This is an up-close and personal account of how my wife Rebecca and I (we hope) dodged a cybercrime bullet.
You probably do not know that I am an elected official of the City of Clearwater, I serve on the Downtown Development Board. Part of that is a yearly disclosure about your personal finances and real estate ownership.
As a board member you are asked to fill out a so called "Form 1" which goes into quite a bit of detail about your liquidity and real estate, and if you are renting out any of it. I normally ask my personal Accountants to fill out this Form 1 and send it back. Here is a screen shot that illustrates the things it asks for:

So, imagine my wife's surprise and concern when she received an email coming from me while I was traveling, asking her to click on a PDF related to that Form 1, but with a spoofed email address! Here is how that looked:
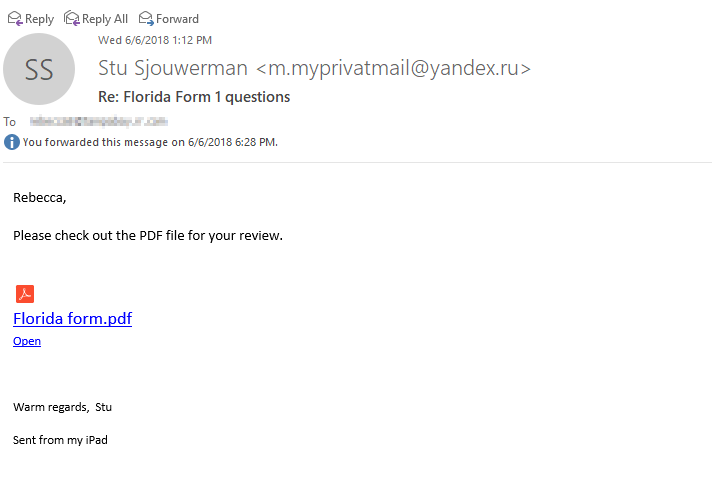
She "stepped away from the keyboard", called me immediately and asked if I had sent her this. (Rebecca has been the guinea pig for a bunch of security awareness modules the last 7 years, so she is trained against this type of social engineering within an inch of her life.) But just have a look at the phishing email and how scary "close" this type of CEO Fraud is:
- It came "from me"
- The subject was related to a current project our accountant was working on
- The subject line was a real one, from a real email thread
- Our accountant does send us PDFs frequently
- It used my real signature from my iPad, and I was on the road.
Here is how it looked in the Outlook pane... nothing here out of the ordinary:
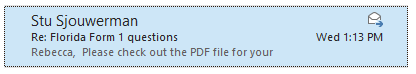
However, there was something off, I never call her by her full first name and that was the only thing that immediately raised a red flag for her.
Next thing she did was call the accountant but found that the voice mail message was not from the correct person, tried someone else there, and found that the VM was also incorrect. Hmm, voice mail system compromised too?
I sent the email to the internal KnowBe4 Incident Response team and within the hour they confirmed this was a known threat actor, that the PDF was a credentials attack, and they tracked the phish to this known threat actor: allenstore40@gmail.com. The page is a basic form page, sends an email with the form contents via php to the above email. Quickbooks and Yahoo code were also hosted on the same server. Same bad guy.
A treasure trove of data to commit a raft of crimes
When I came home and had a look at this, it was clear that the Accountant's email account had been compromised. Now, these folks have all our personal financial information including bank accounts, the amounts, copies of checks to the IRS, you name it. A real treasure trove, not to mention all other customers there too.
So, we had to dig around a bit and find our Accountant's cell phone which (had not yet been sim-swapped, scroll down to the Bank Robbery While-U-Wait story) ) so I alerted them on the account compromise. Their IT team is on it.
In the meantime, Rebecca and I divided up the banks we have accounts with and called their customer service to alert them about this compromise and freeze the accounts—which was in some cases easy, and in some cases very hard—so you can imagine who we will be banking with in the future.
I strongly recommend you physically go to your local bank branch and set up a service that requires an additional verbal approval from yourself if a transfer out of your account is being made larger than, say, 500 bucks. This may save you an incredible amount of hassle one day. If your bank does not provide that service, take out your money and move to a bank that does.
Here is a free course to keep your family safe on the internet
Now, how to train your family against this type of attack? Send them to the free KnowBe4 course that trains families to stay safe on the internet. It's brand new, called the Homecourse, and it asks for a password, which—to make it easy on everyone— is... homecourse
https://www.knowbe4.com/homecourse
Last, but not least, we checked the email address of our accountant to see if it had been breached using the free email exposure check service that we have. Lo and behold, their email address is in 6 breach databases with various information. A more recent one uploaded earlier this year.
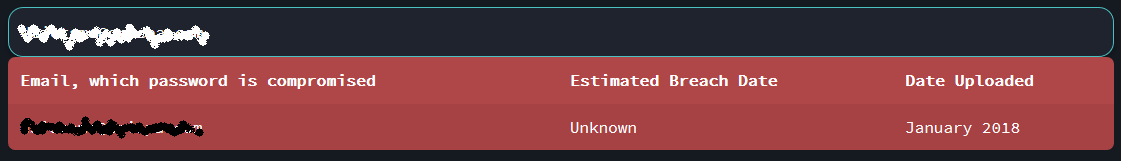
So here is another strong recommendation. Ask your organization's outside lawyers and accountants to run KnowBe4's free Email Exposure Check Pro and see if their email credentials have been breached. They get a report back that looks like this, and gives details about each breached set of credentials:
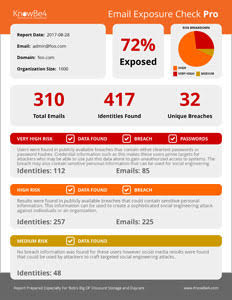
Get it here, again it's free and anyone who runs this gets results in minutes. (They are probably not going to like what they see, and ask a bunch of people to change their passwords immediately.)
https://www.knowbe4.com/email-exposure-check/
Let's stay safe out there!
Warm regards,
Stu Sjouwerman
Founder and CEO, KnowBe4, Inc.





