.jpg?width=369&name=iStock-639646818%20(2).jpg) No matter how good your policies and technical defenses are, some amount of phishing will get to your end users in a given month. They must be trained to recognize social engineering attempts and how to treat them. Which is hopefully to report them to the appropriate people/groups and/or delete them.
No matter how good your policies and technical defenses are, some amount of phishing will get to your end users in a given month. They must be trained to recognize social engineering attempts and how to treat them. Which is hopefully to report them to the appropriate people/groups and/or delete them.
The vast majority of phishing emails are the standard variety, appearing from strange email addresses and pushing unexpected requests for login credentials or to open file attachments. Most of them are fairly easy to recognize if you have had a little training. A few times during the year, newer variants pop up and users must be trained to recognize the latest variants. But even then, the phishing emails are not that sophisticated and fairly easy, to the trained eye, to spot.
Advanced Email Phishing Attacks
But every now and then, a new class of phishing email comes out that does something truly new. Here are six types of phishing attacks I classify as “advanced”.
OAUTH Phishing
OAUTH stands for Open Authorization. It is a new, very widespread authorization standard that allows a participant to use one authenticated login account for multiple sites and services requiring authentication. Most of us have and use an OAUTH account without realizing that we are doing it. Any time you go to a website and it has little buttons allowing you to log in to the new site or service using your Facebook, Twitter, Apple, or Google account (see example below) instead of creating a brand-new log in, it is likely using OAUTH as its single sign-on solution.
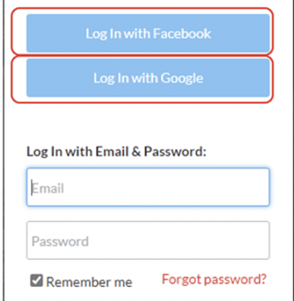
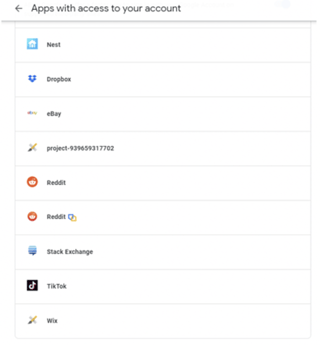
Attached to your OAUTH account on your OAUTH identity provider (again, Facebook, Twitter, Apple, Google, etc.) is a list of which sites and services you have allowed to use your OAUTH identity (see example below).
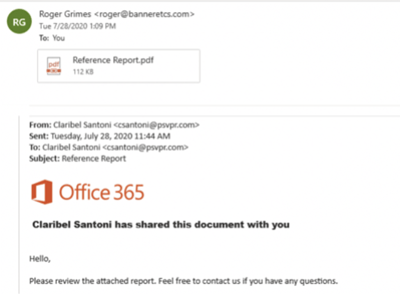
Sophisticated phishing emails, usually masquerading as Microsoft O365-related (see example below).
When the victim clicks on the file attachment, it opens up an OAUTH prompt that requests OAUTH access and permissions (see example below).
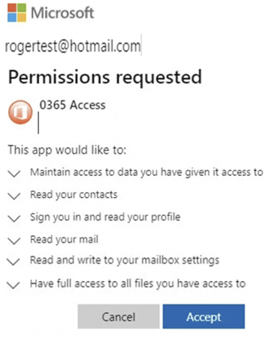
What most victims do not know is that when they click on the (default) Accept button, they are likely unintentionally allowing the new OAUTH requester (the phisher) to have those permissions to their OAUH account and related documents. Notice in the example above, they are requesting permissions to read the victim’s contact list, read the victim’s email, write to the victim’s email client, and have full access to all the files the victim has access to. That is a lot of power. And most of the time, all the victim did was click on a few buttons and the phisher’s malicious code and OAUTH did the rest.
It is a pretty insidious phishing attack. I previously wrote about OAUTH and OAUTH phishing in more detail here.
Compromised Trusted Third-Party Phishing
The most common security advice to potential victims to avoid phishing is for them to be suspicious of any unexpected email coming from a new email address. It is good advice and is often the first sign of a malicious email. But these days, hackers often break into a trusted business partner or friend’s email account (or social media account) and then use that new compromised location to send out fraudulent emails and links to that compromised victim’s contact list.
It is common for Facebook attacks coming from previously compromised friends to send pretend video links (see example below) which are really just a trick to get the new potential victim to download a Trojan Horse malware program.
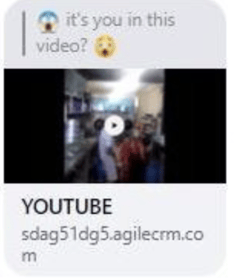
Compromised business email accounts are thoroughly reviewed by hackers to see what ongoing relationships and threads they can exploit. Then, the hacker sends a new email which seems as if it is in response to a previous email (i.e., the middle of a conversation) and asks the new potential victim to do something adversely, such as to pay a fake invoice, change payment information, or open a file attachment. Because the new victim often has a new and ongoing, trusted relationship with the previously compromised victim, the more likely they are to open the email and follow the instructions.
The old adage of being suspicious of unexpected emails from new email addresses does not apply. This is an unexpected email, but it is coming from a valid email address and a person with a previously recognized subject thread. I have spoken to many victims who said they were confused by the new request, but followed the instructions anyway simply because they trusted the sender.
Trusted third-party phishing is more difficult to avoid. So, here is what I tell end users now. Be extra suspicious of unexpected emails, even if it is coming from someone you trust, if it is asking you to do something brand new that you have never done before for them. You can no longer trust all emails just because they are coming from people you trust.
I previously wrote about trusted third-party phishing in more detail here.
Bypass MFA
I’m not sure if we will get to a world without passwords in the next decade, but more and more end users are using multi-factor authentication (MFA). Using MFA significantly reduces some forms of hacking, especially phishing emails which ask for a person’s password. If a person using MFA does not have or know their password, they can’t give it out accidentally.
But most people do not know that 90% of MFA solutions can be bypassed using what looks like a traditional phishing email. The phishing email arrives impersonating a brand or website that the user is familiar with, but the included links take the victim to a man-in-the-middle website, which proxies all information from the victim to the real website; and vice-versa. Anything the user types in is eavesdropped on and transmitted to the real website; and vice-versa. Thus, if the user is asked for their login name, PIN, or any MFA code, and they type it in, the hacker gets it as well and can use the information to log in as the victim to the real website. It is a very, very common hacking method – and it bypasses MFA like it was not even there.
Some forms of MFA, like FIDO2 tokens, have defenses that defeat proxy man-in-the-middle attacks, but most MFA is susceptible. To see a great video of this type of MFA bypass, go here or see the related blog article here.
Dynamic Phishing Kits
Most phishing emails are either very generic looking or tied to a particular well-known brand (e.g., Microsoft, etc.). Although not new, more and more phishing kits (bought and used by less sophisticated phishers) are generating dynamic, brand-related content on the fly that links to the domain the phishing email was sent to. For example, a phishing email sent to me is generated to appear as if it came from KnowBe4, Inc. It includes look alike domain name URLs, mentions KnowBe4 many times in the text, and contains KnowBe4 logos and branding. And if I click on one of the included malicious URLs, the website I am taken to contains the same. But instead of all that content being created beforehand, it is generated on the fly the moment I clicked on the URL.
Many of the dynamic examples only include branded text (see example below), but it is still enough to fool some potential victims.
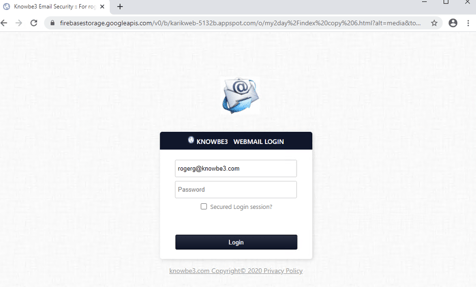
The key differentiator is that the phishing kit that sends out these branded emails and landing pages does all of the branding on the fly. The phisher does not have to modify templates for each domain they send to. The phishing kit’s automation does all the needed changing. We wrote about these types of phishing kits here.
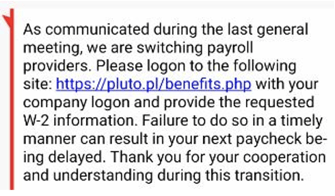
Personalized SMS Messages
It used to be that when you got an SMS spam or phishing message, it was some general ploy (see example below), not mentioning any details to show that it really is directed toward the victim.
It is becoming more and more common to see SMS-based phishing that begins with the recipient’s (first) name (see example below).
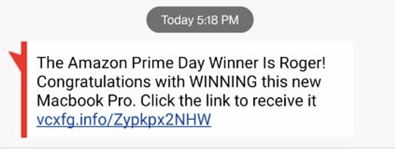
This means that the senders know the potential victim’s name and phone number. This is not surprising, as most of our phone records are out there on the dark web or Internet, along with our names. The SMS phishers are simply taking a bit more time to insert a victim’s name in the SMS-based phish in order to more easily trick them into thinking the message is real.
Ironically, the names attached to the phone record apparently are not always accurate. I got a privacy notice a few months ago that some stranger was using my phone number (which I have had for over 20 years). And now I get SMS-based phishing message to that guy’s first name about once a month (see example below). So, I am not only getting smishes to my true phone record, but to some stranger’s as well. That is a pain.
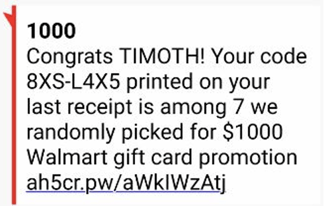
I am continually frustrated by how many robocalls and fake phishes are getting through to my cell phone on a daily basis. If you are interested, this 91-page document has the best coverage of the problem and possible defenses I have read about all in one place here.
Fake Technical Support Voice Calls
I think all of us have received calls from someone pretending to be from Microsoft proactively calling us to help us with a supposed computer virus attack on our compromised computer. I have always laughed at these attempts because I worked for Microsoft for 12 years…and I love Microsoft…but Microsoft (or Google or Apple or Facebook or Instagram, etc.) is so not going to proactively call anyone for any reason. Human-based tech support is expensive. Even with $245 to spend, you’d be lucky to find the right phone number to call to get up with the right Microsoft tech support person to get help with malware. But they definitely are not proactively calling you. It is easy for me to tell people, “Microsoft will never call you. If you get a call from Microsoft, it is a scam!”
But these days, people are getting calls from all sorts of impersonators, including fake banks, hotels companies, credit card companies, airline companies, PayPal, etc. The scammers claim they are from a company you use and that they have detected fraudulent activity. For example, “Mr. Grimes, this is your [credit card company name]. We think we have detected fraudulent activity on your account. Did you buy two American Airline tickets from Dallas, TX, to Nigeria today? No, we did not think so. Do not worry Mr. Grimes, we are here to help you. We have noticed $55,000 of other suspicious activity on your account from the last two days and we are going to reverse the charges. But first we have to make sure they are not legitimate charges. You will need to verify your account first to prove you are who we think you are. What is your login name and password?” And once you give that information, it is game over.
If you have MFA protecting your account, they will put your account into account recovery mode and get an SMS-based reset PIN code sent to your phone. The reset PIN code will be sent to you, at your phone, which they will then tell you to “verify” to them over the phone. With that, they use your reset code to reset the account and take control away from you. From there, they try to keep you on the phone and distracted and away from your account while they drain it or make fraudulent transactions. Here’s an example story.
The key is that with both SMS-based messages and voice calls, the only real authentication is potentially the caller’s phone number or voice, if you recognize it. Of course, phone numbers can be faked and even voices these days (deepfakes). It is far too easy for malicious hackers to pretend to be someone who they are not when you do not recognize the phone number or voice. Statistics show that in 40% of cell phone calls, the receiver does not have the calling phone number in their stored contacts. So, in four out of 10 calls, we usually do not recognize the number or phone number. Many of those calls are fraudulent.
My advice to end users is to be aware that SMS-based messages and voice calls are poorly authenticated and the person on the other side may not be who they say they are. If you receive an unexpected text or call, start by being suspicious. Try to get the sending party to authenticate themselves to you in a way that satisfies to you that they are who they say they are. It can be difficult.
The best mitigation to all of these attacks is education. If you make users aware of these types of more advanced social engineering attacks, the less likely they are to fall for them. Feel free to share this post with your end users as part of your routine security awareness training.
 Here's how it works:
Here's how it works:




