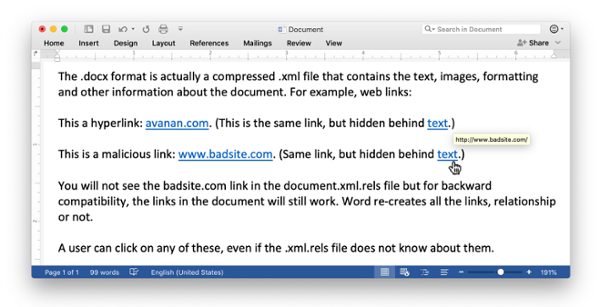
Attackers are bypassing Office 365 email attachment security by editing the relationship files that are included with Office documents, according to Yoav Nathaniel at Avanan.
A relationship file is an XML file that contains a list of essential components in the document, such as font tables, settings, and external links. A number of popular email filters, including Microsoft’s Exchange Online Protection (EOP), only scan the links contained in the relationship file, rather than scanning the entire document. Attackers can remove the links from a document’s relationship file, but they will still be active in the actual document.
Nathaniel compares the relationship file to the index of a book. “Sometimes, key terms might not be included in the index, but they are still in the book,” he says. “In this attack, hackers deleted the external links from the relationship file to bypass link parsers that only read the index rather than the ‘book.’”
When a user opens the document after it’s passed the security scan, the Office application will recreate all the hyperlinks that were deleted from the relationship file, making them clickable again.
The “NoRelationship attack,” as Avanan has dubbed it, demonstrates why employees can’t rely solely on technical defenses to keep them safe. People need to be suspicious of any email attachments, because attackers will always find new ways to get around security mechanisms.
New-school security awareness training can help your employees stay safe when malicious emails end up in their inboxes. Avanan has the story:
https://www.avanan.com/resources/the-norelationship-attack-bypasses-office-365






