By Eric Howes, KnowBe4 Principal Lab Researcher.
A few days ago our friends at BleepingComputer.com announced the discovery of a new form of ransomware, which they dubbed Jigsaw Ransomware. Apparently some of the bad guys decided that simply taking files hostage via crypto-ransomware was not enough to sufficiently motivate victims to cough up the demanded ransom (which is $150 USD -- 0.4 Bitcoins -- in the case of this new ransomware strain). No, they're not just taking hostages these days. They're now shooting them as well.
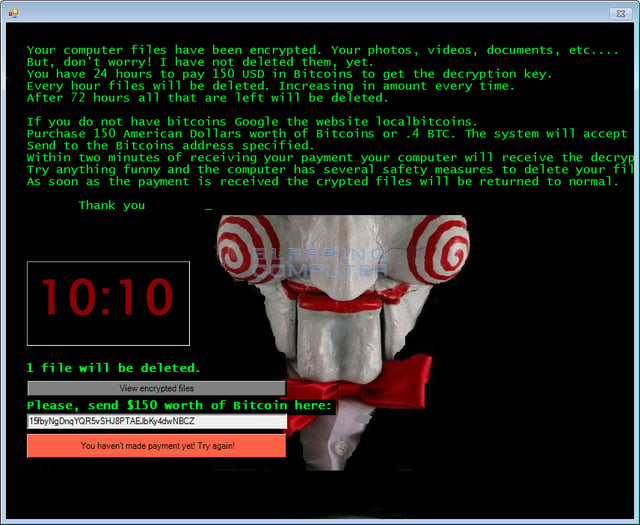
As Larry Abrams explains: "It is not the first time that we have seen ransomware threaten to delete files, but this is the first time that one has actually carried out its threats. The Jigsaw Ransomware deletes files every 60 minutes and when the program is restarted. Every hour, the Jigsaw Ransomware will delete a file on your computer and increment a counter. Over time this counter will cause more than one file to be deleted every hour.
"More destructive, though, is the amount of files that are deleted every time the ransomware starts. After the initial infection, when the ransomware it restarted, whether that be from a reboot or terminating the process, Jigsaw will delete a thousand, yes a thousand, files from the victim's computer."
Jigsaw targets 226 different file types, appending the .FUN, .BTC, and .KKK extensions to files it takes hostage via the AES encryption algorithm.
Decryption Tool Available
The good news, however, is that the team at BleepingComputer (which includes DemonSlay335 and folks from MalwareHunterTeam) developed a process for decrypting files that have been encrypted by Jigsaw. They even offer a free tool to perform the decryption, which you can find, along with instructions, at BleepingComputer.com.
Given that this ransomware variant deletes files, though, it is imperative that users take action as quickly as possible following the encryption process. That means terminating the two Jigsaw processes (firefox.exe & drpbx.exe) in Task Manager and using MsConfig to remove the auto-run entry for firefox.exe in the Registry. Once users have safely disabled Jigsaw they can use the decryption tool available above from BleepingComputer.com.
Know Your Enemy
Jigsaw isn't the first ransomware variety for which malware researchers have built decryption tools. Not all ransomware variants can be thwarted by community-built decryption tools, but many can. To take advantage of these tools, though, you need to know what ransomware variant you're dealing with.
DemonSlay335 (aka Michael Gillespie) now has a, ID Ransomware web site to assist ransomware victims. It allows users to upload sample files (either the "ransom note" that typically accompanies a ransomware infestation or files that have been encrypted by ransomware). The web site then identifies the ransomware variant and points users to decryption tools that might be available for the involved ransomware variant.
Again, not all ransomware variants are vulnerable to community-developed decryption tools. In many cases your only options may be to pay the ransom to recover your files, restore files from backup (if you have backups), or refuse to pay the ransom and suffer the consequences.
That said, ID Ransomware should probably be your first stop if you've been hit with a ransomware infestation.
Ransomware Hostage Rescue Manual
Get the most complete Ransomware Manual packed with actionable info that you need to have to prevent infections, and what to do when you are hit with ransomware. Get The Manual.





