 With its wide use and trusted state among Wordpress developers and website admins, a new campaign impersonating the website security brand could put hundreds of millions of websites at risk.
With its wide use and trusted state among Wordpress developers and website admins, a new campaign impersonating the website security brand could put hundreds of millions of websites at risk.
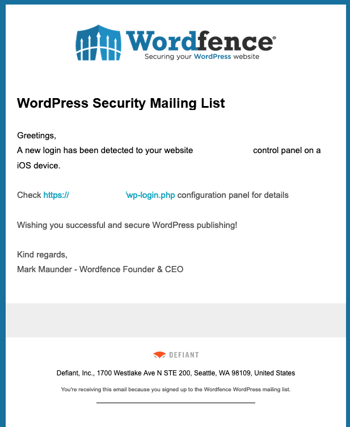
Today, it's estimated there are over 810 million websites that run on Wordpress. One of Wordpress’ most used plugins is Wordfence – a security platform made specifically for the website platform. Last month, a public service announcement about a new phishing campaign impersonating Wordfence was released, providing details on the scam.
In essence, an email is received by the potential victim that impersonates Wordfence – keep in mind that those behind this scam have a rather large base of email addresses to work with. Smaller organizations with outsourced web development could easily receive emails already from Wordfence at this email address. The phishing email itself looks rather legitimate, simply stating “a new logon has been detected” (something Wordfence actually sends emails about).
The link, of course, doesn’t take you to your website, but to a malicious domain. What’s scary is that one evolution of this scam could include hitting your own domain /wp-admin page, and then impersonating it as a means to gain administrative access to a victim organization’s website – a new form, if you will, of Initial Access Broker where website access is provided, rather than credentialed access to a network, etc.
There are two things you should do to mitigate this kind of attack. First, implement multi-factor authentication on your Wordpress site – that way, even if a credential is compromised, it’s useless without the additional authentication factor. Second, users that may receive such emails should undergo security awareness training so they understand they need to maintain their vigilance and make certain it’s legitimate before engaging with its content.
 New-school Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't a one and done deal, continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!
New-school Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't a one and done deal, continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!




