 Steve Ranger at TechRepublic did a good job summarizing the direction of future threats we are going to have to deal with.
Steve Ranger at TechRepublic did a good job summarizing the direction of future threats we are going to have to deal with.
"After at least a dozen years in the shadows, cyberwarfare is gradually emerging into daylight. While cyber weapons were mostly developed and used by intelligence agencies as part of secret missions, they are now becoming an acknowledged military option during conflicts.
Here are predictions about how cyberwarfare will evolve over the next year. PS: You can download the Bad Rabbit in poster format at our resources section.
The cyber arms race will accelerate
Having a cyberwarfare capability is the latest must-have for many nation states, which has sparked a cyber arms race that shows no sign of slowing down. NATO, for example, recently updated its strategy to include the potential use of cyber weapons alongside traditional munitions.
Cyber weapons will become a standard feature of warfare
As NATO secretary general Jens Stoltenberg said recently, noting the use of cyber weapons against ISIS in Iraq and Syria: "in any military conflict, cyber will be an integrated part."
The actual type and sophistication of the attacks deployed will vary; an opponent with little in the way of tech to disrupt will require a different set of options to one with a sophisticated infrastructure to defend. Cyberspace is now considered just another part of the battlefield.
Stealthy cyberwar preparations will continue
There will be no let up for energy companies, high tech manufacturers and government agencies; state-backed hackers (from many nations) will continue to poke and pry at their systems, looking for access to those all-important industrial control systems, which could be used to cause chaos at a later date.
Weaponised ransomware will be your next big headache
Ransomware has been at the heart of some of the biggest security stories of this year, and it will be the same in 2018. But the motivation of ransomware users is shifting in an even more dangerous direction. Up until now most ransomware has been used to extract a ransom (usually in all-but-untraceable Bitcoin) from those unlucky enough to be hit with it.
That's bad enough: there's already a trend towards using ransomware as a weapon, where devices are encrypted, rendering data inaccessible, and the perpetrators don't offer a key. It's not hard to see this weaponised ransomware being utilised—perhaps by hackers loosely aligned with a nation-state—to cause problems for rivals. The only problem is that these kinds of attacks can rapidly spiral out of control: even if you aren't the intended victim you might still get hit.
The IoT will be a cyberwar and cyber espionage gold mine
Unsecured Internet of Things devices (like webcams and routers) have already press-ganged into a botnet - Mirai - which was then used to carry out Distributed Denial of Service attacks against websites. But because that secret double life didn't really affect the day-to-day performance of these gadgets, owners probably barely noticed (and likely cared even less). But it's easy to imagine a situation where the growing armada of IoT devices could be used against us, too.
Failure to patch will be the cause of another giant security disaster
Everyone gets very excited about zero-day exploits; previously undiscovered holes in software that can be used to attack systems and against which there is no defense. Stuxnet used at least four different ones.
Unless you are being specifically targeted (in which case, good luck) having the basics of security in place will be enough to make state-backed hackers go and find an easier target. Full article with more detail here.
Here Are 8 Ways To BECOME A HARD TARGET (apart from having weapons-grade backups and religious patching of both OS and 3rd party apps)
- From here on out with any ransomware infection, nuke the machine from orbit and re-image from bare metal, you do not know what the bad guys left behind
- If you have no Secure Email Gateway and Web Gateways that cover URL filtering and make sure they are tuned correctly
- Make sure your endpoints are patched religiously, and that means OS and 3rd Party Apps, test the Flexera Personal Software Inspector on your workstation.
- Make sure your endpoints and web-gateway have next-gen, frequently updated (a few hours or shorter) security layers
- Identify users that handle sensitive information and enforce some form of higher-trust authentication (like 2FA)
- Review your internal security Policies and Procedures, specifically related to financial transactions to prevent CEO Fraud
- Check your firewall configuration and make sure no criminal network traffic is allowed out
- Leverage new-school security awareness training, which includes social engineering via multiple channels, not just email
BONUS: Work on your security budget to show it is increasingly based on measurable risk reduction, and try to eliminate overspending on point-solutions targeted at one threat-or-another.
Gartner recommends to take some of the money you’re spending on prevention and start to drive it toward more detection and response. As a defender you need to be right 100% of the time, as an attacker you only need to be right once. A dedicated bad actor who is after something in your enterprise is going to get it, even if they use the weakest link–people–to do so. This means adapting your security setup to focus on detection, response, and remediation. That’s where the cybersecurity fight is today. In the future it will most likely move to prediction of what’s coming before anything happens.
Additionally, DevOps should become DevSecOps, with a focus on security. This is a good time to marry development and operations. The time to market has shortened so much, it creates an endless connection between development and operation, which means it’s important to stop running them as isolated units. This is the time to bring security to DevOps, or if the team is not internal, to ask the service provider what kind of security they provide.
Does *Your* Antivirus block the latest Ransomware Strains?
How vulnerable is your network against ransomware attacks??
KnowBe4 has been working hard on something brand new! Bad guys are constantly coming out with new versions of ransomware strains to evade detection. Is your network effective in blocking ransomware when employees fall for social engineering attacks?
KnowBe4’s Ransomware Simulator "RanSim" gives you a quick look at the effectiveness of your existing network protection.
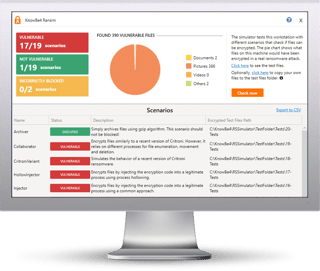 Here's how RanSim works:
Here's how RanSim works:
![]() 100% harmless simulation of a real ransomware infection
100% harmless simulation of a real ransomware infection
![]() Does not use any of your own files
Does not use any of your own files
![]() Tests 10 types of infection scenarios
Tests 10 types of infection scenarios
![]() Just download the install and run it
Just download the install and run it
![]() Results in a few minutes!
Results in a few minutes!
RanSim has been downloaded thousands of times and run against dozens of AV products. The results have been an eye opening experience for many IT pros. NOTE: RanSim was created for Windows-based workstations running Windows 7 or higher.
Download RanSim Now
Don't like to click on redirected buttons? Cut & Paste this link in your browser:





