By Eric Howes, KnowBe4's Principal Lab Researcher

Remember .PIF files? If you're like us, the extension probably rings a bell somewhere deep in the dustiest recesses of your mind -- the same place where you packed away those tips for trouble-shooting Win9x General Protection Faults and so forth.
In fact, .PIF files (Program Information Files) are config files for storing information on how to start up and run MS-DOS programs in Win9X environments. They were designed to function a lot like shortcut files, only with added config data for MS-DOS programs. You can find a good overview here.
Turns out Windows still recognizes .PIF files and will try to run them if you double-click on them. Why we would still need this functionality on, say, a Windows 7 64-bit box is not very clear, but the folks in Redmond apparently decided such functionality is still useful.
But it gets better. The more recent versions of Windows -- including Windows 7, Windows 8, and Windows 10 -- don't just know how to run .PIF files; they hide the extension, even when you explicitly configure Windows to show all extensions.
Stupid Windows Tricks
Starting to get worried? Yeah, you should be. Because it turns out that Windows will run files with the (hidden) .PIF extension even when they're not .PIF files.
So, for example, we can take a Win32 executable file, use the old double-extension trick to name a file something.pdf.pif, and Windows will hide the .PIF extension, leaving us with something that looks like a .PDF.
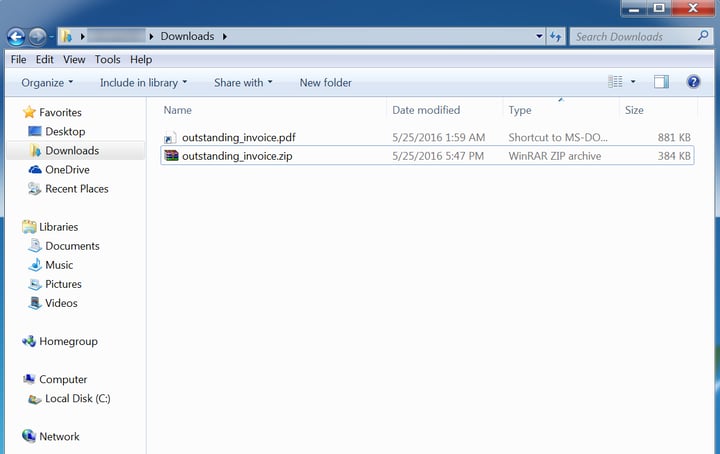
Only when you click the file to open it, your PDF reader will not open to read the file. Instead, Windows simply runs the Win32 file -- silently, without telling you a blessed thing about what just happened. No error messages, no complaints from your PDF reader about a corrupt file. Nothing.
And that's why the gods that be gave us virtual machines, so that we could be reminded of this unexpected functionality in the safety of a virtual environment instead of on one our production PCs.
A Nasty Surprise
And how did we come to be reminded of this nifty feature of Windows? This week several of our customers got hit with a highly targeted phish (addressed to specifically named employees, probably identified through LinkedIn). The phish purported to be a notice from Verizon Wireless about an overdue bill. Multiple paragraphs, the usual indifferent, stilted customer-service style prose, and a FROM: line pointing to: Collection Team Verizon Wireless [billing@collections.verizonwireless.cm]
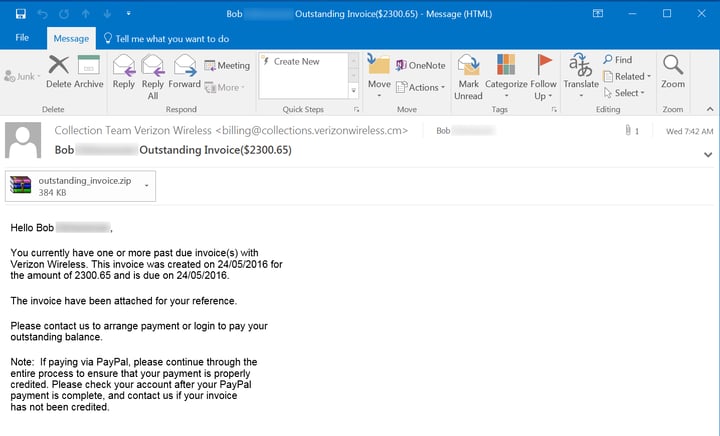
The attachment was a .ZIP file which, when unpacked, yielded a file named outstanding_invoice.pdf. But there was a hidden .PIF extension on the file. When we double-clicked it, nothing. Zilch. Nada. (Or so we thought.) It was only when we opened the file in a hex editor that we noticed it wasn't a PDF file. The header for the file was MZP (packed executable program, probably packed with UPX) along with the note: "This program must be run under Win32."
So did this thing actually run? Yup, it turns out it did. Further investigation revealed that the faux PDF file dropped a number of .EXEs and folders in:
c:\users\<user>\appdata\roaming\samo
One of the .EXEs was actively running and another had been scheduled to start automatically with Windows through one of the standard Registry autorun keys.
We ran several of the key files (including the faux PDF) through VirusTotal. Most components were identified as Zbot (aka Zeus). What Zbot would have pulled down had we allowed it to continue running we don't know, but it wouldn't have been anything friendly. For those looking for a quick refresher on Zeus/Zbot, check these several useful write-ups.
As it turns out .PIF files have been used in phishing attacks before. A post from Webroot two years ago described a similar Zeus phish using .PIF files. The difference between the attack described by Webroot and the one we just encountered is that the bad guys simply included the zipped faux .PDF as an attachment, instead of giving users a link to download it from a external site.
Old attacks never die...
...they just get recycled and re-used. Over the past six months the news has been filled with warnings about the dangerous rise of ransomware -- justifiably so, in fact, and IT admins should be treating the ransomware threat as a five alarm emergency.
That said, it's important not to lose sight of the bevy of other threats, attack vectors, and malware tricks the bad guys are known to exploit in order to compromise the PCs and networks of organizations large and small. As we were reminded this week, in the current malware landscape the past is most certainly not dead. It's not even past. The history of exploits past weighs like a nightmare on the brains of the living.
All the more reason to get your users security awareness training so they recognize phishing attacks when they see them and don't even get close to clicking potentially malicious attachments, be they real PDFs or cleverly hidden executable malware.
Once your users spot the red flags related to phishing, they can click the free Phish Alert button to delete the phish and get it forwarded including all headers to your Incident Response team.
Don't like to click on redirected buttons? Cut & Paste this link in your browser:





