 We saw yesterday how phishing affects the financial sector. Here we see another, related trend: impersonation attacks that purport to be from the victim’s bank.
We saw yesterday how phishing affects the financial sector. Here we see another, related trend: impersonation attacks that purport to be from the victim’s bank.
Bank vishing scams are growing more convincing and harder to detect, CNN reports. A San Francisco man named Peter Gunst told CNN how he had nearly fallen for “the most credible phishing attempt I’ve experienced to date.”
Gunst said he received two phone calls from the same number, and he answered the phone the second time. A woman on the other end told him she worked for his bank and asked if he had just tried to use his card in Miami. Gunst said no, and the woman began to walk him through the process of securing his account.
She asked Gunst for his member number and he gave it to her. He then received a text message from the bank’s phone number containing a PIN, which he read out to the woman. This was actually a password reset code, and it granted her access to his bank account.
Next, the woman told Gunst they needed to block his PIN, and asked what his PIN was. At this point Gunst realized it was a scam, since no real bank should ask you for your PIN, and he hung up immediately. In hindsight, Gunst believes he should have been more suspicious of the caller from the outset.
“When I read that thread now, that’s one red flag after another,” Gunst told CNN. “But it's hard to express the social engineering component of it. My guard wasn't up in the way it should've been.”
Gunst added that he had dealt with real fraud prevention calls from his bank in the past, and the scammer knew exactly how this process worked. He also thinks the scammer somehow knew he was a customer of that particular bank.
“It’s unclear at this point where this happened, but there's no doubt in my mind that they knew that I was a customer of that bank and they thoroughly understood the security procedures of that bank,” Gunst said. “It was rather targeted.”
CNN points out that sometimes scammers gain an advantage by targeting employees of a company to gather information on customers before targeting those customers with scams. New-school security awareness training can enable your employees to be constantly on guard for suspicious requests.
CNN has the story: https://www.cnn.com/2019/10/27/business/phishing-bank-scam-trnd/index.html
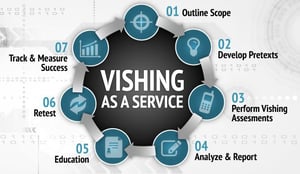
 Here's how MASA works:
Here's how MASA works:




