With 98% of all web traffic going over HTTPS, the malicious use of TLS (transport layer security) helps the cybercriminal conceal their activity specifics while also potentially doing so unnoticed.
Every security strategy has one goal – either keep the bad guys out or expose them as soon as possible. Pretty simple stuff – except that the cybercriminals are really good at working in stealth. One of the tactics is the use of TLS to encrypt web traffic to command and control (C2) servers over TCP port 443 (a port your firewall most definitely has open).
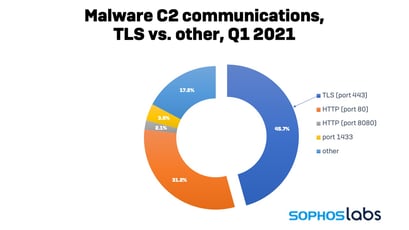
According to new data from security vendor Sophos, 46% of all malware-related communication over the Internet is encrypted using TLS.
 Source: Sophos
Source: Sophos
Sophos also notes that a large portion of TLS communications use an Internet Protocol port other than the standard 443, 80, 8080, and found many uses of non-standard port numbers when communicating securely. Half (49%) of the certificates used were issued by a Certificate Authority, with the remainder using self-signed certificates.
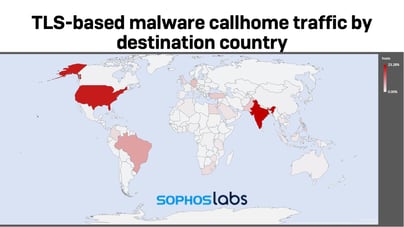
Nearly one-quarter (23%) of TLS traffic communicates with hosts within the United States, with another 23% in India.
 Source: Sophos
Source: Sophos
Remember, TLS is about privacy, not security. It allows the bad guy to hide C2 commands, delivery of malware or tools, exfiltration of data, and more. To stop malicious use, organizations can employ DNS filtering solutions, use an ExternalDynamicList of malicious IP addresses on your firewall, as well as look to Security Awareness Training to stop this kind of traffic before it ever exists by teaching users to not engage with phishing emails and malicious web content that act as the catalyst for attacks.




