 Since releasing its free PhishAlert button in November 2015, KnowBe4 has been receiving a steady stream of emails flagged by users as potential phishing attacks. The email threats reported by users have ranged from the mundane to the extremely alarming, and we'd like to share with readers some of what we've seen.
Since releasing its free PhishAlert button in November 2015, KnowBe4 has been receiving a steady stream of emails flagged by users as potential phishing attacks. The email threats reported by users have ranged from the mundane to the extremely alarming, and we'd like to share with readers some of what we've seen.
The PhishAlert button, available as a free download here, is a Outlook plugin that allows users to report email threats to their internal IT and security response departments with a single click. Companies and organizations who deploy the PhishAlert to their users' desktops have the option to share those reported email threats with KnowBe4, and much of what we've received has been eye-opening, to say the least.
Before diving into the details, it's important to note that the PhishAlert Outlook plugin typically sits behind a range of other network security devices, Exchange protection services, and anti-virus software programs that organizations have in place to filter incoming email and prevent email-borne threats from landing in the inboxes of their employees and users. In other words, the email threats that we're seeing reported by users are threats that slipped through all those other layers of protection, making the individual user or employee the last line of defense.
So what have users been encountering in their inboxes and flagging as phishing threats? To no one's surprise, a large percentage are phishing attacks that trick users into coughing up secure credentials to online services or their own organization's internal network. Plenty of others lead to exploits that use trojan downloaders to drop ransomware, backdoor trojans, and other malicious software that could do a great deal of damage to companies and organizations from inside their networks.
One particular threat, though, has caught our attention: the JSocket remote access trojan (RAT), which has shown up in a number of reported emails as a .JAR file attachment. JSocket is an extremely dangerous, Java-based, cross-platform RAT with advanced features. You can read a more detailed description of JSocket in this write-up from Fidelis Security. Here's a brief summary of the key facts. (We'll focus on the PC version of JSocket, as that's what we've seen, though Android versions exist as well.) JSocket is a subscription-based RAT that is actively maintained and regularly updated by its developer to resist reverse engineering and thwart detection/removal by anti-malware applications.
Here's a brief summary of the key facts. (We'll focus on the PC version of JSocket, as that's what we've seen, though Android versions exist as well.) JSocket is a subscription-based RAT that is actively maintained and regularly updated by its developer to resist reverse engineering and thwart detection/removal by anti-malware applications.
The latest in an established line of RATs like AlienSpy and AdWind, JSocket contains advanced features that allow malicious actors to take remote control of PCs inside protected networks, execute malware on compromised endpoints, and exfiltrate sensitive data from inside otherwise secure companies and organizations. Needless to say, any company or organization with an endpoint compromised by JSocket operating inside its network is facing a potential disaster.
As the distribution of JSocket is subscription-based, numerous threat actors are using JSocket in active malware campaigns. Fidelis reports over 2,000 known Jsocket variants "in the wild" being used by "hundreds of operators." While the majority of these operators' campaigns appear to be targeted at financial institutions, known targets of JSocket campaigns span a range of industries. And the targets are not just large enterprises. JSocket campaigns are going after SMB targets as well.
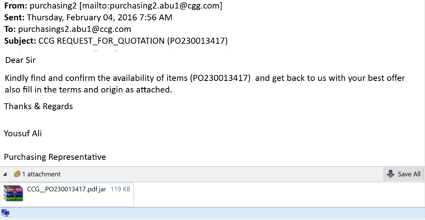
The phishing emails we've seen use social engineering hooks in the email body to trick users into opening an attached .JAR file. These social engineering hooks are often specifically tailored to the target's business or industry. Accounting firms, for example, might receive phishing emails that purport to deliver W-2 forms or other financial data. Healthcare organizations might receive .JAR file attachments that are advertised as patient data or other medical forms.
If hoodwinked users click those .JAR file attachments and Oracle's Java JRE happens to be installed on their PCs, the RAT quickly burrows in to the compromised machine and establishes a secure connection to a command and control (C&C) server (which often resides on a ddns.net subdomain).
Anti-virus coverage of the JSocket variants we've seen ranges from spotty at best (5 or 6 out of 50 plus anti-virus scanners on VirusTotal) to almost non-existent. Because JSocket boasts advanced features that allow it to shut down and defeat anti-malware applications, any anti-virus on a box compromised with JSocket will likely be taken out of action, leaving external, malicious actors with complete control of a machine inside the network.
Alarmed? We certainly were, given that emails reported to us came from users who found these JSocket-armed phishes sitting in their inboxes after those emails slipped past one or more other layers of protection within their organizations. In such situations, it is critical that end users be vigilant in spotting potential threats and reporting them to their organization's IT department.
You get get your own free Phish Alert button and deploy it to your users. Click the button and learn more:





