
Zeljika at HelpnetSecurity had a great summary of Wombat's latest State of the Phish report: "Training employees to spot phishing emails, messages and phone calls can’t be done just once or once a year if the organization wants to see click rates decrease.
For one thing, employees come and go (and change roles) with regularity. Secondly, threats change over time. Thirdly, knowledge and practices that aren’t regularly reinforced will be lost. And, finally, awareness isn’t the same as knowledge.
“Just knowing a threat exists isn’t the same as knowing how to recognize and respond to a threat when it presents itself. In-depth education about phishing prevention is needed to create lasting behavior change,” Wombat Security researchers point out.
The statistics included in the company’s latest annual State of the Phish report show the difference made by both the tools used to train end users to recognize and avoid phishing attacks and how often they are used.
In the US, most organizations use computer-based online security awareness training and simulated phishing attacks to train employees, while UK organizations generally opt for more passive training methods over hands-on practice:
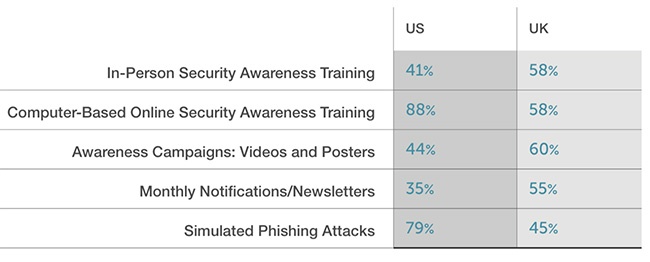
Also, 46 percent of US organizations use those tools biweekly or monthly, while UK organizations do that in just 21 percent of cases.
As a result, 61 percent of US organizations see quantifiable results from these efforts, compared to 28 percent of UK orgs.
You also might find yourself tempted by a “set it and forget it” security awareness training program, the researchers noted, but that’s not ideal. “When you plan and schedule your phishing tests months (or even years) in advance, you lose the ability to be responsive to emerging threats and to tailor activities based on your results.”
Other interesting findings
The company based the report on data from tens of millions of simulated phishing attacks, and they found that:
- Personalized phishing tests (personalized email address, first name or last name) are no more effective than non-personalized ones.
- End users are most likely to report suspicious emails in the middle of the week.
- The topics and themes that are most tempting to end users are “online shopping security updates,” “corporate voicemail from an unknown caller,” and “corporate email improvements.”
- Two simulated phishing templates had a near 100% click rate: one that masqueraded as a database password reset alert, and another that claimed to include an updated building evacuation plan.
- Organizations in the telecommunications, retail, consumer goods, government, and hospitality industries have, on average, the worst click rate (15% to 13%), while those in the energy, finance, transportation and defense industrial base industries have the best (8% to 3%).
- Average click rates fell across all four categories (corporate, commercial, cloud and consumer emails) this year in comparison to 2016. The researchers particularly saw a significant improvement in click rates on cloud-based templates (business-related emails include messages about downloading documents from cloud storage services, or going to an online sharing service to create or edit a document).
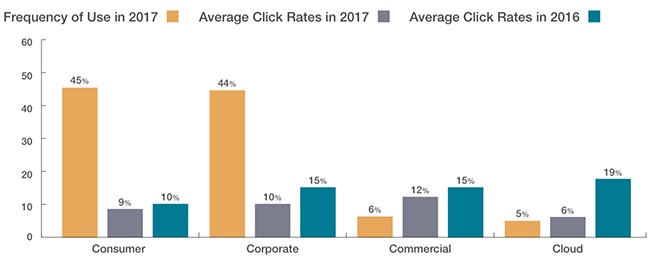
Surveys of infosec professionals and end users also revealed that:
- On average, 53% of infosec professionals reported experiencing spear phishing in 2017.
- 95% of organizations train end users on how to identify and avoid phishing attacks.
- 45% of organizations said there are ramifications if their users continue to click on simulated phishing attacks. Consequences include counseling from a manager or IT department, additional training, and removal of access to systems, but also termination (11% of orgs) and a monetary penalty (5% of orgs).
- Most end users know what phishing is, but only 16% of them know what smishing is. “As more and more employees use smartphones to connect to corporate systems and data, the potential ramifications of an uneducated workforce should not be ignored,” the researchers pointed out.
Source: https://www.helpnetsecurity.com/2018/02/23/phishing-messages/
Free Phishing Security Test
Did you know that 91% of successful data breaches started with a spear-phishing attack?
Cyber-attacks are rapidly getting more sophisticated. We help you train your employees to better manage the urgent IT security problems of social engineering, spear-phishing and ransomware attacks. Take the first step now. Find out what percentage of your employees are Phish-prone™ with our new, improved free test.

PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:




