 Malicious actors continue to probe organizations' security and defenses with malicious emails explicitly crafted to create and exploit sense of panic in the wake of the COVID-19.
Malicious actors continue to probe organizations' security and defenses with malicious emails explicitly crafted to create and exploit sense of panic in the wake of the COVID-19.
Over the past two weeks bad actors pushing malicious files and links have threatened to infect users who fail to cough up a Bitcoin ransom, warned users they may be infected with the Coronavirus, dangled fiscal stimulus money in front of them, and instructed employees working from home that they need to complete a bogus "process" in order to connect to their organization's network.
Users who failed to bite on any of these often hair-raising social engineering schemes are now contending with a yet another bracing claim from malicious actors: your organization's facilities are being shut down on order of the CDC.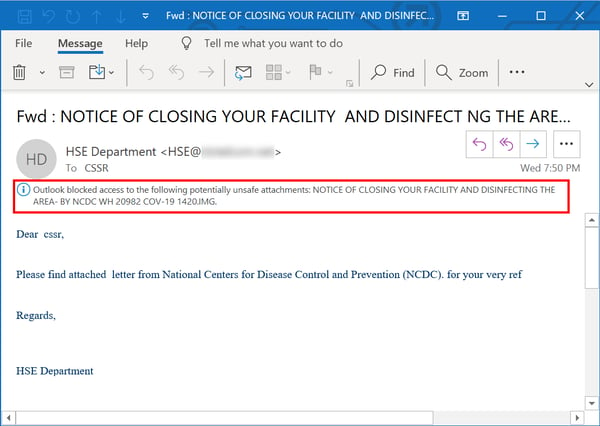
The full Subject: line for this email is rather long-ish: "Fwd : NOTICE OF CLOSING YOUR FACILITY AND DISINFECT NG THE AREA - BY NCDC WH 20982 COV-19 Due To Recent Corona Virus COVID-19 Pandemic." Perhaps the bad guys here were going for something strikingly bureaucratic and wordy in order to give it the flavor of an official government missive.
By contrast the email body itself is calm, brief, and to the point, referencing an alleged letter from the NCDC (National Centers for Disease Control), a favorite target of spoofed phishing emails over the past few months. Given the nature of the alarming "news" here, we fear that senior executives within some organizations could be particularly prone to opening the attachment without thinking through the potential consequences.
Make no mistake about it: the consequences of opening the attached "letter" are indeed severe. That attachment is in fact a malicious executable wrapped in an .IMG file -- a disk image format that has enjoyed some popularity with malicious online groups over the past year. At present only half of the engines represented on VirusTotal are detecting this backdoor trojan.
Outlook appears to be blocking the attachment based on the file format alone, although this list of blocked attachment types from Microsoft does not include .IMG files. (Note, however, that Outlook also began blocking similarly used .ISO files sometime last year and they are not listed either.) Whether other email clients -- be they locally installed or web-based -- are blocking this malicious attachment is not known.
Conclusion
The bad guys pushing these kinds of alarming phishing emails seem to have settled on a simple social engineering tactic that is the digital equivalent of yelling "fire" in a crowded theater in order to stampede panicked users into opening the door to your organization's network.
To keep your users calm and safe, you need to be educating and training them to expect these kinds of phishing attacks, recognize them for what they are, and handle them safely. Organizations that fail to do so really could be facing unexpected downtime -- and it won't be be on account of the Coronavirus or even the CDC.
 Here's how it works:
Here's how it works:




