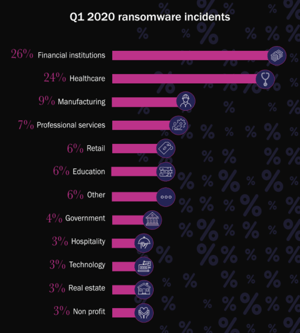
 Ransomware attacks continue to blight organizations of all sizes and sectors. The number of incidents involving ransomware reported to Beazley Breach Response (BBR) Services in the first quarter of 2020 increased by 25% compared to Q4 2019. While no industry was immune, manufacturing experienced the steepest increase of all – up 156% quarter on quarter.
Ransomware attacks continue to blight organizations of all sizes and sectors. The number of incidents involving ransomware reported to Beazley Breach Response (BBR) Services in the first quarter of 2020 increased by 25% compared to Q4 2019. While no industry was immune, manufacturing experienced the steepest increase of all – up 156% quarter on quarter.
As threat actors increasingly exploited ransomware, business email compromise (BEC) eased somewhat in Q1; down 16% from the previous quarter, although it remains a problem across all industries. While the financial services, healthcare and retail sectors reported fewer BEC incidents than in Q4, this may prove to be a temporary reprieve tied to behavioral changes amid the response to COVID-19. Employees first adjusting to working from home may have been less responsive to emails generally, and organizations may have been more focused on quickly ramping up remote working capacity than on identifying and reporting BEC incidents.
During the pandemic, attackers are taking advantage of the fact that many employees have been working from home,
without the technical protections that their corporate networks often provide. Furthermore, many employees are working from their personal computers, often shared with family members, processing sensitive and potentially personally identifiable information (PII) without the advantage of managed endpoint protection or even regular patching schedules that are also managed by the typical IT team. Many organizational policies are not designed to function in these distributed environments, leaving them less protected against wire transfer fraud and similar attacks.
Even social media is seeing a huge rise in pandemic-related scams. A very prolific one is where the bad actors set-up a
fake Facebook page to look like a legitimate company. Here they post that they will be giving a limited number of families one hour to shop for free in their store. All the person needs to do is like and share the post. The scammers start by posting these in local “For Sale” groups in cities using fake or hijacked accounts. Along with the post are instructions to follow a link to confirm their entry into the giveaway. This link is used to send the victim to a website hosting malware or a questionnaire that promises hundreds of dollars in coupons if they fill out a survey. One scam page had almost 5,500 followers after less than 14 hours of being created.
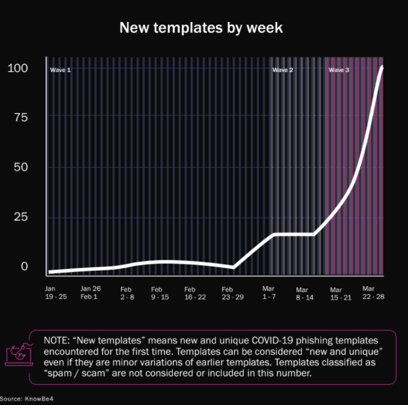
There are three waves of common scam templates:
1. Spoofs of authoritative sources of information such as the Centers for Disease Control and Prevention, World Health Organization and Department of Health & Human Services and company human resources departments, purportedly offering information and updates on the outbreak.
2. New and novel templates designed exclusively for COVID-19 that move beyond merely offering new information on the outbreak.
3. Repurposed older templates and social engineering schemes modified and updated to include a COVID-19 theme or angle.
As we move into the rest of the year, it's important to implement new-school security awareness training. Train employees on how to recognize common threats and scams and how to report any suspicious security incident.
Conduct phishing exercises periodically to enhance security awareness and prepare employees for responding to cyber attacks.
You can access the full report by Beazley Group here.
 Here's how it works:
Here's how it works:




