You need to know about a new phishing attack vector reported by our friends at Barkly. It utilizes a new technique that's just plain nasty.
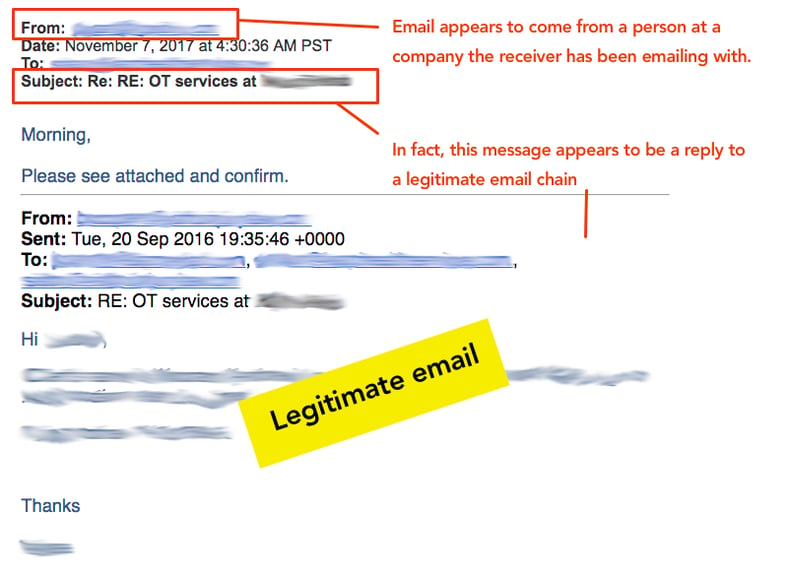
This week, users at one of their customers began receiving emails from known contacts they had at another organization. In the screenshot below you can see that at least one of the emails appeared to be a reply to an existing email thread, where users at the two organizations had been emailing back and forth.
The new message was noticeably short — "Morning, please see attached and confirm" (you probably see where this is going) — but in the context of the email chain it was very convincing. The email appears to come from a person at a company the receiver has been emailing with, and this message appears to be a reply to a legit email chain. Yikes.
The aim was to have the user open the Word attachment, and follow instructions to enable macros.
Technical background of the attack
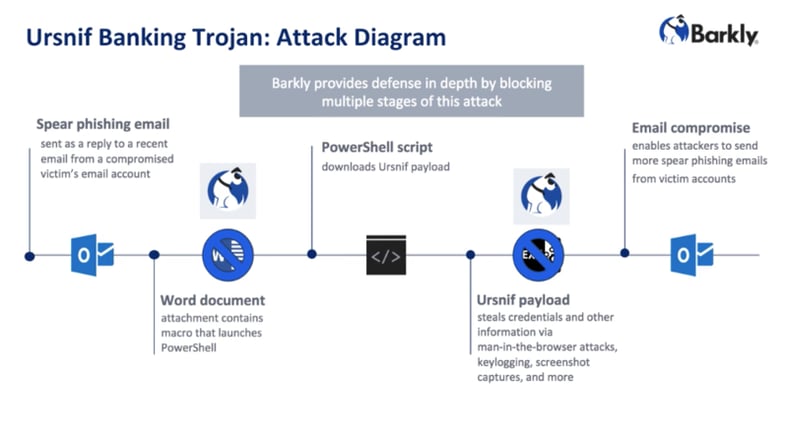
The user on the other end had been infected with a new variant of Ursnif, one of the most active and widespread banking trojans in the world.
Investigation showed that the Word doc the user downloaded contained a macro that, when activated, launched PowerShell script designed to download the Ursnif payload.
Ursnif is a powerful trojan with a lot of features like stealing victim credentials in a variety of ways via man-in-the-browser attacks, keylogging, screenshot capture, etc.
It looks like the evil masterminds behind Ursnif are now taking it one step further and use the compromised email accounts of its victims to spread the infection like a worm.
It's turning infected workstations into spam factories
What makes this social engineering attack so tricky is that the email pictured above wasn't just coming from an organization the recipient knew and had been emailing with, it came as a reply to an existing email chain. That is a hard one for a user not to fall for, they really need to be on their toes to catch this one.
Ursnif isn't the only trojan we've seen hijacking victim email accounts. In July, we saw the Emotet trojan doing something similar.
Now, compromised accounts have been a thing since email has been around, so getting a infected email from a trusted source is nothing new, but if this is becoming a larger trend it is even more important to mitigate before your own network starts spewing out malicious attacks and your mail server gets on blacklists.
What You Can Do About It
Here are some suggestions on how to block attacks like this using as many layers of your defense-in-depth as possible:
- Disable MS Office macros network-wide if possible
- Check your firewall rules to make sure this type of attachment is at least flagged as potentially dangerous or quarantined
- Configure your email servers/filters to block attachments containing VBA/Macro code
- Configure the endpoint security software on the workstation to catch malicious attachments
- Install a (free) Phish Alert button in Outlook, so users can simply click on that, delete the email and forward it to your Incident Response team
- Step your users through new-school security awareness training and send them simulated phishing attacks with Word docs that have Macros, to inoculate them against attacks like this when (not if) your filters do not catch them
Free Phish Alert Button
When new spear phishing campaigns hit your organization, it is vital that IT staff be alerted immediately. One of the easiest ways to convert your employees from potential targets and victims into allies and partners in the fight against cybercrime is to roll out KnowBe4's free Phish Alert Button to your employees' desktops. Once installed, the Phish Alert Button allows your users on the front lines to sound the alarm when suspicious and potentially dangerous phishing emails slip past the other layers of protection your organization relies on to keep the bad guys out.
Don't like to click on redirected links? Cut & Paste this link in your browser:





