 Michael Kan at CSO reported on a TrustWave blog post with some troublesome news: "Hotel and restaurant chains, beware. A notorious cybercriminal gang is tricking businesses into installing malware by calling their customer services representatives and convincing them to open malicious email attachments.
Michael Kan at CSO reported on a TrustWave blog post with some troublesome news: "Hotel and restaurant chains, beware. A notorious cybercriminal gang is tricking businesses into installing malware by calling their customer services representatives and convincing them to open malicious email attachments.
The culprits in these hacks, which are designed to steal customers’ credit card numbers, appear to be the Carbanak gang, a group that was blamed last year for stealing as much as $1 billion from various banks."
Brian Hussey, Trustwave’s global director of incident response, said that the bad guys are preying on the hospitality industry calling their customer service and pretending to be a customer who can’t access their online reservation system.
To infect the workstations with their malware, the hackers send an email to the customer service agent with an attached Word document claiming it has their reservation information. However, the Word doc is infected and when the support rep opens it up, it downloads malware to their workstation. According to Trustwave, most endpoint security software fails to detect the malware used in these hacks, not so surprising because antivirus is not that hard to circumvent.
The hackers are very persistent, Hussey said. “They’ll stay on the line with the customer service rep until they open up the attachment,” he said. “They have excellent English.” “Once this malware finds what it wants, it can steal every single credit card that passes through your servers,” Hussey said. “For a large restaurant chain, that can be a million customers over a period of time.”
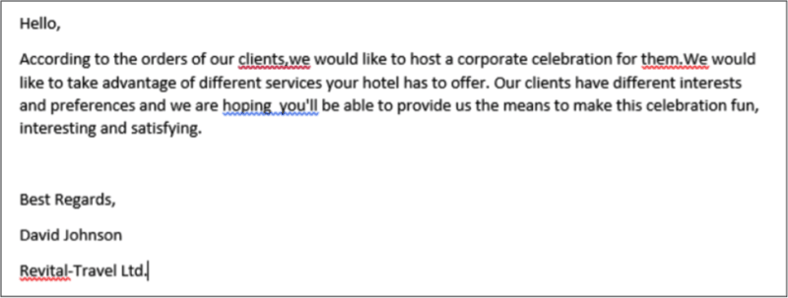
These bad guys have excellent social engineering skills. They research their targets on LinkedIn and find out the names of company department heads and drop those names during the call. The ultimate goal of the Carbarnak malware is to get into point-of-sale machines and steal all the credit card records.
In their blog post, TrustWave outlined the technical details of the malware and other indicators that you can use to find out if your network has been compromised.
You definitely want to step all your customer service staff through new-school security awareness training so that they do not fall for social engineering attacks like this.
Start with a free Phishing Security Test, and find out the Phish-prone percentage of your users.
Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://www.knowbe4.com/phishing-security-test-offer





