 If I were to ask you to picture in your mind a shady criminal organisation consisting of cyber mercenaries, ones that took money from clients, asked no questions, and over the period of seven years spied on over 10,000 email accounts, what would they look like?
If I were to ask you to picture in your mind a shady criminal organisation consisting of cyber mercenaries, ones that took money from clients, asked no questions, and over the period of seven years spied on over 10,000 email accounts, what would they look like?
This digital new-age version of Pablo Escobar, trading electronic information as opposed to cocaine would likely be operating with military efficiency. Row after row of hardened criminal, reverse engineering code to implant malware, creating zero days to infect organisations.
But what if I told you that the reality was more akin to a few ordinary people working above a tea shop in India? That is precisely what happened when researchers at Citizen Lab spent more than two years mapping out a hack-for-hire operation arriving at the conclusion that New Delhi-based BelltroX was behind a hacking spree which targeted government officials in Europe, gambling tycoons in the Bahamas, and well-known investors in the U.S., including private equity giant KKR and short seller Muddy Waters.
Fortune 100 Vs Tea Shops
The whole scenario does beg the question: how do a few people, halfway across the world, working above a tea shop, gain so much influence? The impact of any small organisation, or even an individual can be just as powerful as a Fortune 100 company.
Ben Thompson illustrates this concept in his post Never-ending Niches where he explains how traditional media outlets compete to be more timely and have greater reach.
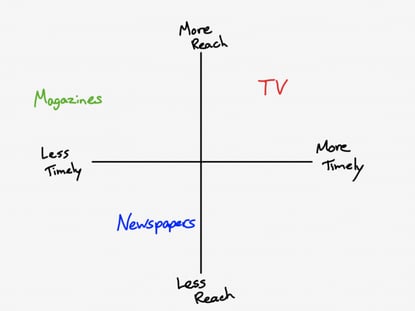
(credit Ben Thompson, Stratechery.com)
However, with the advent of the internet, the trade-off between reach and time is eliminated, regardless of the size of organisation.
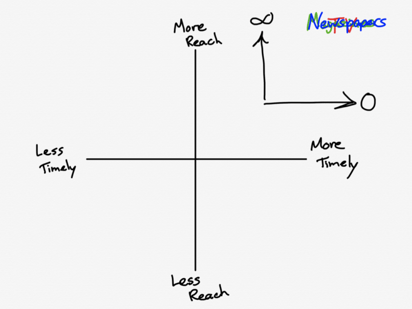
(credit Ben Thompson, Stratechery.com)
The other thing to consider, especially when it comes to hacking services, is that most of these operators don’t necessarily need particularly skilled hackers. Instead, the vast majority of attacks are predominantly phishing or spear phishing emails, which are used to compromise victims.
This is why even an individual can, from anywhere in the world, set up a cyber crime organisation with all the bells and whistles -- virtually indistinguishable from a legit global organisation.
Legit or Not?
In 2015, two U.S. private investigators admitted paying BelltroX to hack the accounts of marketing executives. But BelltroX isn’t the only player in town; and according to a Reuters investigation, private investigators in the U.S. have received unsolicited advertisements for hacking services out of India.
And while BelltroX’s hack-for-hire services may be clearly shady to anyone wanting to take a look, the line between legitimate and illegitimate services is not always clear.
Recent investigations by FireEye uncovered that the notorious FIN7 cyber criminal organisation created a front company called Combi Security. It bills itself as a pen testing company based in Moscow, Russia and Haifa, Israel. They hired skilled individuals and told them they would be involved in legitimate pen testing of client computer networks, making it a twister security employment version of a kind of money mule scam.
There was also recently the case of an Italian company called CloudEyE, which is believed to have made more than $500,000 from selling its binary crypter to malware gangs. Following the report published by Check Point which exposed the company, it appears that CloudEyE has shut down.
Do Your Due Diligence
The global landscape continues to shift rapidly. Technology has acted as the catalyst and made it difficult for even the most forward-looking of organisations to predict what the future may hold.
What is clear though, is that it takes far fewer resources to set up any organisation, legit or otherwise, these days. The whole world is connected, and deals can be made in an instant.
Due diligence lies at the heart of the matter here. Whether you’re a potential victim who has received an unsolicited email from a cyber criminal, poking beneath the hood and pausing for a second can save you a lot of grief in the long run. Or if you’re looking for a security job and find an enticing offer from a security organisation you’ve never heard of, take a moment to look beyond the glossy website and see whether the organisation is legitimate or not. Finally, and probably most importantly, if you’re an organisation looking for a security provider, do your due diligence. Implement security awareness training, look at offices, look at incorporation documents, look at financial records -- it can be all too easy to end up being an unwitting accomplice to a crime.
 Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!
Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!




