 As if the virus itself wasn’t bad enough, lowlife scammers are using the pandemic to trick healthcare workers into giving up credentials.
As if the virus itself wasn’t bad enough, lowlife scammers are using the pandemic to trick healthcare workers into giving up credentials.
Elite hackers tried to break into the World Health Organization earlier this month, sources told Reuters, part of what a senior agency official said was a more than two-fold increase in cyberattacks.
Also, earlier this month, an email went out a number of U.K. healthcare organizations pretending to be from their respective internal IT departments under the premise of requiring staff to take part in both a survey and seminar on the virus.
Given the recent events, it makes sense that this kind of training may be required for all staff members – and at least one cybercriminal gang was counting on it. According to a recent report, the phishing email first found by researchers at Mimecast contains a link that takes the victim to a lookalike Outlook Web App logon page.
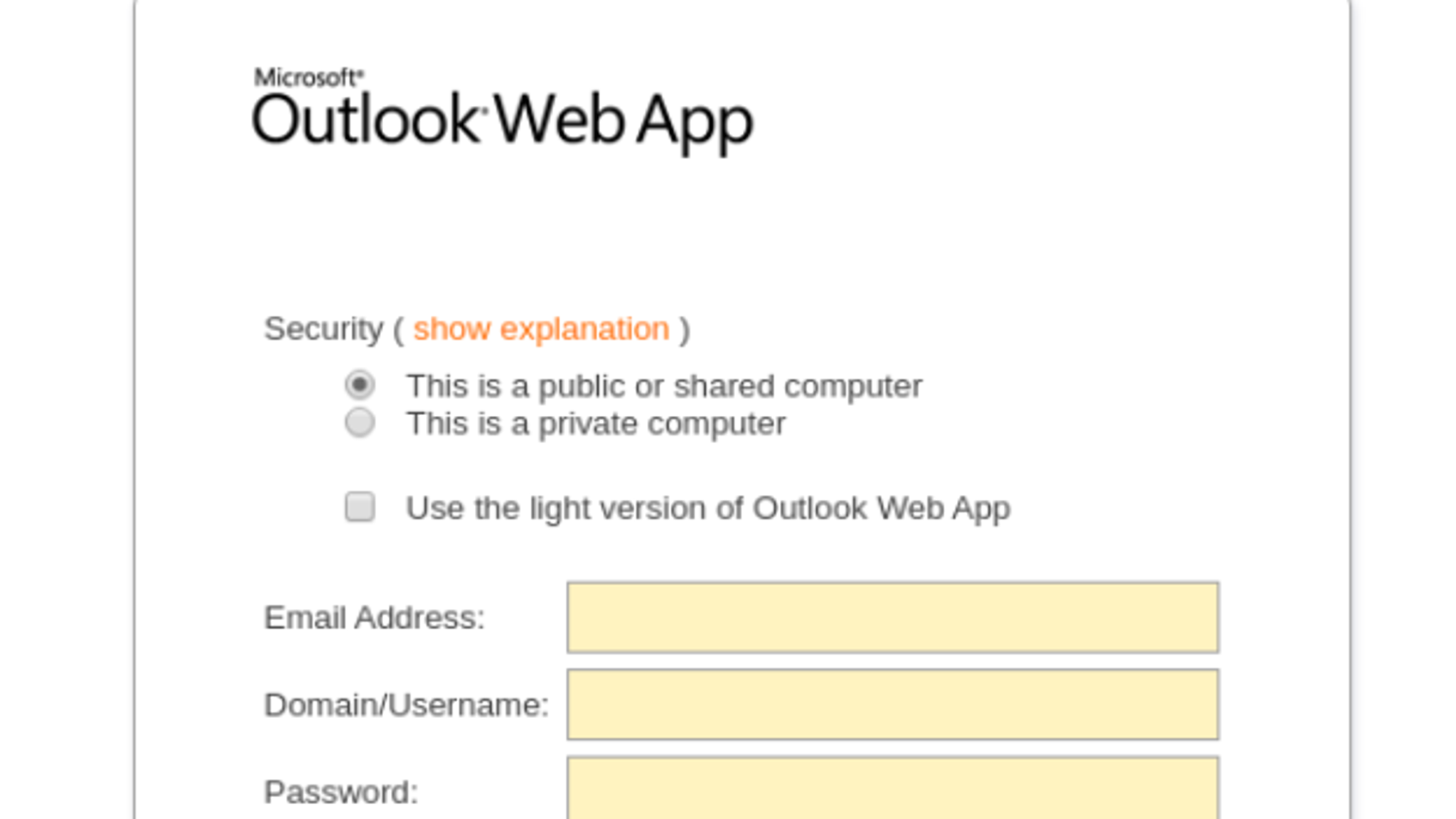
By filling in the details, victims have not only given up their web-based credentials, but also (notice the presence of domain) their on-premises credentials.
Here at KnowBe4, we’ve noticed a massive uptick in coronavirus-themed attacks; the sensitivity and urgency around addressing the virus makes for a perfect message to get potential victims – both individuals and corporate users – to act.
Organizations need to put their staff on high alert about emails regarding coronavirus / COVID-19; the possibilities are endless of how this current pandemic could be used in the favor of the cybercriminal.
Today it’s the Coronavirus, next month it will be about a new government program to give you free money, and in a few months, it will be the Japan Olympics. Given that while the theming constantly changes, the use of phishing remains high, organizations should look to Security Awareness Training to educate users on how to maintain a state of suspicion and spot a scam regardless of the message it uses.
 Here's how it works:
Here's how it works:




