 By Laura DiDio, Principal at ITIC, a research and consulting firm based in the Boston area.
By Laura DiDio, Principal at ITIC, a research and consulting firm based in the Boston area.
“We have met the enemy and it is us.”
This quote aptly describes the current state of security and cyber security.
End users now arguably pose a bigger immediate and ongoing threat to the cyber security of consumer and corporate devices, applications and networks.
Those are the findings of ITIC’s latest 2017 Security Survey which found that 80% of 650 corporate respondents said that end user carelessness and failure to implement and install security on their BYOD and mobile devices are more dangerous than targeted hacks and rogue code.
That said, the organizations which ranged from SMBs with 25 users to large enterprises with over 10,000 employees, are painfully aware of the threat posed by Ransomware, Bots, Phishing scams, Trojans, Viruses, other types of malware and even targeted corporate espionage, are all capable and culpable of wreaking havoc.
End users and IT administrators, each own 50% of the responsibility
Cyber security and protecting corporate and consumer assets and will always be, a 50-50 proposition. End users and IT administrators, own 50% of the responsibility to secure their devices and adhere to safe computing practices. For starters, this means getting security training and actually installing and utilizing security mechanisms. Too often, corporate employees and consumers disable security safeguards because of usability issues.
Similarly, security vendors bear 50% of the responsibility to incorporate strong security mechanisms into their products. The onus is also on vendors to provide businesses and consumers with regular updates. Transparency is also a must for the entire vendor community; they must respond quickly, acknowledge security flaws when they occur and quickly move to deliver guidance and release fixes when bugs or glitches are discovered.
Increasing Interconnectivity and IoT Make Security Imperative
It’s absolutely imperative for corporations, consumers and vendors to be proactive in their approach to security in the 21st Century Digital Age. The corporate infrastructure (servers, routers, gateways and firewalls); BYOD devices and applications are increasingly interconnected via the Internet of Things (IoT). The line of demarcation between personal data and corporate assets is blurring to the point of indistinction as employees increasingly use their own devices for personal and business purposes.
A chain is only as strong as its weakest link. With so much data from myriad sources traversing private and public networks on a daily basis, even the strongest system and network security is easily undone or bypassed completely by a careless corporate or consumer user. Nonetheless, many people continue to blithely ignore the seriousness of the issue.
Companies of every size across every vertical are at risk.
SMBs, which account for nearly 60% of all companies businesses, mistakenly believe they’re not big enough to be targeted. In fact, over 70% cyber attacks occur at businesses with less than 100 employees, according to a 2015 Report, “Small Business, Big Threat: Protecting Small Businesses from Cyber Attacks,” by the Small Business Committee.
IoT Bots Emerge as Latest Cyber Security Threat
In IoT, the attack surface is potentially limitless. There is no singular mechanism to secure the millions or billions of inter-connected components and endpoints. IoT is a veritable hackers’ playground. Consider that connected devices are equipped with default user IDs and passwords that are child’s play for a hacker to crack.
Yet many users and companies never change simplistic original passwords like “Admin,” “123456,” and “Password.” Additionally, many IoT vendors and third party service providers use default passwords that are an abbreviated version of the company brand name. Hackers are well aware and waste no opportunity to exploit these weaknesses.
Cyber Security: An Inconvenient Truth with Expensive and Deadly Consequences
Security breaches almost invariably disrupt operations, resulting in downtime and lost productivity. ITIC’s latest 2017 Hourly Cost of Downtime survey indicates that 98% of large enterprises with more than 1000 employees say that on average, a single hour of downtime per year costs their company over $100,000; while 81% report that the cost exceeds $300,000. The cost of downtime is also expensive for SMBs with one to 50 employees: respondents in this group noted that the Median average cost of one hour of downtime is $58,000.
These statistics represent the “average” hourly cost of downtime. In a worst case scenario – like a catastrophic outage that occurs during peak usage times or that disrupts a crucial business transaction – the monetary losses to the organization can reach hundreds of thousands or millions per minute.
Companies must also factor in the potential losses related to litigation as well as civil penalties stemming from organizations’ failure to meet Service Level Agreements (SLAs) or Compliance Regulations as well as potential “good will” gestures made to the organization’s customers and business partners that were negatively impacted by a system or network failure. These two conditions can cause downtime costs to skyrocket even further.
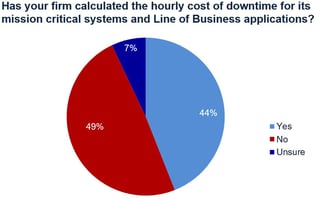
Despite highly publicized security incidents, ITIC’s 2017 Hourly Cost of Downtime Survey found that corporations, their C-level executives, IT Managers and end users are the biggest culprits in unplanned downtime due to security issues. Some 65% of businesses do not calculate the cost or business impact of security-related downtime and over 40% of firms are unable to detect or defend against a security breach in a timely manner when one does occur.
Laura DiDio is Principal at ITIC, a research and consulting firm based in the Boston area.





