 As ransomware, business email compromise, and phishing attacks continue to escalate, new data sheds light on where organizations need to focus to help put a stop to attack success.
As ransomware, business email compromise, and phishing attacks continue to escalate, new data sheds light on where organizations need to focus to help put a stop to attack success.
We’ve long known that credentials are the key to a successful cyberattack. They enable initial access to endpoints, lateral movement, entrance to applications, and access to data. New data from security vendor Talos’ Quarterly Report: Incident Response Trends in Q3 2022 shows repeatedly that credentials are a material focus for threat actors from a few perspectives.
Perspective 1: Initial Attack Vector
We all know that the need for credentials are an eventual certainty, but Talos identified the use of Valid Accounts as the top infection vector in Q3, citing cases where “accounts were misconfigured, not disabled properly, or had weak passwords.”
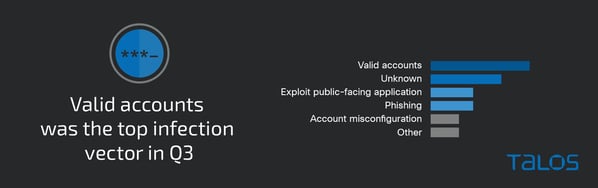
Source: Talos
Perspective 2: Tools Used
Threat actors have a wide range of native, malicious, and misused legitimate tools at their disposal that aid in every aspect of a cyberattack. What’s interesting is that, according to the Talos data, over two-thirds of tools seen being used during attacks focused on accessing and collecting credentials.
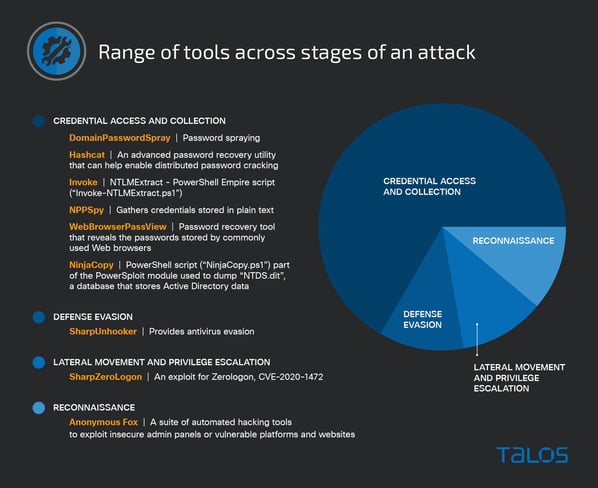
Source: Talos
Perspective 3: Top Observed MITRE ATT&CK Techniques
I’m a big fan of the ATT&CK framework, as it provides security professionals with a way to better understand the threat actions being taken in order to create a more effective defense. According to the Talos data, the MITRE technique T1078 Valid Accounts was the most observed threat action during attacks.
The Talos data provides objective evidence that credentials are a focus for attacks today. What’s necessary is to stop the misuse of credentials at the initial attack by ensuring strong passwords are used, and that users don’t fall victim to credential harvesting scams – something taught via Security Awareness Training. If we can stop making it so easy for threat actors to misuse valid credentials, the end result will be far less successful cyber attacks.
 Here's how it works:
Here's how it works:




