 Scammers use realistic-looking emails and a well-designed website under the guise of the Paycheck Protection Program to trick victims into providing banking credentials.
Scammers use realistic-looking emails and a well-designed website under the guise of the Paycheck Protection Program to trick victims into providing banking credentials.
Everyone in the U.S. who can get some financial assistance during this pandemic is sufficiently motivated to take advantage of legitimate government programs designed to help. But one campaign was identified by anti-phishing vendor Inky that included such a realistic user experience that they even were complimentary about its’ execution.
The scam starts with an email from the “Federal Reserve” promising stimulus payments:
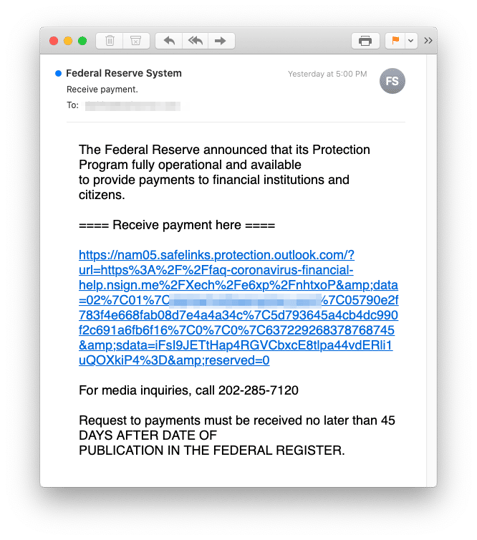
Victims who click the link are taken to a website that leverages FEMA and CDC logos to establish credibility.

Should they click on the “Get Economic Impact Payment” button, they are presented with a list of banks, and a subsequent opportunity to provide their banking credentials. Regardless of the data entered, the victim is told there’s a problem with the credentials provided (and the bad guy gets a copy).
It’s a classic recipe: start with a sense of urgency (financial need), add in an ability to address the issue (receive stimulus money), include some credibility builders (the government logos), and ask for details that seem to be relevant to the process (banking details), and you have yourself a successful phishing scam.
Organizations can help their users with Security Awareness Training that educates them about phishing scams, as this same recipe is used time and time again to scam employees into giving up online credentials, committing fraud, infecting endpoints, and providing sensitive corporate information.
 Here's how it works:
Here's how it works:




