At the heart of almost every phishing email is a spoof. In malicious emails spoofing is the art of deceptively imitating something or someone trusted by users in order to gain their confidence. And malicious actors incorporate this element of deception into everything they do for the purposes of social engineering unwitting users into taking dangerous actions -- usually clicking malicious links, opening malicious attachments, or providing access to money and information under false pretenses.
Your basic email provides bad actors with a number of opportunities to generate trust with users through spoofing. They spoof sender names and email addresses. They spoof trusted online brands like Microsoft, Google, and Docusign through email design and formatting. They even spoof the existence of email attachments through fake graphics designed to disguise links to external web sites.
How to Be a Bad Guy 101: Spoofing Links
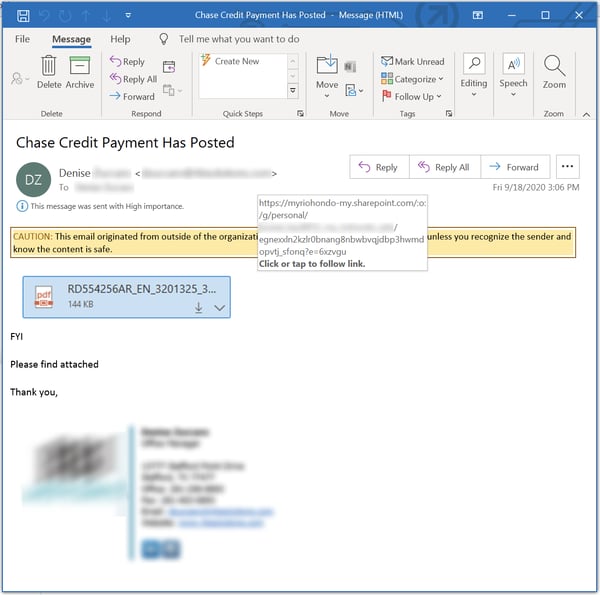
Among the most common email elements that malicious actors spoof are links -- URLs presented to users in the email body. Users see the text for an apparently innocuous link, but the underlying URL actually takes them somewhere completely different and quite malicious.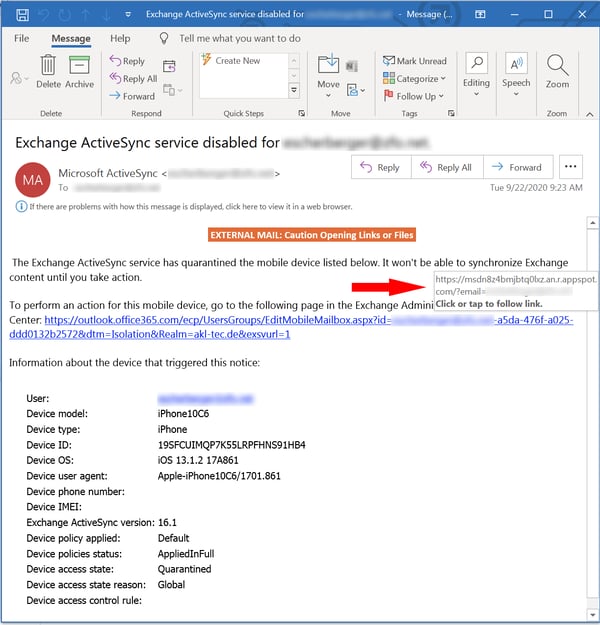
In the above example the URL visible to the user appears to link to outlook.office365.com, a trusted Microsoft site. In reality the link takes unwitting users to a malicious page hosted on Google's Appspot.com. This kind of deception is a bread-and-butter, Bad Guy 101 phishing technique.
Like most forms of spoofing, however, such deceptively presented links can be defeated by alert users trained to look for spoofed email elements and recognize them as "red flags." That's why most security awareness training programs teach users to hover their mouse over links in order to reveal the true destination or actual URL, as in the example above.
Indeed, "link hovering" is one of the most concrete and effective techniques we teach users in order to sniff out malicious emails.
When Everything's a Con
As it turns out, though, the bad guys have a counter to link hovering. After spoofing the link, they simply spoof the link hover text as well. Pay close attention to the two different URLs presented in this malicious fake fax email sitting in a Gmail inbox.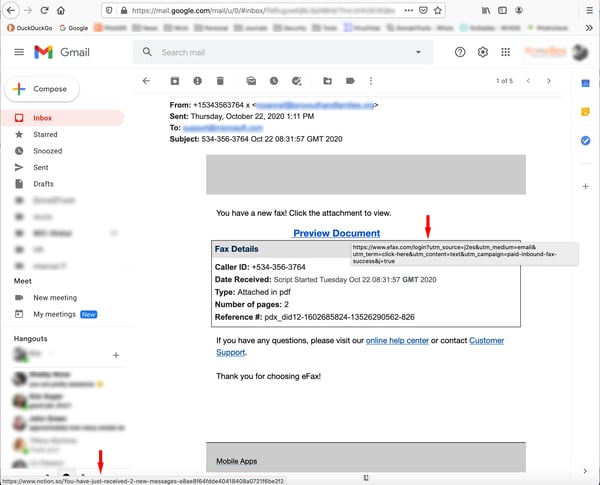
With the mouse pointer hovering over the hyperlinked "Preview Document" text, the browser displays the actual underlying URL -- which is entirely malicious -- in the bottom left corner of the browser. What users see immediately below that text, however, is a mouseover text that points to an innocuous eFax.com URL.
Even diligent and attentive users could be fooled by this bit of trickery. And, unfortunately, it's surprisingly easy for malicious actors to spoof link hover texts in just this manner. Here's the relevant portion of the email body's HTML (decoded from base64):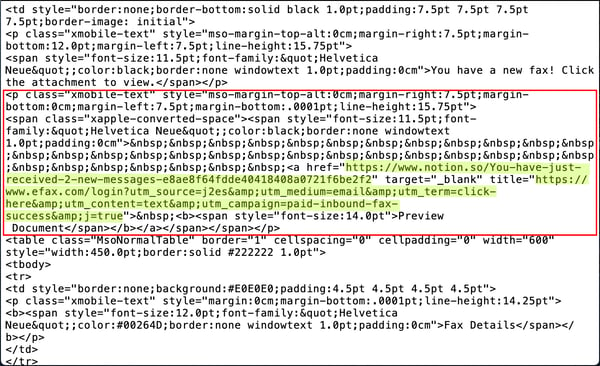
As you can see, it's all done with basic HTML. No Javascript required. That spoofed link hover text is merely a mouseover text label that enjoys the advantage of being presented to users immediately adjacent to the link being checked. The real URL, by contrast, is presented outside of the user's immediate visual focus, off to the side and all the way at the bottom of the browser.
This trick works in other web-based email clients as well. Here's the same malicious email sitting in an inbox for Roundcube, a free/open source webmail client.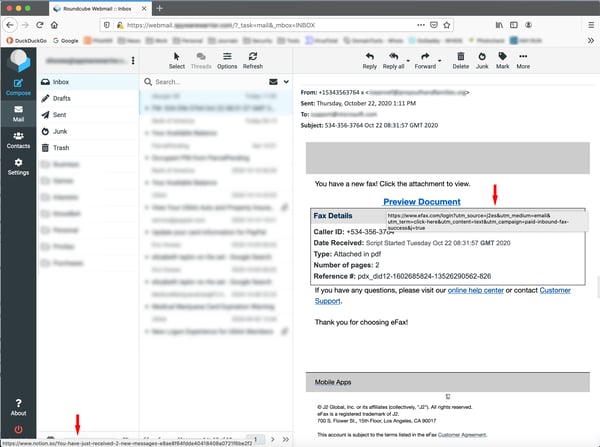
If there is any good news to report, it is that this malicious trick appears to work only in web-based email clients where link hovering can produce both a standard link preview at the bottom of the browser as well as a deceptive mouseover text label with a spoofed URL.
Desktop email clients like Microsoft Outlook and Apple Mail, by turns, tend to present the link hover text immediately adjacent to the link itself. Again, here's the same phishing email sitting in an Outlook inbox.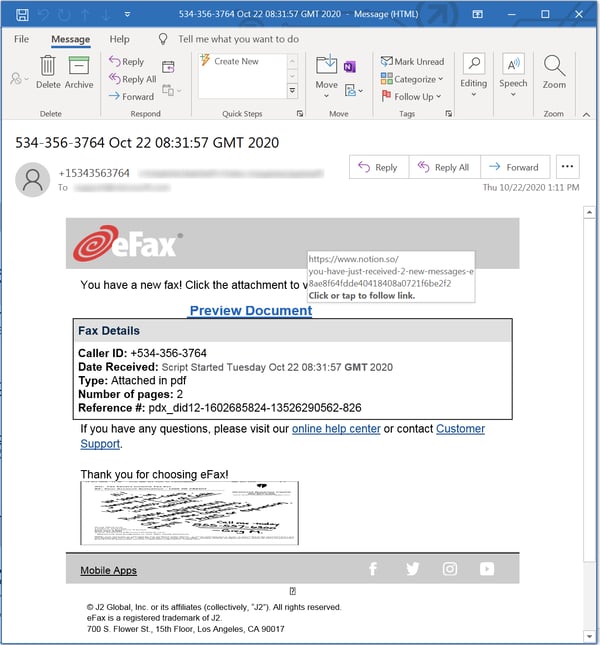
In contrast to the webmail clients, Outlook shows users only one URL -- the actual malicious URL.
Conclusion
Link hovering can be an incredibly useful technique for spotting "red flags" in phishing emails. But users of webmail clients like Gmail (part of Google Workspace, formerly known as G-Suite) need to be trained to look for the link hover text in the correct location in the browser.
Spoofed link hover texts are just one of the many techniques developed by malicious actors to trick your users into opening the door to your network. And they use these forms of deception because your users are at once the weakest element of your organization's security posture as well as its last line of defense.
That's why your users need to be stepped through New-school Security Awareness Training and regularly tested with quality simulated phishing emails modeled on actual malicious emails in the wild.
 The Training Preview includes:
The Training Preview includes:
