During 2016, ransomware exploded. It clearly became the biggest menace on the net, using phishing as it's No.1 infection vector.
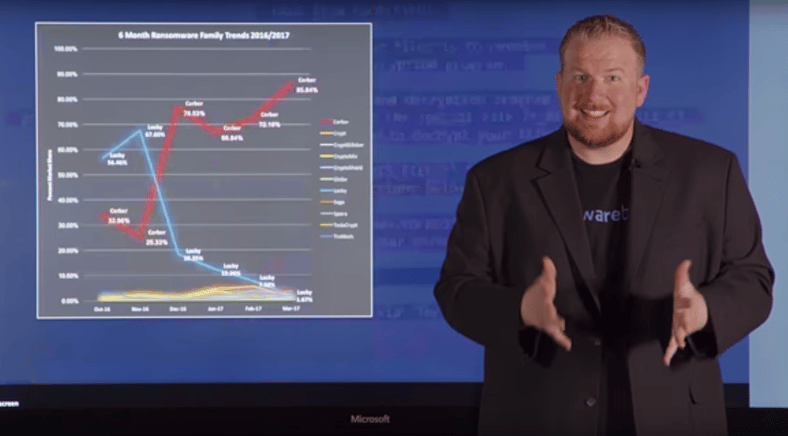
Hundreds of ransomware strains competed for market dominance last year, but one was clearly dominant; Locky, costing victims over 1 billion dollars. However, a recent report of our friends at Malwarebytes showed that Locky has fallen off the face of the earth in Q1 2017, making way for the Cerber strain to become the new king of ransomware.
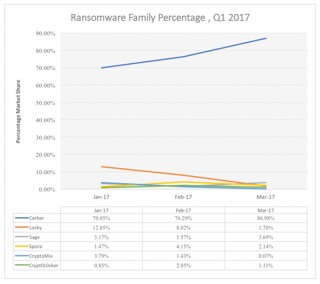
Malwarebyte's new Cybercrime Tactics and Techniques Q1 2017 report shows Cerber has totally taken over "the market", accounting for 90 percent of Windows ransomware. Note that ransomware accounts for 60 percent of all malware attacks on Windows.
So why has Cerber become the Apex Predator?
The success of Cerber is down to its features (robust encryption, offline encryption etc) combined with the adoption of a RAAS (Ransomware-as-a-Service) business model, where the malicious code can be modified or leased through an affiliate scheme. "It's also very easy for non-technical criminals to get their hands on a customized version of the ransomware," Malwarebytes reports.
 Another factor contributing to the rise of Cerber is that those behind it are constantly upgrading it with new features and evasion techniques. Researchers at Trend Micro recently detailed how Cerber has gained the ability to evade detection by cybersecurity tools which use machine learning to identify threats.
Another factor contributing to the rise of Cerber is that those behind it are constantly upgrading it with new features and evasion techniques. Researchers at Trend Micro recently detailed how Cerber has gained the ability to evade detection by cybersecurity tools which use machine learning to identify threats.
The Cerber strain, like most ransomware, is mostly delivered by a phishing email. But rather than encouraging the victim to click on a link to download a file, these emails contain a link to Dropbox which downloads and self-extracts the Cerber payload which is a social engineering tactic which is hard to protect against.
The Locky strain which was last year's number one, has dropped off the map due to a switch in tactics by the cyber gang behind the Necurs spam botnet. The Necurs network used to distribute Locky, but suddenly surged back to life last month to distribute fake stock tips for 'pump and dump' scams.
Cerber is more difficult to stop than Locky
"We've already observed evolution in its distribution mechanisms and it's likely they will continue to do this to ensure that their malware can infect users effectively. It might also start instituting additional functionality like different files to target and increasing victim support capabilities," Adam Kujawa, lead malware intelligence analyst at Malwarebytes, said.
"However it's hard to predict the exact modifications Cerber will make, the only definite is that it's not going away," he added.
They ended off with: "We expect to see continued heavy distribution of Cerber through Q2 2017 due to new developments made to the malware design and its continued use of the ransomware as a service (RaaS) model."
At the moment, Cerber may be king of the hill, but if you look at the tumultuous history of ransomware, this won't last for too long. Either the Cerber mafia will withdraw on their own when the heat gets too much, or they will pivot to a new business model just like the Locky/Necurs gang just did. Third option: they'll get arrested like BitCryptor/CoinVault.
In any case, there will be another ransomware strain waiting in the wings to grab the No.1 slot, and at the moment it looks like Spora is the contender for the crown.
Since phishing has risen to the #1 malware infection vector, and attacks are getting through your filters too often, getting your users effective security awareness training which includes frequent simulated phishing attacks is a must.
KnowBe4's integrated training and phishing platform allows you to send attachments with Word Docs with macros in them, so you can see which users open the attachments and then enable macros!
See it for yourself and get a live, one-on-one demo.

PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://info.knowbe4.com/kmsat-request-a-demo