The latest Analysis Report covers both areas of concern around Office 365 configurations that impact security, and offers up some simple recommendations to shore up vulnerabilities.
The DHS’ Cybersecurity and Infrastructure Security Agency (CISA) regularly puts out in-depth reports on new or evolving cyber threats. The latest report focuses on Office 365 and some of the key issues CISA sees with common customer configurations.
According to the report, a number of configuration issues exist that have “led to user and mailbox compromises and vulnerabilities.” These include:
- No MFA for Admin Accounts – Disabled by default, utilizing MFA would help ensure that should a threat actor manage to obtain admin credentials, authentication would not be possible.
- No Mailbox Auditing – Customers who setup their Office 365 instance prior to January 2019 have this disabled by default. Auditing would log all actions performed in mailboxes, providing security teams with visibility into potential threat actions.
- AAD Password Sync – Enabled by default, on-prem AD accounts are matched and sync’d with Azure AD-based Office 365 accounts. Should an admin account be compromised on-prem, the enabled password sync would overwrite the password to the equivalent Office 365 account, allows an attacker to shift focus to Office 365. Microsoft has disabled this for admin accounts in late 2018, but some orgs may still have online and on-prem admin accounts matched.
- Insecure Legacy Authentication Protocols – Organizations using POP3 and SMTP to access corporate email are using legacy protocols to authenticate, potentially exposing credentials. Either disable these protocols or use Azure AD Conditional Access policies will limit their use.
Attacks on Office 365 users are a staple in the cybercriminals arsenal. With a set of credentials, a wide range of subsequent attacks are possible, including fraud, phishing, ransomware, and data theft.
Because Office 365 accounts are a target, organizations should encourage their users to be constantly vigilant using Security Awareness Training. Even if emails are coming from the inside, users need to be taught to scrutinize one-of band requests to open attachments, click links, etc.
Free Phishing Security Test
Find out what percentage of your employees are Phish-prone™
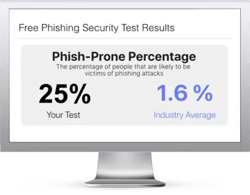 Would your users fall for phishing and other social engineering attacks? Take the first step now and find out before the bad guys do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
Would your users fall for phishing and other social engineering attacks? Take the first step now and find out before the bad guys do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
Here's how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





