 Hackers focused on CEO fraud (or Business Email Compromise - BEC) attacks often go to great lengths to hide the fact they have access to your CEO’s mailbox as part of a larger scam.
Hackers focused on CEO fraud (or Business Email Compromise - BEC) attacks often go to great lengths to hide the fact they have access to your CEO’s mailbox as part of a larger scam.
BEC is a relatively commonplace attack with impressive success. Scammers often simply purport to be the CEO of a given organization and send one of the company employees a directive to wire money, purchase gift cards, and other financially-related activities that can benefit the scammer.
But, in some cases, hackers work to compromise email credentials – which isn’t difficult, given the ease access to Office 365 via the web; a quick scam, some social engineering, a realistic logon page, and voila! - scammers have their hands on email credentials.
But hackers are taking additional steps to ensure they operate in stealth; one great example is that of using messaging rules that focus on inbound messages from users that may be warning the hacked user of a potential breach.
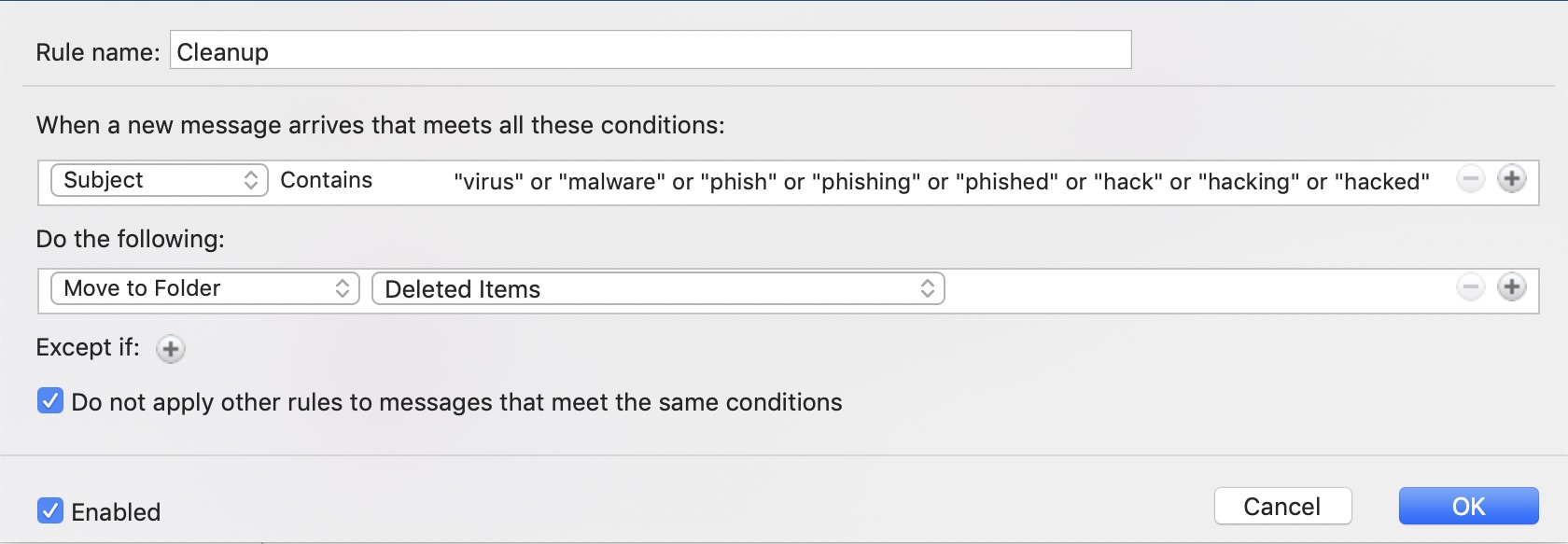
A simple rule, shown above, that looks for words of warning from colleagues, partners, and subordinates and deletes the email immediately can allow a hacker to retain their access to the CEO’s mailbox for an extended duration. This allows them time to understand where the opportunities lie; details about transactions, deals, individuals involved, etc. can all be used as part of a larger BEC scam.
Users of every level within your organization – from the CEO on down – need to be educated with continual Security Awareness Training. This training helps them to be better prepared for the initial attack that may be used to compromise credentials, infect an endpoint, or solicit personal information.
 CEO fraud has ruined the careers of many executives and loyal employees, causing over $26 billion in losses. Don’t be the next victim. This manual provides a thorough overview of how executives are compromised, how to prevent such an attack and what to do if you become a victim.
CEO fraud has ruined the careers of many executives and loyal employees, causing over $26 billion in losses. Don’t be the next victim. This manual provides a thorough overview of how executives are compromised, how to prevent such an attack and what to do if you become a victim.




