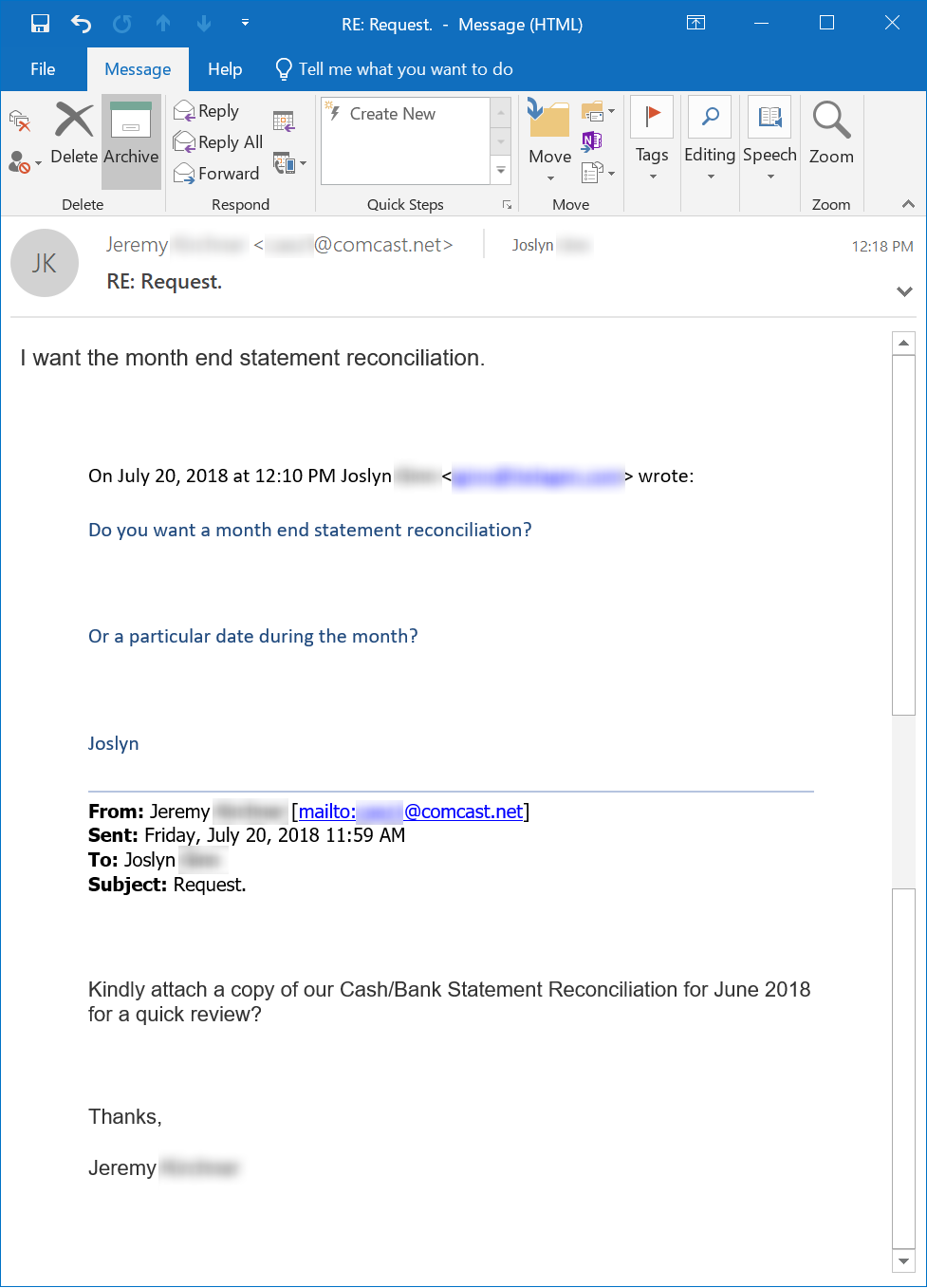
So, here's a new CEO Fraud phish: see these fresh screen shots from emails reported to us through the free KnowBe4 Phish Alert Button. Bad guys spoof the managing partner and CPA and an accounting & consulting firm and ask an employee for the "Cash/Bank Statement Reconciliation" for June of this year.

Now, it's not immediately clear what the bad guys could do with the data from such a statement, but this may simply be a first step of a one-two punch that is meant to establish credibility. The next step would be a malicious request for salary payment records like a pay stub that allow the bad guys to change bank accounts for direct deposit salary payment to accounts they control.
Here is another variant, where the employee seems to be willing to comply:
And here is another variant
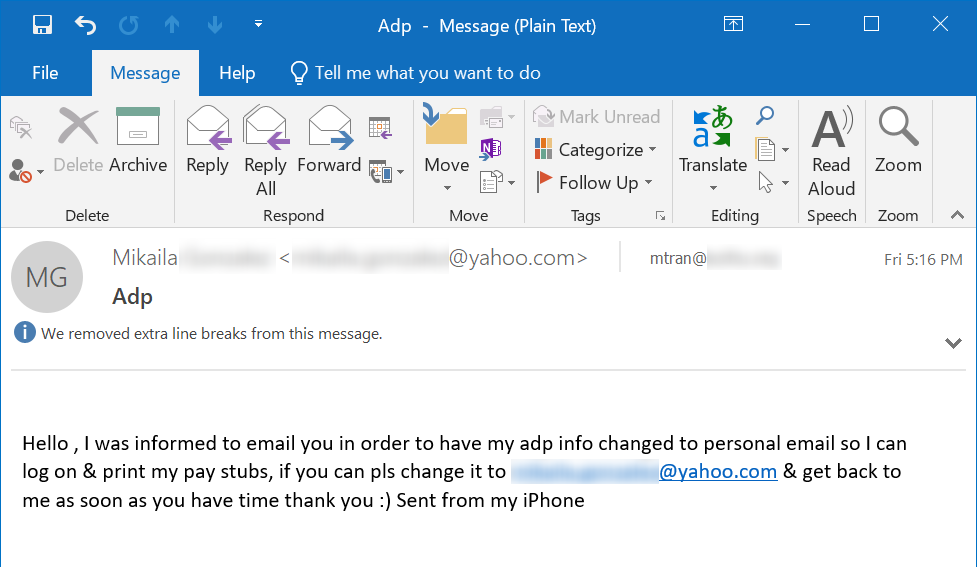
See the payroll phish screenshot, which asks an employee at a credit union to change the email associated with another employee's ADP account to a non-company email address.
Of course, ADP already allows employees to do this on their own: http://www2.ccga.edu/Faculty/
- The bad guys didn't bother spoofing the targeted employee's corporate email address. They used the same address submitted as a substitute.
- The targeted employee doesn't appear to be very senior in the organization. So, this might be some kind of initial test to see if the scheme works.
I suggest you send the following to your employees in accounting specifically. You're welcome to copy, paste, and/or edit:
The bad guys are getting very creative with payroll scams, which can be done through the whole year instead of just during the tax season. They are now impersonating an executive and ask for financial reports like Cash/Bank statement reconciliation, or they ask employees in payroll to make changes to either bank accounts or the email address that controls making edits to the account. In these last two cases this allows them to get money sent to an account they control. Make very sure that any request related to financial or payroll records comes from the right person and grab the phone and give them a call to make sure the change request is legit. Think Before You Click!
Watch out for these new types of CEO fraud, and train your accounting team to not fall for spoofed social engineering attacks like this. Install the free phish alert button on their machine so they can report incidents like this.
Free Phish Alert Button
When new spear phishing campaigns hit your organization, it is vital that IT staff be alerted immediately. One of the easiest ways to convert your employees from potential targets and victims into allies and partners in the fight against cybercrime is to roll out KnowBe4's free Phish Alert Button to your employees' desktops. Once installed, the Phish Alert Button allows your users on the front lines to sound the alarm when suspicious and potentially dangerous phishing emails slip past the other layers of protection your organization relies on to keep the bad guys at bay.

Don't like to click on redirected links? Cut & Paste this link in your browser:




