 Micropayments company Coil accidentally exposed at least a thousand of its customers’ email addresses by including their addresses in the “To” field of an email, BleepingComputer reports. The email in question concerned updates to the company’s privacy policy (many observers have noted the irony). It’s not clear how many email addresses were exposed, but BleepingComputer suspects it was more than a thousand.
Micropayments company Coil accidentally exposed at least a thousand of its customers’ email addresses by including their addresses in the “To” field of an email, BleepingComputer reports. The email in question concerned updates to the company’s privacy policy (many observers have noted the irony). It’s not clear how many email addresses were exposed, but BleepingComputer suspects it was more than a thousand.
“On taking a closer look, BleepingComputer noticed at least 1,000 emails were included in the announcement,” the publication says. “It is likely other users saw a different set of email addresses listed in the To or CC fields, assuming the mass announcement was emailed in batches of 1,000.”
Coil’s founder and CEO Stefan Thomas apologized in a statement, saying the incident was caused by human error.
“Earlier this evening we sent you an email updating you on changes to our Terms & Privacy Policy,” Thomas said. “Unfortunately, due to a human error related to how we interface with our mailing list provider, a number of users' email addresses were populated alongside yours. This mistake is especially painful as we take privacy extremely seriously -- it is the cornerstone of our values. We’re deeply sorry and hope you can forgive us for this mistake. We’re here to help you with any concerns or issues you may have as a result of this error.”
BleepingComputer notes that these types of privacy breaches are fairly common, with at least two other incidents occurring in the past few weeks.
“Last week, Rakuten had erroneously emailed multiple customers, stating the customers had earned cashback, only to recall their words later,” BleepingComputer says. “In October, a Home Depot email blunder had exposed hundreds of customer orders and personal information to strangers CC'd in emails.”
It’s not just the incoming mail that can be a problem. The outgoing mail carries its own risks. New-school security awareness training can reduce the risk of both malicious and accidental incidents by teaching your employees to be vigilant when dealing with emails and other forms of communication.
BleepingComputer has the story.
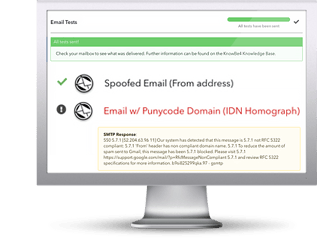 Here's how MSA works:
Here's how MSA works:




