 Originally seen all the way back in 2008, this banking trojan is continuously being developed. Its latest iteration is downright nasty and has already infected 5% of all organizations worldwide.
Originally seen all the way back in 2008, this banking trojan is continuously being developed. Its latest iteration is downright nasty and has already infected 5% of all organizations worldwide.
Bad guys today generally have two goals with every infection. First, infect the targeted endpoint to begin the work of whatever malicious threat action (e.g. ransomware, remote access, etc.) needs to come next. Second, they want to use that compromised making as the launchpad for an attack on other organizations.
The latest version of Qbot does both is such a sinister way, it’s a bit scary.
According to new research from Checkpoint, Qbot contains a number of collector modules. One is used to harvest browsing data, email records, and banking credentials. Another uses mimikatz to scrape RAM for credentials. And still another new module seen by Checkpoint, extracts specific email threads related to tax payments, job recruitment, and COVID-19 from the endpoint’s Outlook client, uploading them to the attacker's command-and-control (C2) server.
The email threads are used to hijack the conversation where the cybercriminals send emails impersonating the compromised email account’s owner, providing malicious attachments and links in an effort to increase their reach into other organizations.
Qbot is no joke; it’s a very powerful tool that’s definitely in the wrong hands.
Organizations need to protect themselves with a layered security strategy that includes Security Awareness Training to empower users with knowledge of phishing attack methods, social engineering tactics, and how to keep from falling for these very prevalent attacks.
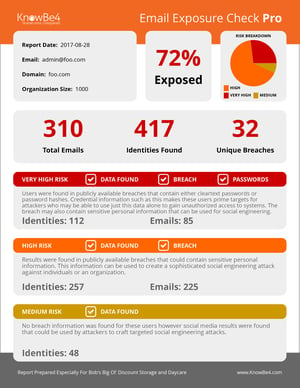 Here's how it works:
Here's how it works:




