The Emotet botnet is up and running again after four months of inactivity, according to Ars Technica. Multiple security firms have reported seeing phishing emails delivering the malware via malicious Word documents.
The attackers are using improved social engineering techniques, with around a quarter of the emails being sent as replies to existing email threads.
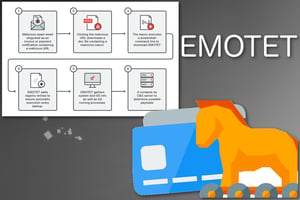
Emotet is a banking Trojan that spreads itself by accessing the email services of infected computers. It uses this access to send phishing emails to the victim’s contacts by replying to previous email threads, and sometimes adds the target’s name to the subject line of the email. This is an effective social engineering tactic, since the target sees the email coming from a trusted contact. It also helps the emails bypass security filters.
These emails contain Word documents purporting to be a “printer friendly version” of a new message. When a user opens the document to read their message, they’ll see what appears to be an alert from Microsoft telling them to accept a license agreement by clicking the “Enable Content” button. If someone clicks this button, their computer will be infected and incorporated into the botnet, and their own contact list will be targeted with phishing emails. The malware will also attempt to infect other devices on the network.
Emotet’s purpose isn’t just to infect other computers, however. The Trojan has become a malware-as-a-service platform that’s used by criminals to deliver additional malware to infected computers, and it’s often a precursor to ransomware attacks.
Emotet is one of the most dangerous threats facing organizations today, and its revival is noteworthy. Users should be particularly wary of the botnet’s tactic of replying to their email threads. New-school security awareness training can help your employees stay up-to-date on these types of threats so they know what to watch out for.
Ars Technica has the story: https://arstechnica.com/information-technology/2019/09/worlds-most-destructive-botnet-returns-with-stolen-passwords-and-email-in-tow/
 Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!
Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!




