 A new SMS-based phishing attack uses a smishing kit-as-a-service to impersonate the U.S. Postal Service.
A new SMS-based phishing attack uses a smishing kit-as-a-service to impersonate the U.S. Postal Service.
If you’ve received a fake text from the U.S. Postal Service in the last month, you’re not alone. A Cybercrime-as-a-Service (CaaS) group based in China is likely behind the attack, and many others.
According to security researchers at cybersecurity vendor Resecurity, the group is behind similar attacks throughout the globe, posing as the U.K. Royal Mail, New Zealand Postal Service (NZPOST), Correos (Spain), PostNord, Poste Italiane and the Italian Revenue Service (Italy). They’ve also been responsible for scams previously targeting FedEx and UPS customers.
In these attacks, victims are sent a text about a failed delivery:
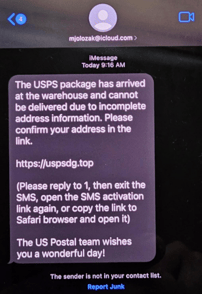
Source: Resecurity
Upon clicking the presented link, victims are taken to a website impersonating the USPS where the Redelivery option requires a small payment to obtain the victim’s credit card details.
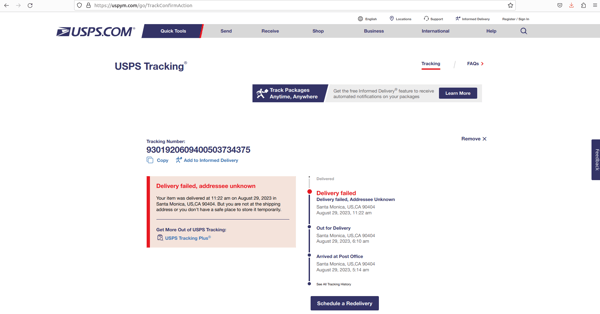
Source: Resecurity
The standout telltale sign that this is a scam is the domain name – Smishing Triad have registered a large number of “.top” domains that begin with “usp” to align the domain with the USPS.
But this may not be so easy to spot when using a mobile device. Many browsers show the friendly name and not the domain name, making the attack appear more legitimate. All the more reason to educate your users with new-school security awareness training about these types of attacks.
 Here's how it works:
Here's how it works:




