blog.knowbe4.com/bid/290552/The-Seven-Deadly-Social-Engineering-Vice
Mobile Threats Now Outpace PC Attacks
Tracy Kitten over at Government InfoSecurity interviewed Dave Jevans, the founder and chairman of the Anti-Phishing Working Group. (APWG)
Attacks aimed at mobile devices are progressing much more rapidly than any attacks ever waged against PCs. Organizations are in danger if they don't pay attention. Over the past six months, the APWG has analyzed emerging mobile security threats and pinpoints some of the key vulnerabilities, such as jail-broken devices, open-source OSen and sophisticated malware baked into rogue mobile applications.
Jevans, founder and chairman of the APWG, says criminals are increasingly targeting mobile devices, building on their decades' worth of experience through attacks waged against PCs.
"The big message here, as you look through the report, is that malicious and fraudulent activity on the mobile platform is growing much more quickly than it did on the PC platform over the last 10 years," Jevans says. More:
https://www.govinfosecurity.com/interviews/mobile-threats-outpace-pc-attacks-i-1940?

Cyberheist 'FAVE' LINKS:
* This Week's Links We Like. Tips, Hints And Fun Stuff.
Holy $#!T. This is -rendered-. Wow, this Activision R&D Real-time Character Demo almost has everything right: skin, muscle, lighting, and eyes. But the teeth? That demo needs to see a dentist ASAP. LOL:
https://www.youtube.com/watch?v=l6R6N4Vy0nE
For hardware/security nerds: Security Breach Team - The Combination Reclamation Device - Wowthisguyistalkingfast!
https://www.youtube.com/watch?v=8byAOaIM1cY&feature=youtu.be
|

