Our friends at Bleepingcomputer had a great article written by Ionut Ilascu I think you will like: "While phishing continues to be the prevalent threat in malware-less email-based attacks, cybercriminals refine their methods by adding an impersonation component to increase the success rate against company employees.
Impersonation attacks, also known as CEO fraud and business email compromise (BEC), are somewhat targeted and require the threat actor to do some reconnaissance about the recipient or the company they work for. This method is more difficult to detect by traditional security solutions because it typically does not follow a pattern.
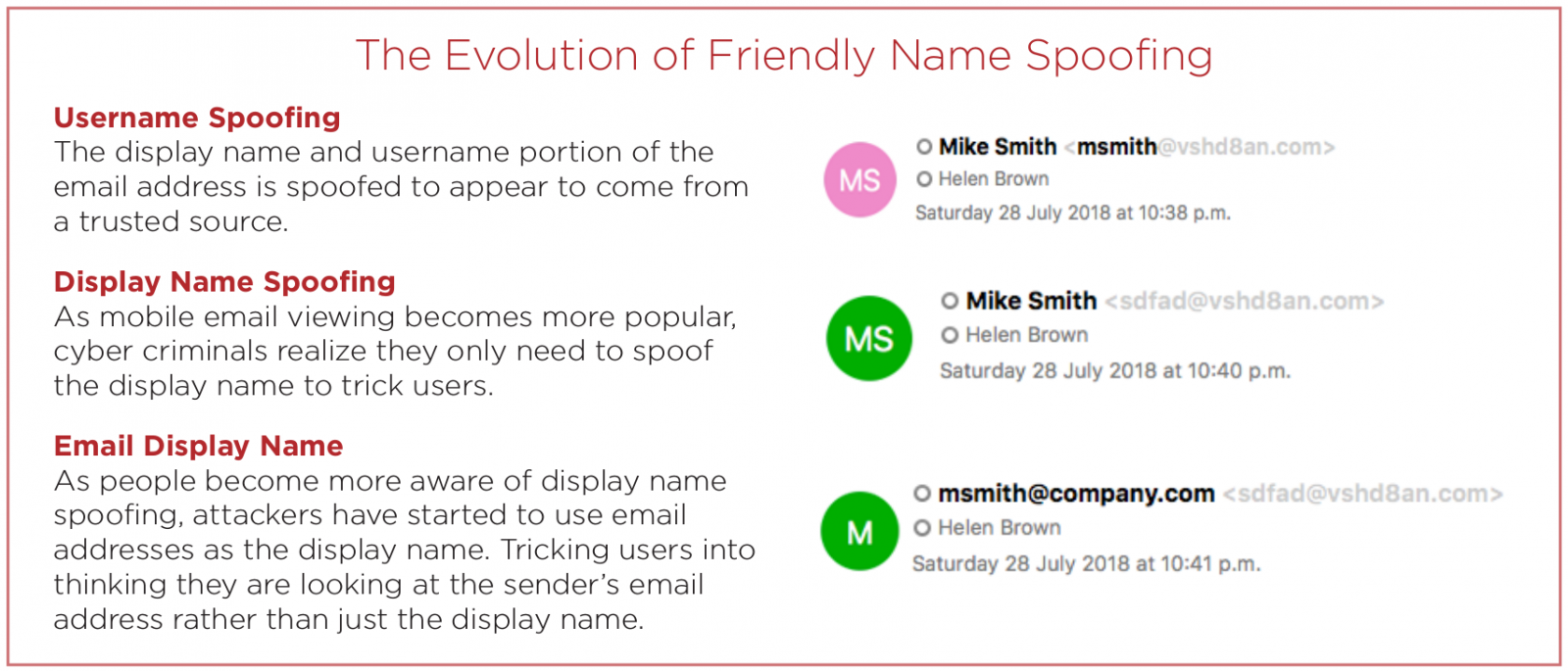
Spoofing the source name
Using impersonation to lead the company employees to a phishing site seems to be the most recent evolution step in malware-less email threats, according to the new Email Threat Report from FireEye, shared with BleepingComputer.
The end goal is the same as ever: trick the user into transferring money or disclosing information about the company that could lead to a more efficient attack.
"By including a phishing link in the impersonation email, cybercriminals realized they could send out a vaguer email to a larger amount of people while still seeing a similar open rate," the report details.

One technique cybercriminals use in impersonation attacks is to give the email address a name that is trusted by the victim. This detail may be the only one shown, so the source of the message will reveal the deception.
Another tactic that is usually combined with display name spoofing is to use an address with a friendly username that is trusted by the victim.
Other methods rely on tricking the eye by using domain names that look like a trusted source. Purchasing domains that are similar to the ones impersonated is a common strategy that is often used in phishing attacks.
"The emergence of impersonation attacks that lead to phishing sites is a prime example of how cybercriminals are constantly looking for the most efficient attack method," concludes FireEye's report.
FireEye observed these techniques used on their own or in combination. According to their statistics, there was an upward trend for friendly impersonation attacks between January and June.
The company analyzed over half a billion messages circulating in the first six months of the year and noticed that only 32% of them went through an inbox. The rest was blocked by security systems monitoring the content in the emails (attachment, URL, impersonation) and the origin (blacklisted IPs, known malicious domains) of the emails. Cross-posted with grateful acknowledgment to Bleepingcomputer.
Can *Your* Domain Be Spoofed?
One quick email from us to you shows if your email server is configured correctly. To enter just go here fill out the form, it's fast, easy and often a shocking discovery.
Warm regards,
Stu Sjouwerman
Founder and CEO, KnowBe4, Inc





