 Rachel Louise Ensign wrote a great story for the WSJ about CEO Fraud, also known by the FBI as Business Email Compromise. I'm quoting an extract and I strongly recommend sending a link to the original WSJ article to your C-levels as it's excellent ammo to get budget for new-school security awareness training.
Rachel Louise Ensign wrote a great story for the WSJ about CEO Fraud, also known by the FBI as Business Email Compromise. I'm quoting an extract and I strongly recommend sending a link to the original WSJ article to your C-levels as it's excellent ammo to get budget for new-school security awareness training.
"In 2018, Frank Krasovec took on a $1 million personal line of credit from PlainsCapital Bank. A few months later, he went on a business trip. When he returned, $450,000 was missing.
"Mr. Krasovec, the chairman of Dash Brands Ltd., which owns Domino’s Pizza Inc. franchises in China, said he soon learned that someone had hijacked his email and asked his assistant to wire the money to a Hong Kong account.
"Fraudsters are stealing billions of dollars each year through this type of scam, which combines sophisticated hacking with wire transfers, an old-fashioned but efficient way to move money overseas. Banks and law-enforcement officials are struggling to curb the problem, while victims like Mr. Krasovec say they are finding it nearly impossible to get their money back.
"Years ago, lenders only had to worry about real-life bank robbers. Now, the wire-transfer scam puts them in a tough position. Customers expect them to move money quickly for legitimate transactions, while also guarding against hackers that have infiltrated clients.
"The largest banks are most likely to be conduits for the wire-transfer scams, according to the American Bankers Association. But community banks, with much smaller technology budgets to build their defenses, are also vulnerable.
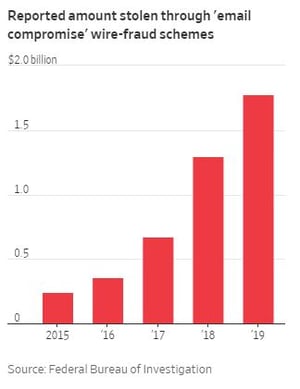
FBI: 2019 Losses up to 1.8 Billion from 1.3 Billion in 2018
"The Federal Bureau of Investigation received reports of nearly $1.8 billion in losses from this type of scam in 2019, up from about $1.3 billion the prior year. The agency estimates total losses world-wide, which include those not reported to the agency, were $26 billion between June 2016 and July 2019. The transfers primarily go to banks in Hong Kong and mainland China, where chances of recovering the money are slim, the agency said.
"Victims include “the elderly, college students, nonprofits, religious organizations, celebrities, CEOs of companies,” FBI Supervisory Special Agent Zacharia Baldwin said in an interview. “It could be anybody.”
"Hackers can break into a target’s email by trying out passwords made public in previous data breaches. They also may use phishing schemes like those used against political campaigns and in corporate espionage. The hackers then commandeer an account and impersonate the victim, asking assistants or colleagues to initiate a wire transfer."
Link to full WSJ Article: https://www.wsj.com/articles/losing-450-000-in-three-days-hackers-trick-victims-into-big-wire-transfers-11582453800?
It is a really good idea to step any employee that has any kind of access to financials through new-school security awareness training and prevent social engineering disasters like this.
 Here's how it works:
Here's how it works:




