Yesterday, April 25 2016, we encountered a new phishing email being delivered through Zendesk.
The credentials phish itself is a straightforward social engineering attack. The email body tells your employee that someone named John is sending them a file through a file-sharing service called ShareFilz. Users who click the supplied download link are taken to spoofed Google Docs login page hosted on the domain sharefilzs.com. The user's email address is prepopulated in the login form, and any password will be accepted.
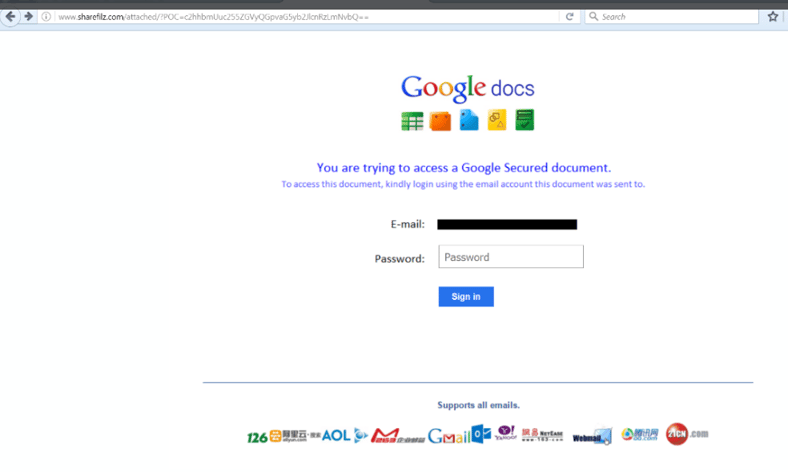
Users who proceed with the bogus sign-in are then redirected to a PDF document hosted on another site -- an attempt by the bad guys to distract users from noticing that they have effectively given out the login credentials to their personal or work email account.
We are giving you a heads-up about this phish since it's being delivered through Zendesk, as revealed by the email headers. Apparently the bad guys are able to a Zendesk account (sharefilzs.zendesk.com, which may be a trial account) and are using it to distribute this particular phish.
Do you have Zendesk whitelisted?
Given that Zendesk is a well-known, legitimate customer service platform, it's a good bet that you will have have Zendesk whitelisted, allowing this phish to pass through all your email security applications, services, and appliances.
The domain sharefilz.com, used to host the bogus Google Docs login page, was registered April 25 through an anonymizing domain registration service (Whois Privacy Corp.).
The RED FLAG in this case?
Users should be tipped off that something is very wrong once they hit a web page purporting to be a Google Docs login page on an unfamiliar web site (sharefilz.com).
[UPDATE] The rogue Zendesk account has been suspended. Additionally, all three major browsers (Chrome, Firefox, IE/Edge) are now throwing block pages on the URL. So, Zendesk is obviously aware of that rogue account being used for phishing.
This type of phishing attack, where an existing potentially trusted domain is used as an attack vector, is another very good reason for effective security awareness training. Get a one-on-one web demo and see how easy it is to train and phish your users.
PS: If you do not like to click on buttons with redirects, here is a link you can cut&paste in your browser:
https://info.knowbe4.com/kmsat-request-a-demo
Related Pages: Phishing





