 Organizations in Russia, Ukraine and a few hours later also the U.S. are under siege from Bad Rabbit, a new strain of ransomware which is basically a new, improved NotPetya version 2, the WSJ reported.
Organizations in Russia, Ukraine and a few hours later also the U.S. are under siege from Bad Rabbit, a new strain of ransomware which is basically a new, improved NotPetya version 2, the WSJ reported. Other sources did not include the U.S. yet, but that is just a matter of time. The outbreak started Tuesday and froze computer systems in several European countries. Department of Homeland Security’s Computer Emergency Readiness Team issued an alert saying it had received “multiple reports” of infections.
UPDATE: Ukrainian authorities attribute BadRabbit ransomware to Black Energy, the threat group they also believe was behind NotPetya. Ukraine and many (most?) security experts believe Black Energy operates in the interest and under the direction of the Russian government. (Moscow denies this, and also denies that it's carried out cyberattacks against Ukraine.) The attack has fizzled out after a short time, meaning it was shut down by the controllers.
Russia’s Interfax news agency reported on Twitter that the outbreak shut down some of its servers, forcing Interfax to rely on its Facebook account to deliver news.
Bad Rabbit Starts With Social Engineering
The outbreak appears to have started via files on hacked Russian media websites, using the popular social engineering trick of pretending to be an Adobe Flash installer. The ransomware demands a payment of 0.05 bitcoin, or about $275, from its victim, You have just 40 hours to pay.
This is NotPetya v2.0, much improved over the earlier version. Our friends at MalwareBytes blogged: "The code has many overlapping elements to the code of Petya/NotPetya, which suggests that the authors behind the attack are the same. Again, they tried to compose their malicious bundle out of stolen elements, however, the stolen Petya kernel has been substituted with a more advanced disk crypter in the form of a legitimate driver."
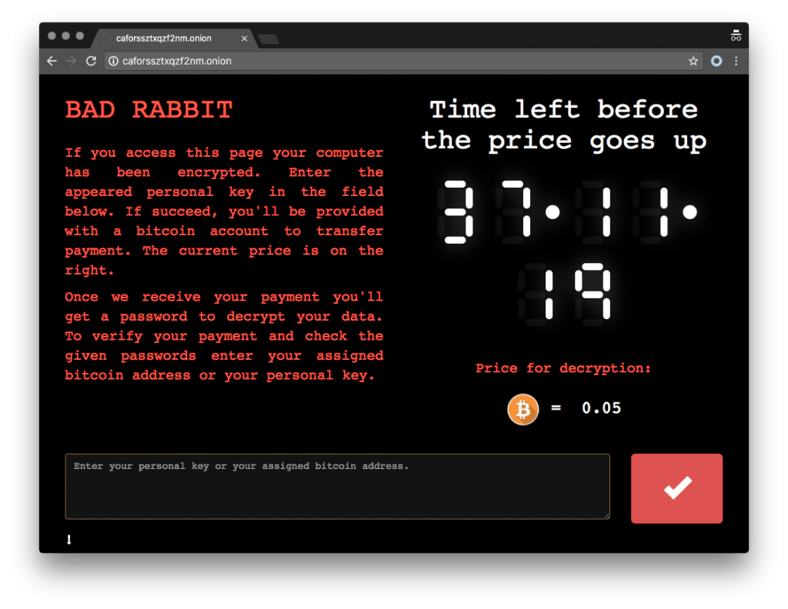
Encrypted data is recoverable after buying the key
It looks like the authors tried to improve upon previous mistakes and wrap up unfinished business. So far, it seems that in the current release, encrypted data is recoverable after buying the key, which means the BadRabbit attack is not as destructive as the previous one." They fixed a lot of bugs in the file encryption process.
Based on analysis by ESET, Emsisoft, and Fox-IT, Bad Rabbit uses Mimikatz to extract credentials from the local computer's memory, and along with a list of hard-coded credentials, it tries to access servers and workstations on the same network via SMB and WebDAV.
MimiKatz is a well known tool to extract plaintexts passwords, hash, PIN code and kerberos tickets from memory, and can also perform pass-the-hash, pass-the-ticket or build Golden tickets, link to Github. As opposed to some public claims, Bad Rabbit does not use the EternalBlue vulnerability like the NotPetya outbreak. It does scan internal network for open SMB shares though.
The hardcoded creds are hidden inside the code and include predictable usernames such as root, guest and administrator, and passwords straight out of a worst passwords list. (Note To Self: all user passwords need to be strong, step all employees through a strong password training module ASAP.)
 You need to buy two separate decryption keys
You need to buy two separate decryption keys
As for Bad Rabbit, the ransomware is a so-called disk coder, similar to Petya and NotPetya. Bad Rabbit first encrypts files on the user's computer and then replaces the MBR (Master Boot Record). This means you need to buy two keys, one for the bootloader and one for the files themselves. This basically bricks the machine. More technical background at bleepingcomputer.
How to Inoculate a machine if your endpoint software does not block Bad Rabbit
- Block execution of the files c:\windows\infpub.dat and c:\Windows\cscc.dat.
- Disable the WMI service (if it’s possible in your environment) to prevent the malware from spreading over your network.
Here are detailed instructions if you are in a hurry.
If you are a KnowBe4 customer, this is the time to run the EZXploit campaign, which emulates exactly this Bad Rabbit attack! And for both customers and If you are not a customer yet...
 How weak are your user’s passwords? Are they... P@ssw0rd?
How weak are your user’s passwords? Are they... P@ssw0rd?
Verizon's recent Data Breach Report showed that 81% of hacking-related breaches used either stolen and/or weak passwords. Employees are the weakest link in your network security, using weak passwords and falling for phishing and social engineering attacks.
KnowBe4’s complimentary Weak Password Test (WPT) checks your Active Directory for several different types of weak password related threats.
WPT gives you a quick look at the effectiveness of your password policies and any fails so that you can take action. WPT tests against 10 types of weak password related threats for example; Weak, Duplicate, Empty, Never Expires, plus 6 more.
Here's how Weak Password Test works:
- Reports on the accounts that are affected
- Tests against 10 types of weak password related threats
- Does not show/report on the actual passwords of accounts
- Just download the install and run it
- Results in a few minutes!
This will take you 5 minutes and may give you some insights you never expected!
Download this free tool now. Click here or cut & paste this link in your browser:
https://info.knowbe4.com/weak-password-test
Let's stay safe out there.
Warm regards,
Stu Sjouwerman
Founder and CEO, KnowBe4, Inc.

 How weak are your user’s passwords? Are they... P@ssw0rd?
How weak are your user’s passwords? Are they... P@ssw0rd?



