Danny Palmer at ZDNet reported: "A widespread phishing campaign is targeting executives across a number of industries with messages asking to reschedule a board meeting in an effort to steal logins and passwords.
Spotted by researchers at security firm GreatHorn, the phishing messages spoof the name and email address of the CEO of the company being targeted and uses a subject line including the company name and a note about the meeting to gain the attention of potential victims. Users are more likely to fall for attacks they believe to come from their boss.
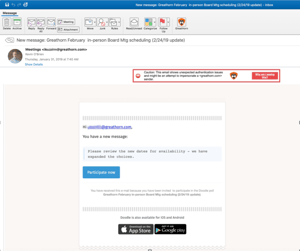
The contents of the phishing email is simple: it says a board meeting has been rescheduled and asks users to take part in a poll to choose a new date.
If users click the link, they're taken to a webpage which appears to be a login page for Microsoft Outlook and Office 365, but this is in fact a phishing site — any information entered into it will go directly into the hands of the attackers.
The attack is slightly different if the email is viewed on a mobile device — the display name is changed to 'Note to Self' but the contents of the message stays the same.
With the phishing email targeting high-level executives like CFOs, CTOs and SVPs, a successful attack could provide attackers with access to highly sensitive data across the corporate network — and the compromised accounts could also be used to help conduct further malicious campaigns.
The fake meeting phishing attack appears to be prolific — researchers at GreatHorn say it was found targeting one in seven of the firm's customers. In each case, the attackers were eliminated before damage could be done.
It's believed that the campaign is still active and that the phishing URL claiming to be windows related — is still up.
Users are therefore warned to be aware of the campaign and to be suspicious of any emails containing a subject line following a pattern of: New message: [Company Name] February in-person Board Mtg scheduling (2/24/19 update) Full article here:
Cross-posted with grateful acknowledgment to ZDNet.






