 Brian Krebs wrote: "A number of Discord communities focused on cryptocurrency have been hacked this past month after their administrators were tricked into running malicious Javascript code disguised as a Web browser bookmark.
Brian Krebs wrote: "A number of Discord communities focused on cryptocurrency have been hacked this past month after their administrators were tricked into running malicious Javascript code disguised as a Web browser bookmark.
"According to interviews with victims, several of the attacks began with an interview request from someone posing as a reporter for a crypto-focused news outlet online. Those who take the bait are sent a link to a Discord server that appears to be the official Discord of the crypto news site, where they are asked to complete a verification step to validate their identity.
As shown in this Youtube video, the verification process involves dragging a button from the phony crypto news Discord server to the bookmarks bar in one’s Web browser. From there, the visitor is instructed to go back to discord.com and then click the new bookmark to complete the verification process.
However, the bookmark is actually a clever snippet of Javascript that quietly grabs the user’s Discord token and sends it to the scammer’s website. The attacker then loads the stolen token into their own browser session and (usually late at night after the admins are asleep) posts an announcement in the targeted Discord about an exclusive “airdrop,” “NFT mint event” or some other potential money making opportunity for the Discord members.
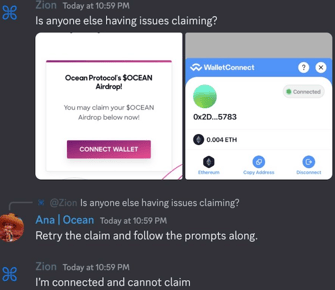
The unsuspecting Discord members click the link provided by the compromised administrator account, and are asked to connect their crypto wallet to the scammer’s site, where it asks for unlimited spend approvals on their tokens, and subsequently drains the balance of any valuable accounts.
Meanwhile, anyone in the compromised Discord channel who notices the scam and replies is banned, and their messages are deleted by the compromised admin account."
OUCH. Social engineering at its best.
First the interview requests, then clicking a malicious link, followed by a clicking on a "bookmark" that's really criminal Javascript bypassing their MFA. This is probably the North Koreans at work. They are very good at this. Here is the full Krebs article with the technical details:
https://krebsonsecurity.com/2023/05/discord-admins-hacked-by-malicious-bookmarks/
 Here's how it works:
Here's how it works:




