
The two hospitals were hit by ransomware infections and are one of the largest data breaches reported by the U.S. Department of Health. This particular incident encrypted all kinds of sensitive data, including clinical and demographic data, and financial information including social security numbers.
The Bayamon Medical Center and the Puerto Rico Women and Children's hospital sought help to decrypt the records and stated that: "The Hospitals believe that the records were simply encrypted and there is currently no indication that the information itself has otherwise been used by any unauthorized individual".
The organizations decided to evaluate the security of their systems and staff will get additional security awareness training. It has not yet been released how the infection happened, which ransomware strain was used, or if any ransom has been paid.
The fact that they are using a third party to see if they can decrypt the files is an indication that their backups apparently failed, and that they are not initially thinking about paying the ransom.
Note that the U.S. Department of Health and Human Services has categorized this as a data breach that is under investigation.
Brand-New Ransomware Simulator Tool Now with Two New Ransomware Scenarios
The bad guys are continuing to evolve their approach to evading detection. That’s why we’ve updated our Ransomware Simulation tool “RanSim” to include two new ransomware scenarios! 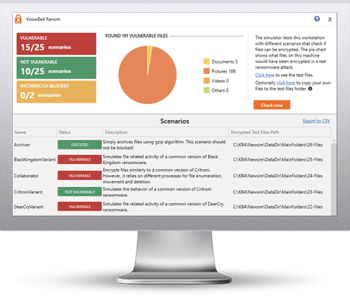
These new scenarios simulate ransomware strains like GandCrab and Rokku that encrypt users’ files and demands a crypto-ransom in exchange for the keys.
GandCrab was a very active ransomware strain all throughout 2018 as well as since the start of 2019, and it is known for requesting up to $3000 from its victims to decode encrypted files. While the creators of GandCrab announced in May they were shutting down their operation, make sure your organization is safe from this type of infection before another group takes it over, or worse, you won’t have an option to decrypt your system!
Try KnowBe4’s NEW Ransomware Simulator version and get a quick look at the effectiveness of your existing network protection against the latest threats. RanSim will simulate 15 ransomware infection scenarios and 1 cryptomining infection scenario to show you if a workstation is vulnerable to infection.
Here's how RanSim works:
- 100% harmless simulation of real ransomware and cryptomining infection scenarios
- Does not use any of your own files
- Tests 16 different types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
This is a complimentary tool and will take you 5 minutes max. RanSim may give you some insights about your endpoint security you never expected!
Don't like to click on redirected buttons? Copy & paste this link into your browser: https://www.knowbe4.com/ransomware-simulator





