OK, here is something really scary.
KnowBe4's Chief Hacking Officer Kevin Mitnick now and then calls me with some chilling news. This time, Kuba Gretzky, a white hat hacker friend of Kevin developed a tool called evilginx to bypass 2-factor authentication, and it can be weaponized for any site! My first thought when I heard about this was: "Holy cr@p!"
It’s essentially a man-in-the-middle attack, but it uses proxy_pass and sub_filter to modify and capture HTTP traffic. It requires a Nginx HTTP server and some familiarity with Debian Linux. Many people have the necessary expertise to do it. I asked Kevin: "Can you show it to me?", and Kevin just sent me a video demo, you can see it below.
This particular attack is based on proxying the user through the attacker’s system with a credentials phish that uses a typo-squatting domain. Once the user falls for this social engineering tactic and enters their credentials, their authenticated session cookie gets intercepted and it's trivial to hack into the target’s account.
Gretzky has published the code for his 2FA hack on GitHub, so everyone has access to it. That means cyber criminals can easily use this for targeted phishing attacks, but security researchers can also help protect potential victims.
See it for realz here (video is just 6 minutes) and shiver:
What Kevin recommends at the end of this video: "Of course you need to have user education and training, that's a no-brainer, but you also need to conduct simulated phishing attacks so you can inoculate your users against this type of risk. And more importantly, you have to Stop, Look and Think before you click that link."
What Percentage Of Your Users Would Click On That Link?
Organizations are moving to 2FA to improve security. However, this video proves that using 2FA does not mean you are automatically protected. The Phish-prone percentage of your users remains your number one vulnerability, as employees continue to be the weakest link in your IT security, 2FA or not.
Here is a way to get your users' phish-prone percentage baseline at no cost
KnowBe4's free Phishing Security Test allows you to choose which environment you want to test:
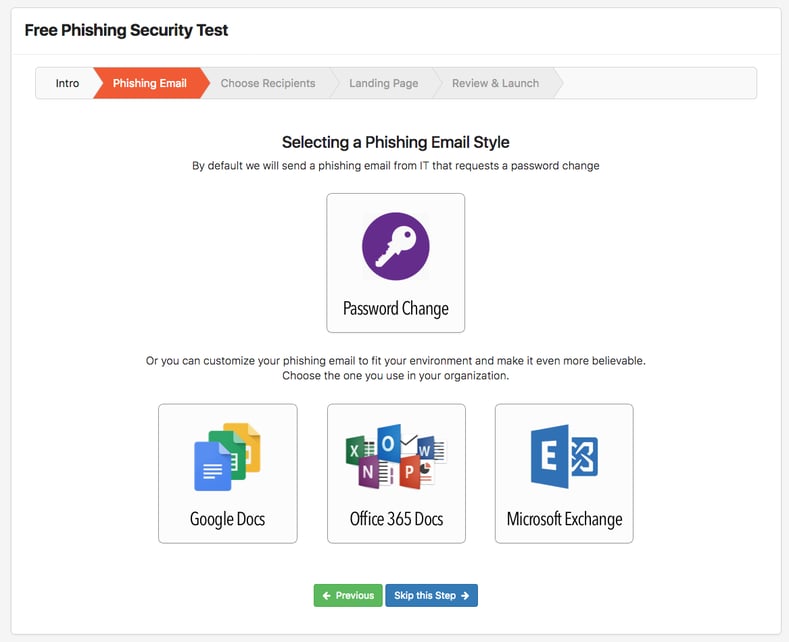
If you choose the O365 option, your user will be sent this Phishing Security Test (PST) email after you upload the email addresses and whitelist our domain:

As you just saw, cyber-attacks are changing all the time. We help you step your employees through new-school security awareness training to better manage the urgent IT security problems of social engineering, spear-phishing and ransomware attacks. Take the first step now. No need to talk to anyone.
Find out what percentage of your employees are Phish-prone™ with our free Phishing Security Test (PST). If you don't do it yourself, the bad guys will.
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





