According to a report from email security & protection vendor Agari, the cybercriminal group dubbed London Blue are directing their latest scams at very specific finance execs.
The business email compromise (BEC) scam has seen many iterations – each one seeking to fool the recipient into taking actions that benefit the cybercriminal. Agari uncovered this scam by being a potential victim themselves – their CFO was sent an email purporting to be from Agari’s CEO asking for a wire transfer. Unfortunately for the bad guys, they picked the wrong company to target.
Agari’s counterintelligence research team jumped into action and was able to learn much about the scammers and their intended targets.
The Scammers
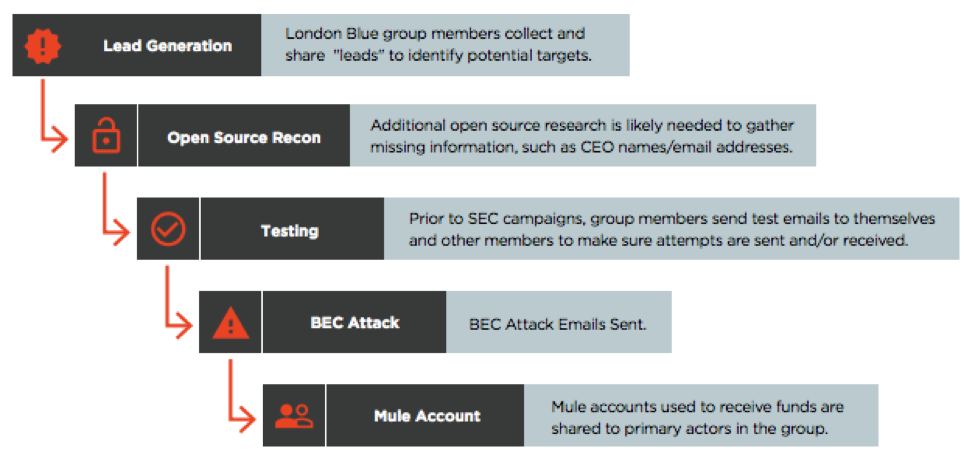
The group dubbed ‘London Blue’ by Agari run like a well-tuned corporation. Members of the group are responsible for specific tasks that, in total, make up the scam. According to Agari, this includes:
- Business intelligence (lead generation)
- Sales management (assignment of leads)
- Email marketing (semi-customized BEC attack emails)
- Sales (the con itself, conducted with individual attention to the victim)
- Financial operations (receiving, moving, and extracting the funds)
- Human resources (recruiting and managing money mules)
Source: Agari
The Targets
London Blue built a list of more than 50,000 finance executives that was generated over a five-month period in early 2018. The top titles targeted included: CFO (71%), Finance Director/Manager (12%), and Controller (9%), and went down the org chart to Executive Assistant. The majority of companies targeted – over half – reside in the United States, with countries in Europe, Central America, and Africa also represented.
Protecting Against London Blue
Organizations should be very afraid of London Blue – with over 50,000 organizations targeted, and London Blue’s fine-tuned scam execution, they are a force to be reckoned with. And because their emails use social engineering to trick their victims, there is no malware or attachments to use to spot the scam.
To address this scam and threats like it, we recommend organizations take two steps:
- Verify with a Phone Call – it’s something we’ve shared before. Users involved with financial transactions need to have policy and/or procedure dictate that any requests for money transfers of any kind be validated with a phone call to the originating user.
- Educate Users – Users, regardless of their role within the organization, need to be educated on scams like this in order to elevate their understanding for the need to be vigilant against external threats. Security Awareness Training educates users on the latest trends in phishing scams, malware, social engineering, and more in an effort to establish a security culture, reducing your organization’s risk of successful cyberattack.
You can read the full report on London Blue over Agari’s website.






