 New data shows phishing attacks are deviating from the traditional focus on technology and retail sectors and are opting for alternate brands with widespread appeal.
New data shows phishing attacks are deviating from the traditional focus on technology and retail sectors and are opting for alternate brands with widespread appeal.
I’ve covered plenty of reports about brand impersonation and it’s almost always Microsoft on top of the list.
And with good reason: access to a Microsoft 365 account can give attackers a foothold and potential access to data, applications and more.
But in Guardio’s latest Q1 Phishing Impersonation report, things take a surprising turn. According to their data, the U.S. Postal service saw a massive jump of nearly 6x from its position two quarter’s ago, representing just 1.9% of all impersonation attacks to Q1’s position of 11.6%.
Guardio cites the use of text messages as a common medium for scams involving the USPS. This could be one of the reasons for the jump; the ease of access to basically every mobile phone number in the U.S. outweighs the work it would take to obtain the equivalent number of email addresses.
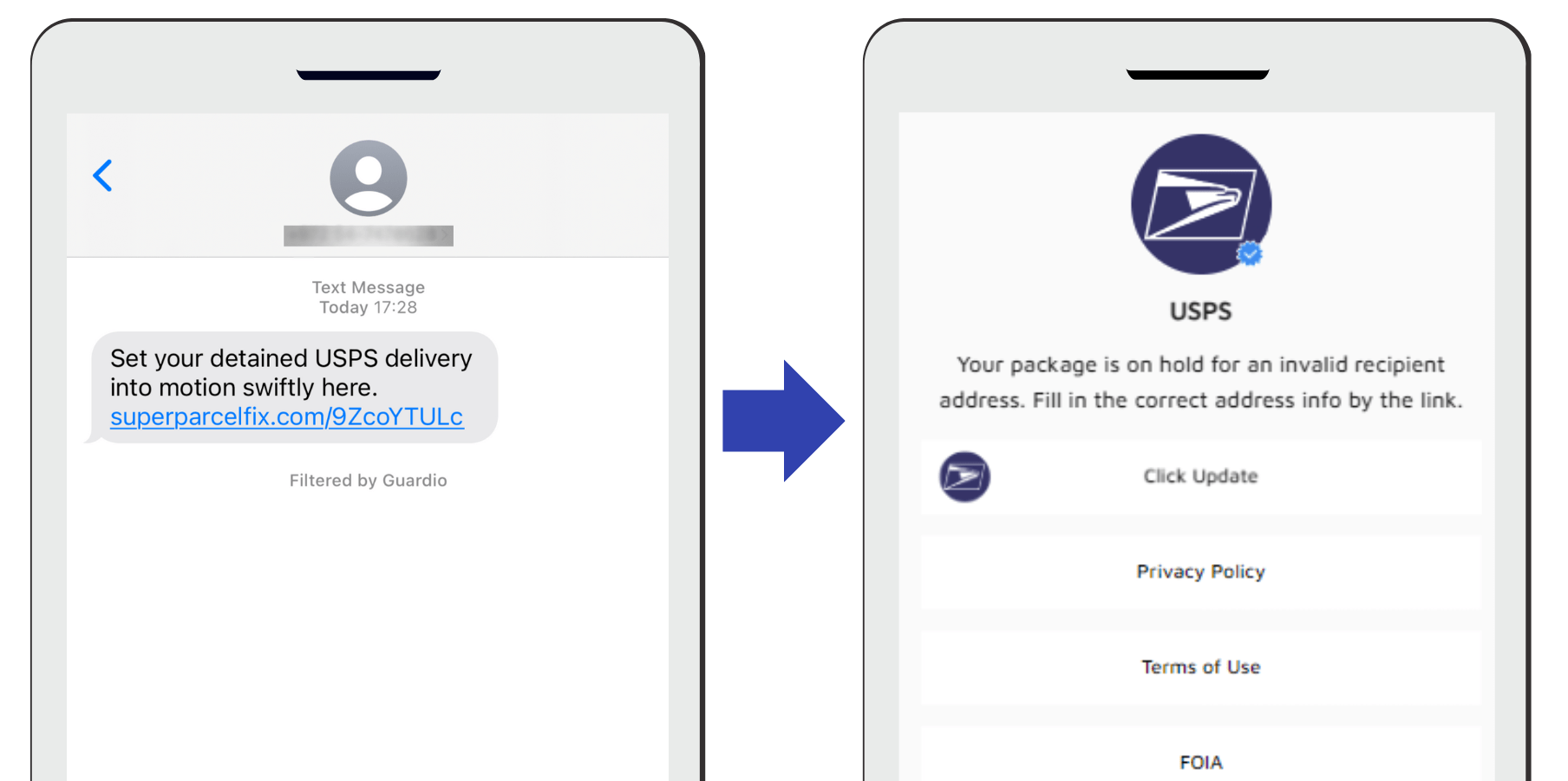
Source: Ctfassets
Microsoft’s brand was still represented in 9.3% of all impersonated emails, putting it in second place, with the focus remaining on obtaining user credentials with fake logins:
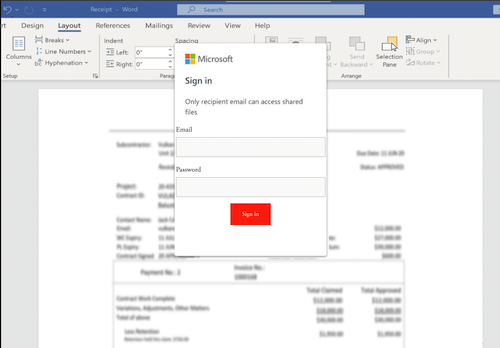
Source: Ctfassets
You should expect the brands to continue to change positions in the lists of those security vendors tracking the brands they see in attacks; it’s merely a shifting of priorities and desired outcomes – all in the name of figuring out the best path to monetize victims.
No matter the brand, the simple rule of thumb, “If it’s not expected, it should be treated as suspicious” applies here – something employees who undergo security awareness training understand fully. Anyone receiving branded communications across an unexpected medium or with a request that is out of the norm, should treat them as hostile and scrutinize such messages with extreme prejudice until it’s proven to be legitimate.
KnowBe4 empowers your workforce to make smarter security decisions every day. Over 65,000 organizations worldwide trust the KnowBe4 platform to strengthen their security culture and reduce human risk.
 Here's how it works:
Here's how it works:




