KnowBe4 customers run millions of phishing tests per year, and we report quarterly on the latest top-clicked phishing email subjects in 3 separate categories: subjects related to social media, general emails and 'In The Wild' attacks that we received from our customers by employees clicking the Phish Alert Button on real phishing emails and sending the email to us for analysis.
We want our customers to always know what the most current high-risk phishing templates look like and why users fall for them. That way they can keep up with current threats and innoculate their last line of defense, their users, against social engineering attacks. The Q3 2017 results were a mix of personal and company notifications, showing email continues to be an effective way to phish users.
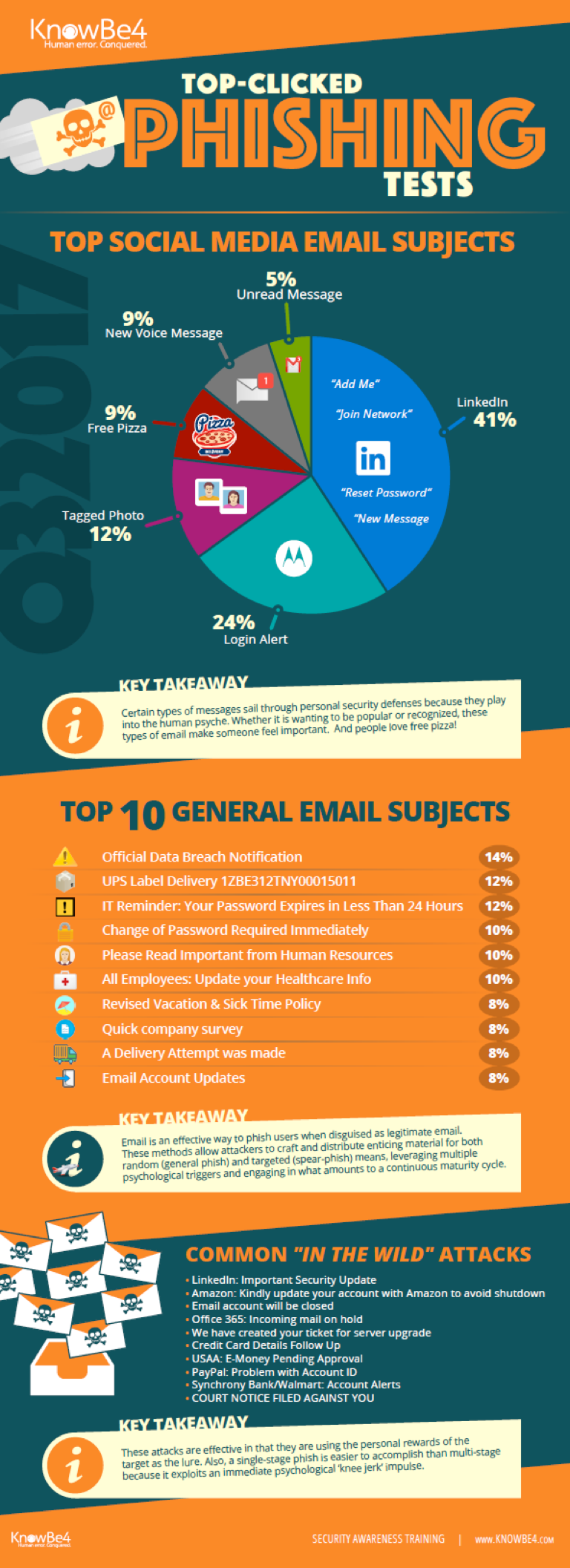
The Top 10 Most-Clicked General Email Subject Lines Globally for Q3 2017 include:
- Official Data Breach Notification – 14%
- UPS Label Delivery 1ZBE312TNY00015011 – 12%
- IT Reminder: Your Password Expires in Less Than 24 Hours – 12%
- Change of Password Required Immediately – 10%
- Please Read Important from Human Resources – 10%
- All Employees: Update your Healthcare Info – 10%
- Revised Vacation & Sick Time Policy – 8%
- Quick company survey – 8%
- A Delivery Attempt was made – 8%
- Email Account Updates – 8%
How Can This Help My Organization?
Armed with this data, KnowBe4 customers can set up phishing campaigns using templates related to these subjects to strengthen their human firewall. We recommend starting with 1- and 2-star level tests --these are easier to spot -- and over a 12-month period increase the difficulty level to 4- and 5-star templates which are much harder to identify.
You can even target specific groups, departments, and/or individuals with phish of differing maturity levels. That can allow security leaders to inject training at a maturity level that is most likely to help each group – and it also allows for some gamification.
Phishing Emails Remain the #1 Infection Vector
According to Osterman Research, email has been the number one infection vector since 2014. It’s an effective method because it gives attackers more control than simply placing traps on the web and hoping that people will fall for them. Instead, attackers craft and distribute enticing material using both random and targeted means. This method gives the cybercriminals greater control in selecting potential victims, leveraging multiple psychological triggers and engaging in what amounts to a continuous maturity cycle.
 Here's how it works:
Here's how it works:




