 There is a new strain of ransomware called Cerber that takes creepiness to the next level.
There is a new strain of ransomware called Cerber that takes creepiness to the next level.
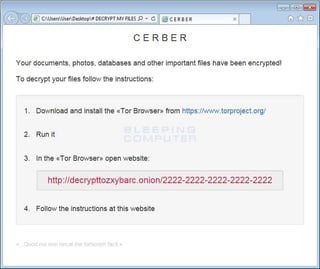
It drops three files on the victim's desktop named "# DECRYPT MY FILES #." These files contain instructions about the ransom amount and how to pay it. One of the files is your standard TXT format, one is HTML and the third is plain weird. It contains a Visual Basic Script, which contains text-to-speech code that converts text into an audio message.
"When the above script is executed, your computer will speak a message stating that your computer's files were encrypted and will repeat itself numerous times," Larry Abrams from Bleepingcomputer said in a blog post. They have a sample in that post you can listen to.
Cerber's criminal developers are selling the tool as Ransomware-as-a-Service (RaaS) so that practically anyone can use it without any coding experience. It is easy to find out where this new strain originated. When first run, Cerber will check to see if the victim is from a particular country. If the computer appears to be from any of the following countries, it will terminate itself and not encrypt the computer: Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, Tajikistan, Ukraine, Uzbekistan.
Yup, that was easy. Another Eastern European cyber gang with another strain. This is getting old, and employees are still the weakest link in your IT security.
There are two different attack vectors being used: the first is a double-zipped file with a malicious WSF (Windows Script File) attached to a phishing email, the second is an unsubscribe link located at the bottom of the email, which also links to the same ZIP file. This new strain was also pushed by the Rig and Magnitude exploit kits which both use zero-day vulnerabilities.
Cerber then decrypts several different file extensions and also scan and enumerates unmapped Windows shares to encrypt files found there.
The ransom note directs its victims to the payment site which asks you to select your language and enter a captcha. There you will get your ransom amount (at this time 1.24 bitcoins or around $500), instructions to pay and you will also be warned that ransom doubles if unpaid within the first 7 days. Unfortunately no known free decryption method is available.
Get the most informative and complete ransomware hostage rescue manual. This 20-page manual (PDF) is packed with actionable info that you need to prevent infections, and what to do when you are hit with ransomware.




